This week is all about a great feature that has been introduced with the latest service release of Microsoft Intune (2306). That feature is the ability to easily configure the Intune Management Extension as a managed installer on Windows devices. Until this new ability, it’s always been challenging to work with the Intune Management Extension in combination with Windows Defender Application Control (WDAC). The main challenge was to configure the Intune Management Extension as a managed installer, to simplify the acceptance of applications that were installed via that extension. With this new feature, it’s now possible to configure the Intune Management Extension as a managed installer, by using a tenant-wide configuration. So, that will take away any challenging configuration to configure a managed installer. This post will provide more details around the that tenant-wide configuration, followed with the steps to easily take advantage of that configuration. This post will finish with experiencing this WDAC configuration on a Windows device.
Note: Using the Intune Managed Extension as managed installer is supported on Windows 10 and Windows 11 Pro, Enterprise and Education. Jus make sure to run a supported version of the platform version and edition of choice.
Adding Intune Management Extension as managed installer
When looking at using WDAC with the Intune Management Extension, it all starts with adding the extension as a managed installer. That will make sure that apps that are installed via that extension are automatically tagged. That tag will make sure that those apps are automatically identified by the Application Control policies as safe apps that can be allowed to run on the device. The following four steps walk through the tenant-wide configuration for the managed installer.
- Open the Microsoft Intune admin center portal and navigate to Endpoint security > Application control
- On the Endpoint security | Application control page, on the Managed Installer tab, click Add
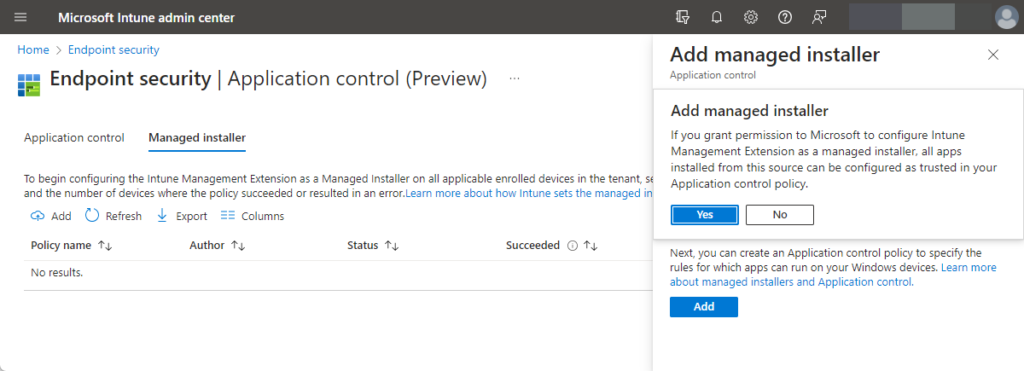
- On the Add managed installer blade, as shown in Figure 1, review the information and click Add
- On the confirmation dialog, confirm the choice and click Yes
Important: Keep in mind that this configuration will add the Intune Management Extension as a managed installer in a rule collection in AppLocker. That might impact existing AppLocker and WDAC configurations.
Note: To remove the Intune Management Extension as managed installer, edit the policy and turn off the setting.
Configuring Application Control to trust apps from managed installers
Once the Intune Management Extension is configured as a managed installer, it’s time to configure an actual WDAC policy that can user that configuration. For that purpose, Microsoft also introduced a new iteration of Application control policies. Those policies rely on the ApplicationControl CSP and are available via the Endpoint security node within Microsoft Intune. And those policies can be used to manage which apps are allowed to run on the managed Windows devices. Any apps that aren’t explicitly allowed to run, are blocked from running. For testing purposes, these policies can also run in audit mode. With audit mode, the policy allows all apps to run and logs the details in the Event Viewer.
When looking at the configuration options of the Application control policies, it requires IT administrators to choose between the following two different Configuration settings formats that can be used to configure the WDAC policy:
- Enter xml data – This option provides IT administrators the ability to provide a fully customized XML-file that defines the Application control policy with all the required settings.
- Built-in controls – This option provides IT administrators the simplest path to configure a basic Application Control policy. The built-in controls, provide easy options to approve all apps that are installed by a managed installer, and to trust Windows components and store apps.
Once the different configuration are known, it’s time to look at the actual configuration of an Application Control policy. As the focus for this post is on the ability to configure the Intune Management Extension as a managed installer, the following seven steps will walk through the configuration of an Application control policy using the built-in controls.
- Open the Microsoft Intune admin center portal and navigate to Endpoint security > Application control
- On the Endpoint security | Application control page, on the Application control tab, click Create Policy
- On the Basics page, specify a valid name to distinguish the policy from other similar policies and click Next
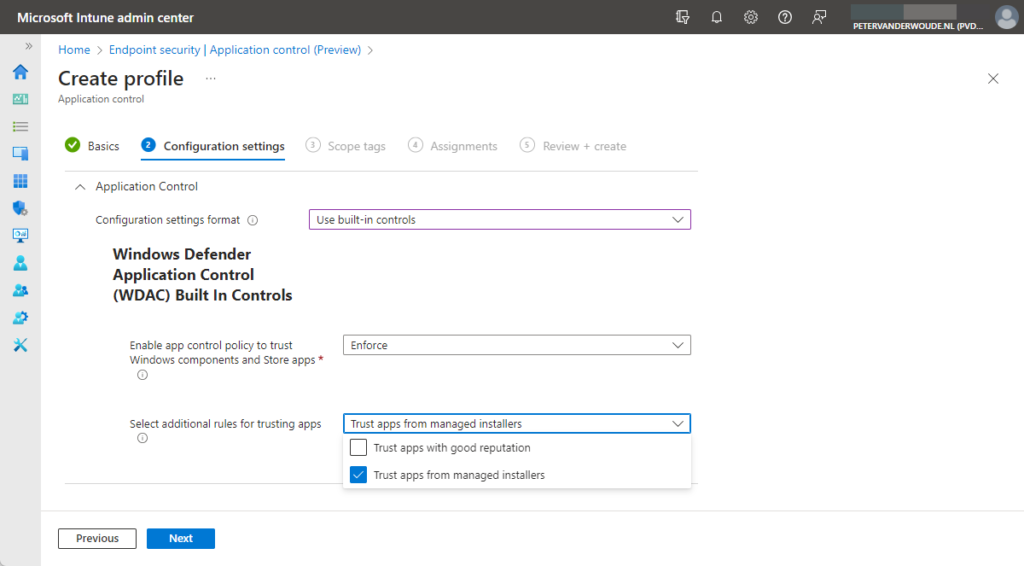
- On the Configuration settings page, as shown in Figure 2, provide the following information and click Next
- Configuration settings format: Select Use built-in controls to use the simplest path to configure a basic policy
- Enable app control policy to trust Windows components and Store apps: Select Enforce to allow Windows components and Store apps, as well as other trusted apps (alternatively Audit mode can be used)
- Select additional rules for trusting app: Select at least Trust apps from managed installers to trust apps that are installed by the Intune Management Extension and optionally select Trust apps with a good reputation to also trust apps that are defined as reputable apps by the Microsoft Intelligent Security Graph
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the required assignment by selecting the applicable group and click Next
- On the Review + create page, review the configuration and click Create
Note: With these new policies, it’s now also possible to create supplemental policies that add additional rules.
Experiencing Intune Management Extension as managed installer
Once the Intune Management Extension is added as a managed installer, and the Application Control policy is applied, it’s time to look at the experience. The easiest would be to simply show a screenshot of a working app, but that doesn’t mean that much. The best would probably be, to show that an app is actually installed by Microsoft Intune and tagged as installed by a managed installer. And the easiest method to achieve that, is by looking at Event ID 3090. That event indicates that a file was allowed to run based on managed installer and can be enabled by adding the following registry key.
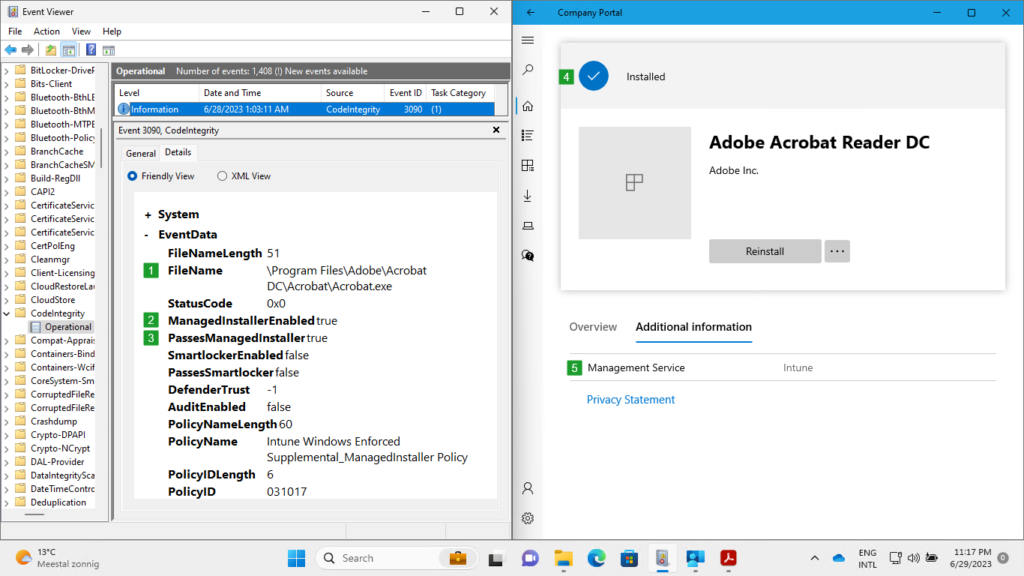
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\CI -v TestFlags -t REG_DWORD -d 0x300When enabling Event ID 3090, the interesting information becomes available in Microsoft > Windows > CodeIntegrity > Operational log. As shown below in Figure 3, that event shows the FileName (1) of the installed application, ManagedInstallerEnabled (2) indicating that the policy enables managed installer trust, PassesManagedInstaller (3) indicating that the file originated from a managed installer, and event the PolicyName indicating the policy that the event applies to. Besides that, the same figure also shows that the specific application was Installed (4) by using Intune as the Management Service (5).
There are also many other locations and configurations to look at, to verify a successful configuration. To name a few:
- Use
Get-AppLockerPolicy -Effective -XML > {location}\AppLocker.xmlto verify the managed installer configuration in the AppLocker policy on the device - At the location of C:\Windows\System32\AppLocker at least a file named ManagedInstaller.AppLocker should exist that contains information about the Intune Management Extension
- At the location of C:\Windows\System32\CodeIntegrity\CiPolicies\Active at least a file should exist with the PolicyID of the created base policy (the PolicyIDs of the built-in controls are documented here)
More information
For more information about Windows Defender for Application Control and managed installers, refer to the following docs.
Very nice, takes away a lot of the headache in managing this. Setting Managed Installer and Base Policy Deployment works fine. However, Supplemental Policy Upload seems to fail for me, no matter what I do.
“Policy creation: Failed to create policy, try again later”
🙁
Hi Alpha,
Apologies for the late reply, as I was enjoying my vacation. Have you seen my follow-up post around that subject: https://www.petervanderwoude.nl/post/creating-supplemental-application-control-policies-for-the-base-application-control-policies-created-with-the-built-in-controls/
Regards, Peter
Thought readers would benefit from knowing WDAC managed installer and msstore WDAC options don’t seem to work with winget (even through the msstore)!
I tested the the new built in WDAC controls to deploy the msstore version of Adobe Reader and WDAC blocked it. After a month with a ms support ticket they confirmed “you will need to specifically allow it to run by adding a supplemental policy.”
As far as I can tell there are 3 different features that don’t really work like MS documentation says they should.
1 – Intelligent Security Graph – adobe reader installer app from the MS store is one of the most common msstore apps in the world and is safe (unless there is something I don’t know). Why wouldn’t it be allowed by ISG?
2 – managed installer – the feature is described as “This option lets you automatically allow applications installed by a designated software distribution solution, such as Microsoft Configuration Manager (MEMCM) or Microsoft Intune.” It doesn’t say anything about limitations based on intune application type or winget.
3 – trust Windows components and Store apps – this feature is described as “When this setting is Enabled (the default), managed devices can run Windows components and store apps” It also doesn’t say anything about limitations based on intune application type or winget.
Thank you Jeremy. It does sound a bit strange though, because – if I’m not mistaken – I could just install the Company Portal app. Or are you referring to Win32 apps from the Store?
Regards, Peter
Yes, win32 apps from the ms store.
Steps to reproduce the issue:
– assign the “Trust apps with good reputation, Trust apps from managed installers” built in WDAC control in Intune.
– setup the managed installer feature in intune.
– assign acrobat reader and VLC win32 apps from the msstore.
– do an autopilot build and observe WDAC block the installations.
I’m leaning towards the diagnosis that the managed installer policy hasn’t applied when the installs run. but later after user logon these apps do eventually install (when the managed installer policy has applied?).
Either way, something is not working right.
Thank you for that addition.
Regards, Peter