This week something completely different, but maybe even more intriguing at some level. That something is Windows Autopach groups. Windows Autopatch groups are logical containers, or units, that can group several Azure AD groups and different software update policies, within Windows Autopatch. That’s a really nice addition to Windows Autopatch that is available starting with the latest service update of May 2023. Windows Autopatch groups enable organizations to create different selections of devices with as many as 15 unique deployment rings, custom cadences and content. And a tenant can contain up to 50 Windows Autopatch groups. That enables IT administrator to create nearly any structure for patching their devices within Windows Autopatch. This post will start with some more details for understanding Windows Autopatch groups, followed with the steps for using those Windows Autopatch groups.
Note: Keep in mind that Windows Autopatch also requires Windows 10/11 Enterprise E3 (or higher) licenses.
Introducing Windows Autopatch groups
Windows Autopatch is a cloud service, provided by Microsoft, that automates the update process for Windows, Microsoft 365 Apps for enterprise, Microsoft Edge, and Microsoft Teams. All with the idea to further improve security and productivity. That on itself is not something new, but, within the last couple of months, lots of new features are introduced to provide more flexibility to organizations. One of the biggest improvements is Windows Autopatch groups. Those Windows Autopatch groups enable organizations to replicate organizational structures, create up to 15 deployment rings, control the devices in the different rings, and choose the deployment cadence. All with the idea that it’s possible to be fully customized, within the boundaries of the Windows Autopatch service. For organizations with a lot less requirements, Windows Autopatch can also still be used with default values. For the complete picture, the following concepts are important to understand:
- Windows Autopatch groups: By service default, Windows Autopatch contains a default Windows Autopatch group. That group contains five deployment rings and a default update cadence for updates. Besides that, that group can’t be deleted or renamed. It’s, however, possible to customize the devices in deployment rings and the update cadence for each ring. It’s also possible to create custom Windows Autopatch groups. That provides flexibility in all areas; the number of groups, the number of deployment rings per group and the update cadence per deployment ring.
- Deployment rings: By service default, the default Windows Autopatch group contains five deployment rings (as shown below in Figure 1). That includes a test and a last ring. Assigning devices to those rings is always a manual process. Besides that, the other three rings can be configured by providing percentages of devices, or by providing specific device groups. It’s, however, possible to configure the update cadence of all default deployment rings. With custom groups it’s also possible to configure the number of deployment rings, the members of those rings and the deployment cadence of those rings. Every deployment ring, however, always contains the test and the last ring.
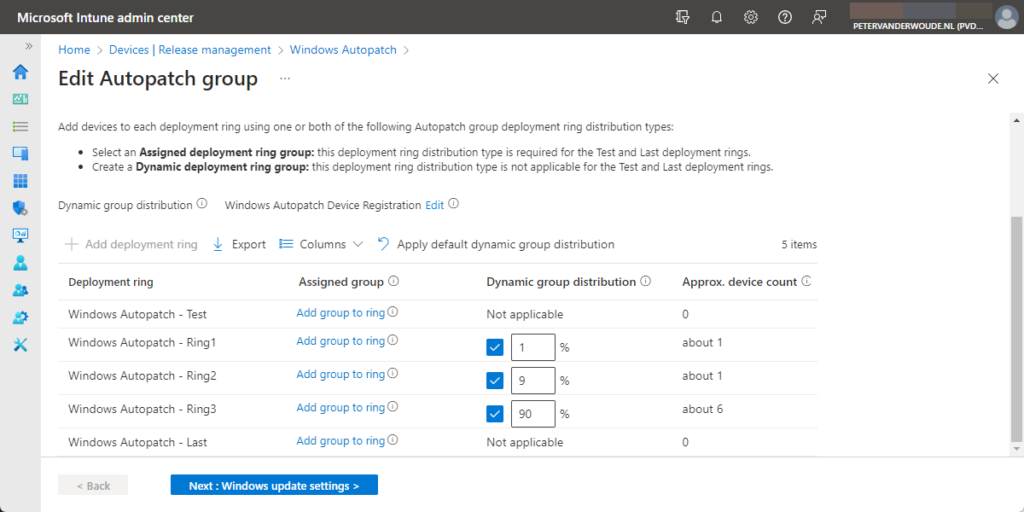
- Deployment cadence: By service default, every default deployment ring contains a deployment cadence (as shown below in Figure 2). That includes update rings policies and feature update deployments. The configuration of the deferral period, the deadline, the grace period, and the user notifications, is fully customizable. Those configuration options are also the same for every custom Windows Autopatch group.
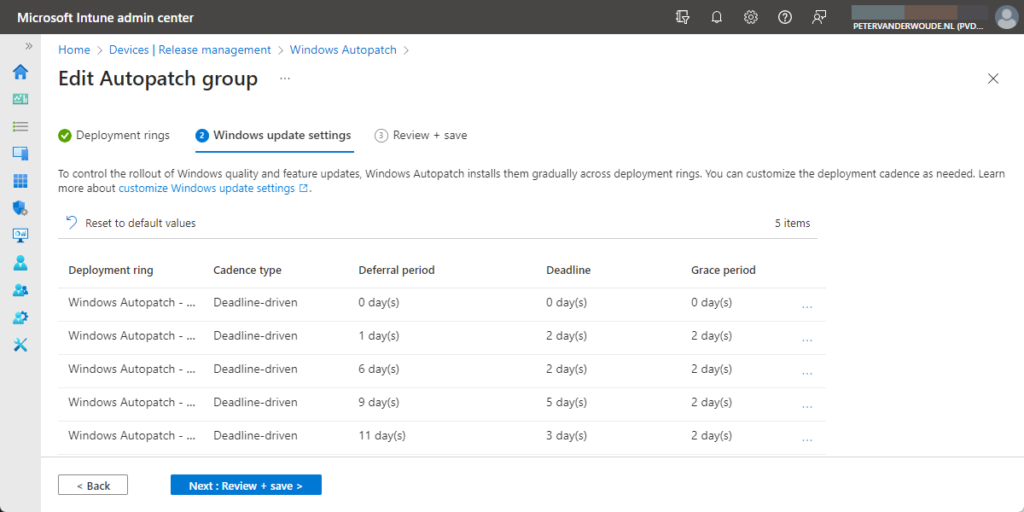
- Device registration: By service default, the device registration relies on the Windows Autopatch Device Registration group, unless creating or editing (custom) Windows Autopatch groups to use existing Azure AD groups.
Note: A tenant can contain up to 50 Windows Autopatch groups and a group can contain up to 15 deployment rings. Besides that, Windows Autopatch groups are only supported for quality updates and feature updates.
Creating custom Windows Autopatch groups
When understanding the Windows Autopatch groups, it’s time to have a closer look at creating a new Windows Autopatch group and seeing what configuration options that brings. The following six steps walk through the process of creating a custom Windows Autopatch group and help with understanding the different configuration options.
- Open Microsoft Intune admin center and navigate to Devices > Windows Autopatch > Release management
- On the Devices | Release management page, select the Windows Autopatch groups and click Create
- On the Basics page, specify a valid name to distinguish the group from other similar groups and click Next
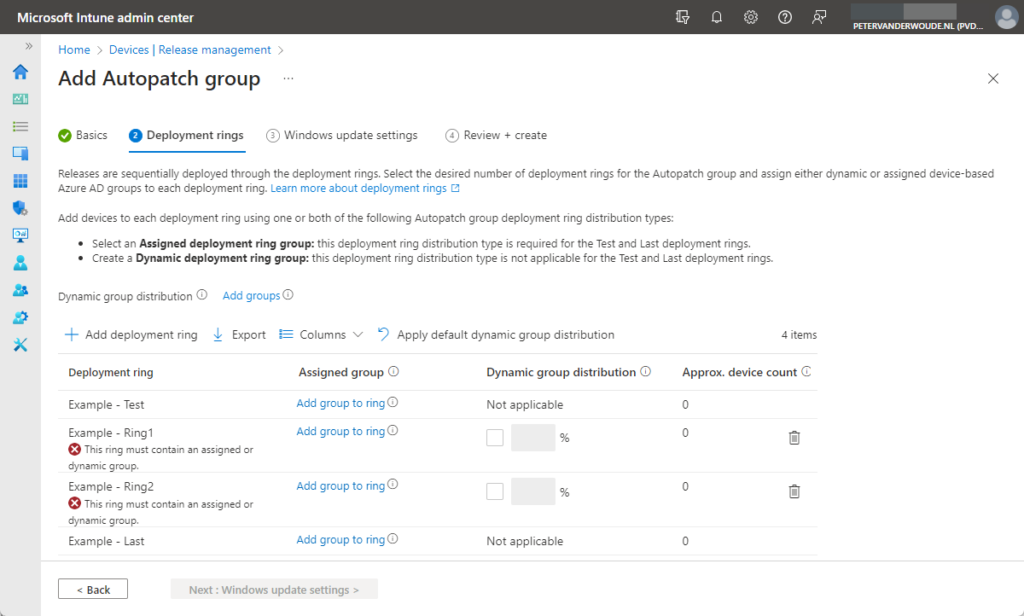
- On the Deployment rings page, as shown below in Figure 3, use the following configuration options to come to the required deployment rings configuration and click Next
- Use Dynamic group distribution to configure one ore more Azure AD groups that will be used for the dynamic group distribution and configure the required percentages for the add deployment rings
- Use Add deployment ring to add up to 13 additional deployment rings (that brings the total to 15 deployment rings)
- Use Add group to ring to assign a specific Azure AD group of devices to at least the test and last deployment ring and potentially – depending on the requirements – also to the added deployment rings
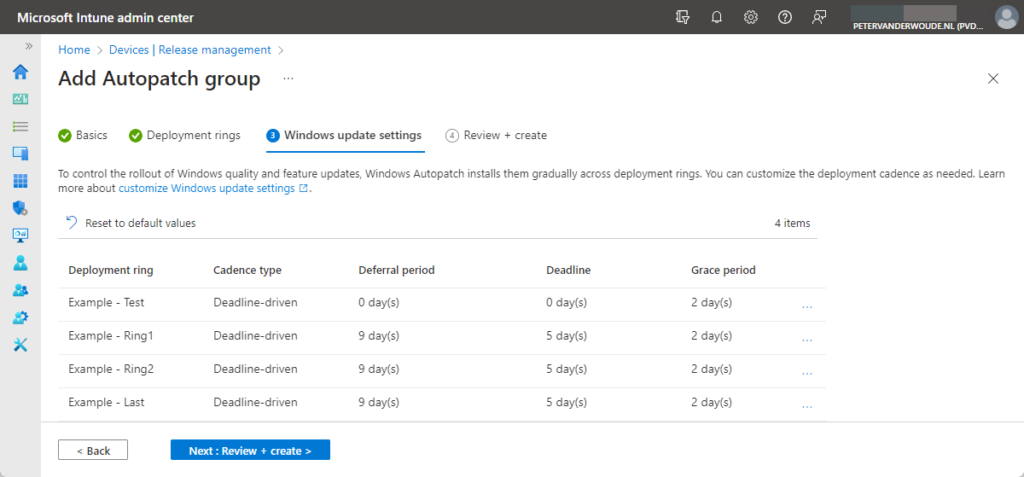
- On the Windows update settings page, as shown below in Figure 4, use the following configuration options (available via the three dots) to come to the required Windows updates settings configuration and click Next
- Use Manage deployment cadence to configure the deployment cadence by choosing between deadline driven and scheduled install, and configuring the related configurations based on that choice
- Use Manage notifications to configure the Windows Update notification behavior
- On the Review + create page, review the configuration and click Create
Note: After creating a custom Windows Autopatch group, it can always be edited and deleted again.
More information
For more information about Windows Autopatch and Windows Autopatch groups, refer to the following docs.
Nice addition for Autopatch.!.
Does this means, if I enable the Autopatch groups (preview), the groups like “Modern Workplace Devices-Windows Autopatch-Broad” are being replaced with the “Windows Autopatch – ring” groups?
I see without having the Autopilot groups enabled, they already exists in the tenant and are being filled with devices, but the groups are not used in the (update) profiles (yet).
No. There will be a differentiation between service-based and deployment update rings. See for more information: https://learn.microsoft.com/en-us/windows/deployment/windows-autopatch/deploy/windows-autopatch-groups-overview#service-based-versus-software-update-based-deployment-rings
Regards, Peter