This week is focused on conditional access and the recently introduced grant control of Require app protection policy (preview). I already tweeted about it a couple of weeks a go, but I thought that it would be good to also write a little bit about this grant control. The Require app protection policy (preview) grant control could be seen as the successor of the Require approved client app grant control. The main difference is that the new Require app protection policy (preview) grant control will be more flexible. In this post I’ll start with a short introduction about this new grant control, followed by a configuration example. That example will be about a scenario for accessing Exchange Online. I’ll end this post by showing the end-user experience.
Introduction
Now let’s start with a short introduction about the Require app protection policy (preview) grant control. This grant control is not static and will be flexible as it will simply require that the user received an app protection policy for the app that is used for accessing the respective cloud app. That immediately checks a couple of boxes, as it will require the user to have an Intune license, it will require the user to receive app protection policies and it requires apps to be configured to receive an app protection policy. Besides that, this will also enables organizations to start using third-party apps and line-of-business apps in combination with conditional access. That should be a big advantage compared to the Require approved client app grant control.
There are also a couple of things keep in mind; the Require approved client app grant control only supports iOS and Android and the apps should be using the Intune App SDK. Also, at this moment, this grant control only applies to Microsoft OneDrive and Microsoft Outlook.
Configuration
Let’s continue by having a look at the configuration options, by looking at a simple scenario that is focused on the Require approved client app grant control. That scenario is requiring an app protection policy on any platform, for accessing Exchange Online. Not supported platforms should be blocked. The following seven steps walk through that scenario.
| 1 | Open the Azure portal and navigate to Microsoft Intune > Conditional access > Policies or to Azure Active Directory > Conditional access > Policies to open the Conditional Access – Policies blade; |
| 2 | On the Conditional Access – Policies blade, click New policy to open the New blade; |
| 3 |
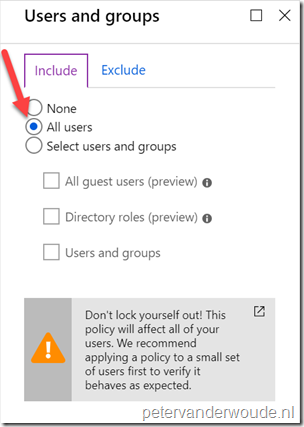
Explanation: This configuration will make sure that this conditional access policy is applicable to all users. |
| 4 |
Explanation: This configuration will make sure that this conditional access policy is only applicable to Exchange Online. |
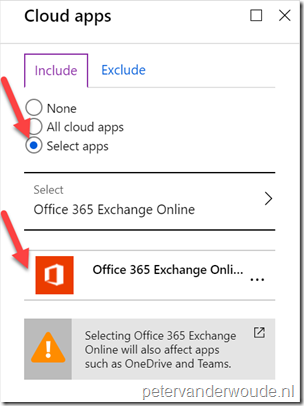
| 5 |
On the New blade, there is no need to select the Conditions assignment; Explanation: This configuration will make sure that this conditional access policy is applicable to all platforms, locations, client apps and device states. That will also make sure that platforms, which are not supported by this grant control, will be blocked. |
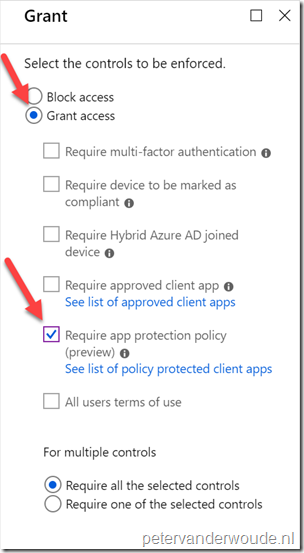
| 6 |
Explanation: This configuration will make sure that this conditional access policy will grant access for the assigned users, to the assigned cloud apps, when using an app with app protection policy applied. |
| 7 | Open the New blade, select On with Enable policy and click Create; |
Note: Keep in mind that the Require app protection policy control is still in preview.
End-user experience
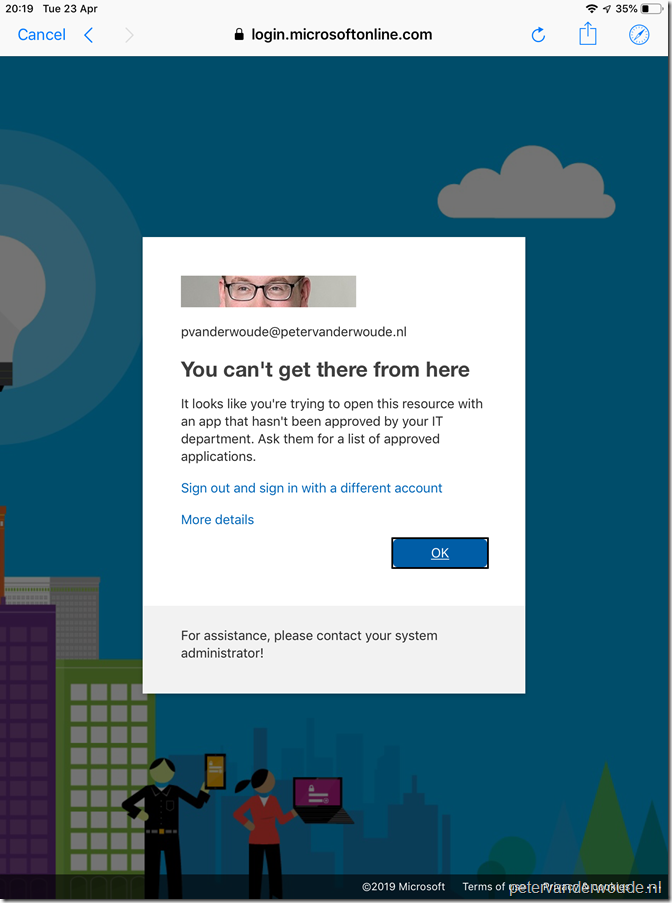
Now let’s end this post by having a look at the end-user experience on an iOS device. Specifically in scenarios when the end-user will be blocked. When the end-user wants to configure their email in the native iOS mail app, the end-user will receive a notification as shown below. It basically explains the end-user that this app is not approved.
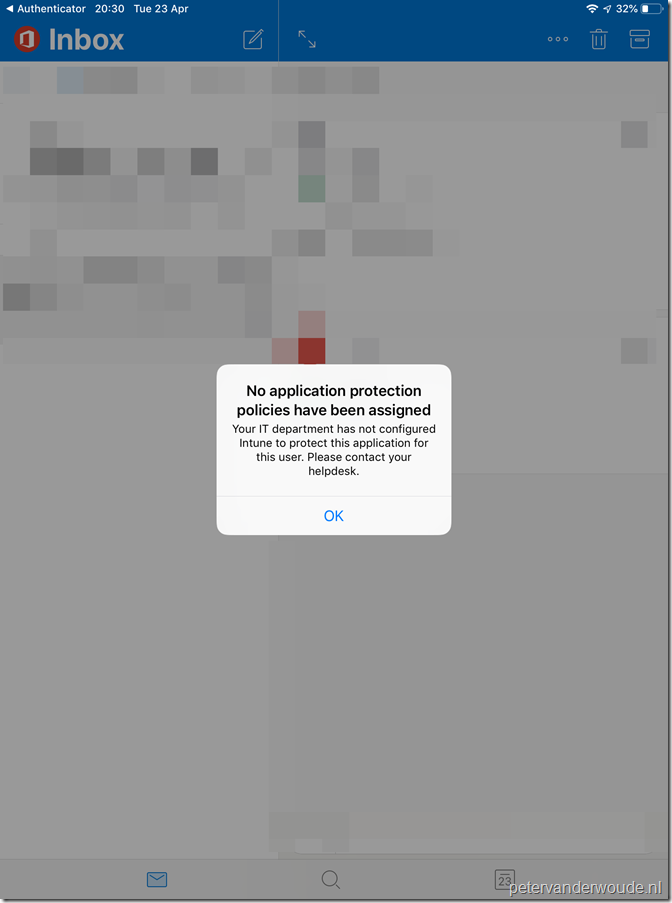
When the end-user wants to configure their email in the Outlook app, but no app protection policy is assigned to the app, the end-user will receive a notifications as shown below. It simply explains the end-user that no app protection policy is applied.
Note: Keep in mind that this is still a preview feature. In some of my test I would receive the (returning) message in the Outlook app, but I could still send and receive email.
More information
For more information regarding conditional access and requiring app protection policies, please refer to the following articles:
- What are access controls in Azure Active Directory conditional access?: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/controls
- Require app protection policy for cloud app access with conditional access (preview): https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/app-protection-based-conditional-access
- Azure Active Directory conditional access settings reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/technical-reference#app-protection-policy-requirement
Hi Peter, Do you know if this still require a broker app (Android Company Portal or iOS Authenticator) to be installed? Thanks, Ryan.
Hi Ryan,
To my knowledge a broker app is still required.
Regards, Peter
My experience has been that only Android requires the broker app, not IOS. Make sure when you create the intune app policy you select unmanaged devices, otherwise it requires the broker/registration.
I was trying to understand if I could use it in an “require one of the selected controls” option where I could have a “compliant device” or “use a app protected policy” and simply apply the app protection policy if it wasn’t a managed device. (if you look at CA it allows for selected both of these grants, and if I had MAM only when it wasn’t managed/compliant, I could still cut and paste inside a managed device to any application)
Anyone have experience here? Thanks
Hi Ed,
I don’t completely understand your question. You want to require a compliant device OR a managed app? In that case your behavior is expected. In that case you don’t need a managed app on a managed device.
Regards, Peter
Hi Peter,
Great Work!
I have 2 questions. We are using MAM-WE and we have setup CA with OR 1. Require approved client app (Teams is not part of App Protection Policy list yet). 2. Require App Protection Policy.
Questions:
1) Why with some users does it rrequire to Register the device with Azure AD.
2) How come when only selecting in CA option 2 then Teams cant login from IOS since “not a an approved client app. This behavior should also be the same with Android correct?
Thanks for all the info you bring. Im a big Fan!!
Hi Aron,
1. An user must always register once via the broker app (the Authenticator on iOS). Maybe the user already register for a different app.
2. When using option 2, only apps on that specified list are allowed (when also using APP). And yes, the behavior is the same for Android (just a different broker app).
Regards, Peter
One issue i have found
1) Putting in a APP Protection Policy for Teams -> Then a CA policy to “Require Require app protection policy (preview)” – On iOS the user still cannot use Teams. Error still comes when I try sign into Teams:
“It looks like you’re trying to open this resrouce with a client app that is not available for use with app protection policies”
Teams does not show as a supported app yet for this CA policy setting – therefore have needed to remove this for the time being on clients whos accounts use CA with App Protection Policies.
Hi Adam,
I thought that was why you were also using Require approved client app?
Regards, Peter
Hi Peter,
Yes this is why I am using “Require approved client app” – this was just to update your blog that with “Require App Protection Policy” Teams is not supported. Therefore, during my testing, if you select this option for “Require App protection policy” & have Teams in the Protected App Policy on Endpoint manager, users are unable to use Microsoft Teams.
Therefor as you’ve mentioned, we use Require Approved Client App only at the moment. – This means (I believe) that I am not able to do app selective wipe or other controls that are associated when using “App Protection Policy” for MS Teams – Other Apps such as outlook etc are fine.
Here is a thread I found on Reddit that also helps explain: https://www.reddit.com/r/Intune/comments/eqj9ax/teams_and_app_protection_policies/
Thank you for the update, Adam! Regarding your last note: you’re correct that a selective wipe is only possible for managed apps.
Regards, Peter
@Peter @Adam
Correct me if im wrong. CA is only to get access to the protected app but once you have access and 1) in the correct group 2) have a APP with the app assigned to that policy (Teams) it will still be protected since Intune assigns the protection policy.
With this i believe that app selective wipe will work regardless. Even though in my experience it was a hit or miss with all apps.
Hi Aaron,
You’re absolutely correct! Selective wipe is not a CA feature but an APP feature. I should have been clearer on that part. Selective wipe is always available for managed apps (APP) and the use of CA doesn’t matter.
Regards, Peter