At the end of last year Microsoft introduced the very nice feature of mobile application management without the requirement of device enrollment. What makes it even better is that it can also be used in combination with third-party mobile device management and it can be used in combination with Microsoft Intune mobile device management. In this blog post I’ll go through the configuration options, I’ll go through the configuration steps and I’ll go through the end-user experience.
Configuration in the Azure portal
Now let’s start with the configuration of this type mobile application management policies. The first difference, with the normal mobile application management policies, is that the configuration is done through the Azure portal. The rest of the configuration experience is also completely different. However, the configuration options are pretty similar.
Different configuration options
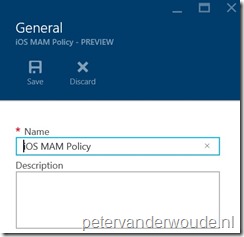
The mobile application management policies in the Azure portal, contain four different configuration parts. These four parts together are the targeted mobile application management policy. Let’s go through these four parts and see how they fit together.
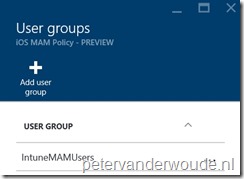
Important: Only users that are member of the selected group AND have a Microsoft Intune license assigned, are affected by the mobile application management policy.
Basic steps
After getting familiar with the different configuration options, it’s time to look at the creation and the deployment of a mobile application management policy. The following twelve straight forward steps will guide anyone through the configuration and deployment.
| 1 | In the Azure portal navigate to Intune mobile application management > Settings to open the Settings blade; |
| 2 | In the Settings blade, click App policy to open the App policy blade; |
| 3 | In the App policy blade, click Add a policy to open the Add a policy blade; |
| 4 | In the Add a policy blade, provide a Name for the policy, select the Platform and click Apps to open the Apps blade. |
| 5 | In the Apps blade, select at least one app and click Select to return to the Add a policy blade; |
| 6 | Back in the Add a policy blade, click Settings to open the Settings blade; |
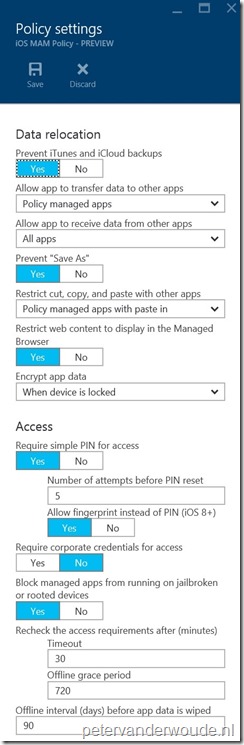
| 7 | In the Settings blade, configure the Data relocation settings and the Access settings and click OK to return to the Add a policy blade; |
| 8 | Back in the Add a policy blade, click Create to create the policy and to return to the App policy blade; |
| 9 | Back in the App policy blade, click the <NewPolicy> to open the <NewPolicy> blade; |
| 10 | In the <NewPolicy> blade, click User groups to open the User groups blade; |
| 11 | In the User groups blade, click Add user group to open the Add user group blade; |
| 12 | In the Add user group blade, select an user group and click Select to save the changes and to return to the User groups blade. |
End-user experience
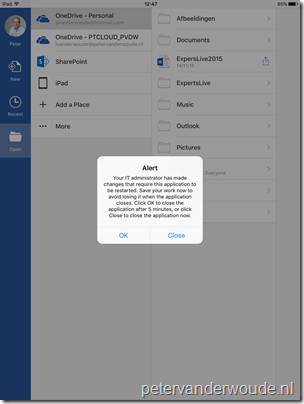
Now it’s time to have a look at the end-user experience. When an end-user is targeted with a mobile application management policy and wants to use one of the configured apps, the end-user will get the messages below after providing company credentials. The first message will show after the initial configuration and the second message will show after removing the configuration again.
| Initial configuration | Removal configuration |
 |
 |
More information
For more information about mobile application management, the supported apps and even more, please refer to:
- Configure data loss prevention app policies with Microsoft Intune: https://technet.microsoft.com/en-us/library/mt627825.aspx
- Create and deploy mobile app management policies with Microsoft Intune: https://technet.microsoft.com/en-us/library/mt627829.aspx
- Microsoft apps you can use with Microsoft Intune mobile application management policies: https://technet.microsoft.com/en-us/library/dn708489.aspx
- Microsoft Intune application partners: https://www.microsoft.com/en-us/server-cloud/products/microsoft-intune/partners.aspx
- Microsoft Intune – Mobile Application Management (MAM) standalone: https://blogs.technet.microsoft.com/cbernier/2016/01/05/microsoft-intune-mobile-application-management-mam-standalone/

How does this apply to Intune hybrid and restricting access to all unmanaged devices? Would you have a MAM policy for the Intune Hybrid apps then another MAM policy via the Intune/Azure policy for all unmanaged devices targeting All Users?
Yes, in that case you use ConfigMgr for MAM with enrollment and the Azure portal for MAM without enrollment.
Hi Peter,
Any idea if it is possible to restrict access to as an example email for unmanaged apps? I want to use MAM for BYOD`s so the users can access corporate data on the way, but I don`t them to use third-party/ build in apps which are unmanaged.
Kind regards,
Dani
Hi Dani,
You can achieve something like that when you’re also using ADFS on-premises. For some ideas, please refer to: https://www.petervanderwoude.nl/post/conditional-access-for-exchange-online-to-the-max/
Peter
Thanks Peter, great article!
Hello Peter,
Can we use MAM-WE for Windows mobile phones as well?
If yes than it will be only support to BYOD devices or else it can support to COD devices??
Kindly update.
Thank you!
Regards,
Richie
Hi Richie,
Windows 10 (Mobile) relies on WIP for a MAM experience. For more information see: https://docs.microsoft.com/en-us/windows/security/information-protection/windows-information-protection/create-wip-policy-using-mam-intune-azure
Regards, Peter
Peter
So if we are currently using the Azure intune /sccm hybrid , i take it this article is our only option so we dont have to re-enroll our devices?
Hi Ian,
Re-enrolling devices should only be required in really specific scenarios.
Regards, Peter