This week another blog post about Windows 10 and OMA-DM. However, this time it might not be that obvious. In this post I’ll go through the configuration of enabling the provisioning of Microsoft Passport for Work on Windows 10 devices. Maybe even more important, I’ll go through the PassportForWork configuration service provider (CSP) that is used to provision that configuration.
During this blog post I’ll go through the PassportForWork CSP, the configuration steps in Microsoft Intune hybrid and standalone and the end-user experience.
PassportForWork CSP
Before starting with the configuration of enabling the provisioning of Microsoft Passport for Work on Windows 10 devices, it’s good to get a better understanding of what is actually used to get the configuration in place. The configuration through Microsoft Intune hybrid and standalone uses the PassportForWork CSP. That CSP is used to provision Microsoft Passport for Work, which allows the end-user to login to Windows using the AD, or Azure AD, account and replace passwords, smartcards, and virtual smart cards for that specific device. Microsoft Passport for Work lets the end-user use a user gesture to login, instead of a password. A user gesture can be a simple PIN, biometric authentication, or an external device.
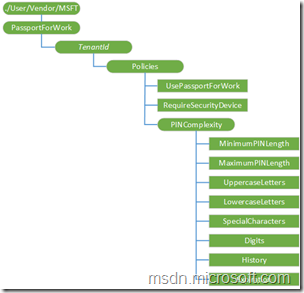
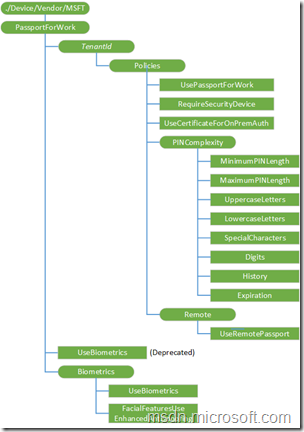
Below is an overview of the nodes of the PassportForWork CSP. I won’t go through the nodes in detail, as that information will come during the configuration, but make sure to switch back a couple of times to connect the configuration with the CSP.
| User configuration | Device configuration |
 |
 |
Configuration
Now it’s time to start with the configuration of enabling the provisioning of Microsoft Passport for Work on Windows 10 devices. I’ll walk through the configuration steps for Microsoft Intune hybrid and standalone and I’ll provide the configuration options. While going through the configuration options, please make sure to switch back to the PassportForWork CSP a few times and connect the configuration options with the CSP nodes.
Microsoft Intune hybrid
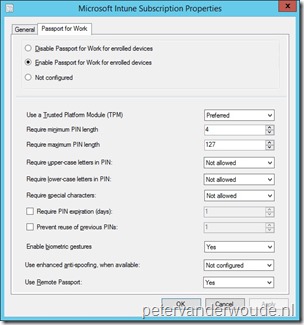
Let’s start with the configuration in Microsoft Intune hybrid. I’ll walk through the required steps to configure Microsoft Passport for Work for enrolled Windows 10 devices.
Microsoft Intune standalone
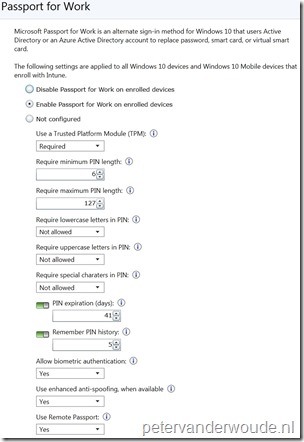
Let’s continue with the same configuration within Microsoft Intune standalone. I’ll walk through the required steps to configure Microsoft Passport for Work for enrolled Windows 10 devices.
End-user experience
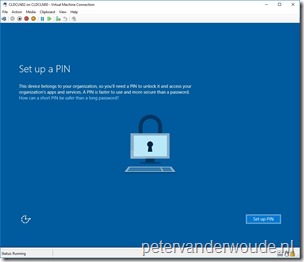
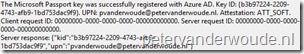
Let’s end this post with the most important thing, the end-user experience. After the device is registered in Azure AD and enrolled into Microsoft Intune hybrid, or standalone, Microsoft Passport for Work will be provisioned for the end-user. On a fresh device the end-user will be prompted to set up a PIN during the initial logon. A successful configuration will be logged in the User Device Registration node in the Event Viewer with Event ID 300.
| End-user experience | Event Viewer |
 |
 |
More information
Fore more information about Microsoft Passport for Work on Windows 10 and the PassportForWork CSP, please refer to:
- Microsoft Passport guide: https://technet.microsoft.com/en-us/itpro/windows/keep-secure/microsoft-passport-guide
- Implement Microsoft Passport in your organization: https://technet.microsoft.com/en-us/itpro/windows/keep-secure/implement-microsoft-passport-in-your-organization
- PassportForWork CSP: https://msdn.microsoft.com/en-us/library/windows/hardware/dn987099(v=vs.85).aspx
- Control Microsoft Passport settings on devices with Microsoft Intune: https://docs.microsoft.com/en-us/intune/deploy-use/control-microsoft-passport-settings-on-devices-with-microsoft-intune
- Control Microsoft Passport settings on devices with System Center Configuration Manager: https://technet.microsoft.com/en-us/library/mt488797.aspx