This week is a short post about the ability to prevent users from shutting down, or restarting, specific devices. That is something already often used for specific servers, like domain controllers, to prevent users from shutting them down. There are, however, also good reasons why that might also be very useful and beneficial on specific devices. Think about devices that host critical business processes that can only be turned off, or restarted, during specific windows. For those devices the user right to shutdown that device, should only be provided to a few trusted users, or administrators. So, not just removing the shutdown, or restart, button, but actually removing the user right to perform a shutdown. Luckily, nowadays there is an easy method for configuring the list of users that are allowed to shutdown a specific Windows device. This post will provide some more details around that configuration, followed with the configuration steps. This post will end with showing the user experience.
Note: Keep in mind that this post is focussed on the local options on the Windows device.
Configuring preventing users from shutting down specific devices
When looking at preventing users from shutting down, or restarting, specific Windows devices, the UserRights section in the Policy CSP is the place to look. That section contains many of the different policy settings of the User Rights Assignment Local Policies, including the Shut Down The System (ShutDownTheSystem) policy setting. That policy setting can be used to configure the users that are allowed to locally shutdown, or restart, the device. The configuration of that policy setting is available via the Settings Catalog. The following eight steps walk through the creation of a Settings Catalog profile that contains the required setting to configure the local shutdown rights, by using the Shut Down The System policy setting.
- Open the Microsoft Intune admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create > New Policy
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later to create a profile for Windows 10 devices
- Profile: Select Settings catalog to select the required setting from the catalog
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: (Greyed out) Windows 10 and later
- On the Configuration settings page, as shown below in Figure 1, perform the following actions and click Next
- Click Add settings and perform the following in Settings picker
- Select User Rights as category
- Select Shut Down The System as setting
- Specify the allowed users and local groups on separate lines (1)
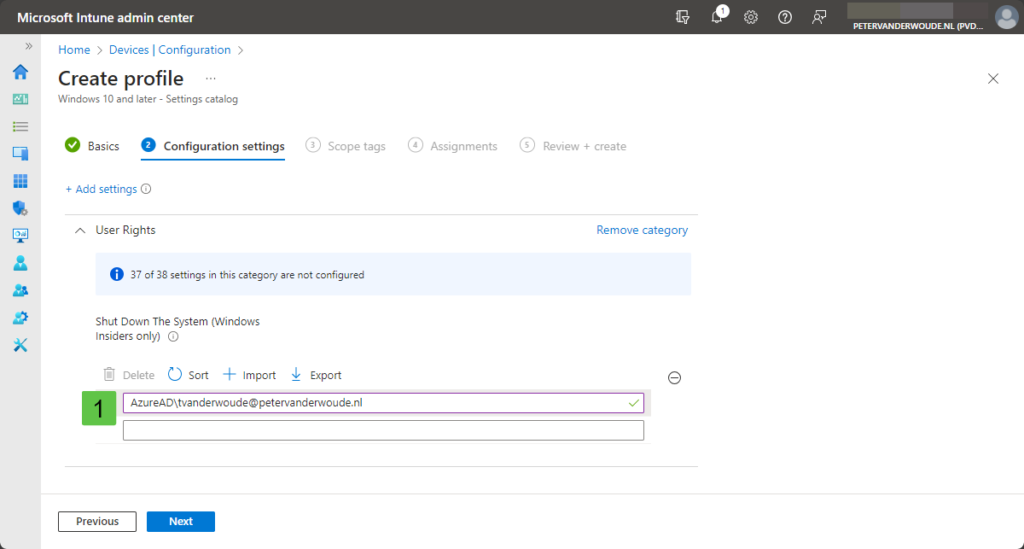
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the assignment for the specific devices and click Next
- On the Review + create page, verify the configuration and click Create
Note: The setting mentions that it’s available for Windows Insiders only, but that’s not the experience so far.
Experiencing users prevented from shutting down specific devices
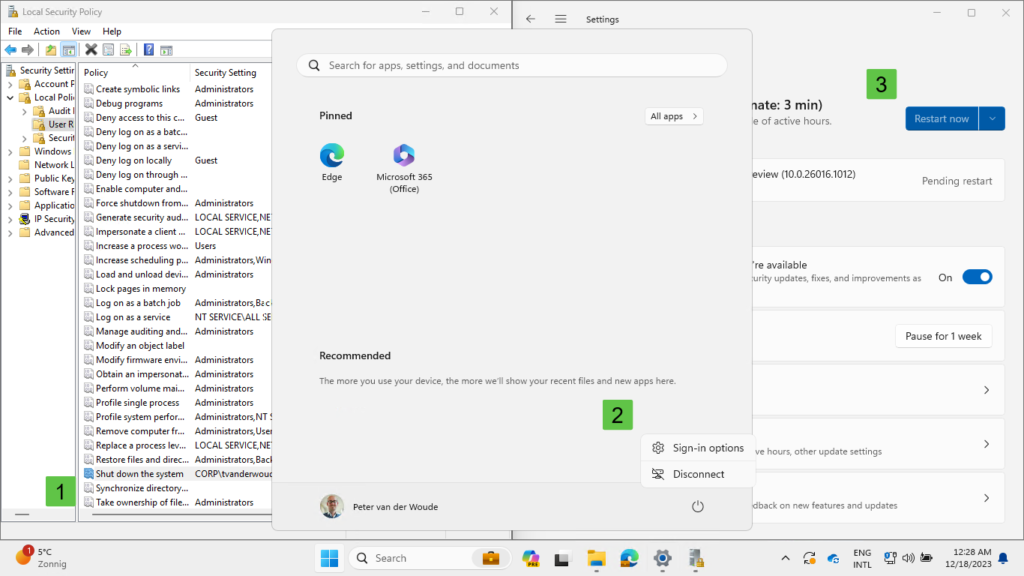
After configuring the list with users that are allowed to shutdown the device, it’s time to look at the user experience. And there are many things that indicate the behavior and that the configuration is applied. That can be the actual applied configuration, as well as the experience of the user. Pieces of both are shown below in Figure 2. To start with the first, the applied configuration can be verified in the Local Security Policy by looking at Local Policies > User Rights Assignment. That includes the Shut down the system right (1) that includes the configured list of users and local groups that are allowed to shutdown the system. The applied configuration will make sure that the users cannot shutdown, or restart, the device. That can be verified by for example looking at the available power options for the users (2), or the ability to restart the device after the installation of updates (3). Besides that, even command actions will be prevented and give the user an access denied message.
Note: This configuration was successfully tested on the latest Windows Insiders builds and on Windows 11 version 23H2.
More information
For more information about preventing users from restarting Windows, refer to the following docs.
I don’t suppose you tested this on Win 11 22H2 as well did you by any chance? I’m not having much luck setting it yet, I’ve even tried using a SID rather than domain group name.
Before I dig too deeply I’m unsure if it’s the Windows Insider thing mentioned that isn’t working on 22H2 – but does on 23H2, or if it’s something else.
Hi Steve,
I’ve successfully tested it on Windows 11 23H2 and Insider Builds.
Regards, Peter