This blog post uses the Accounts configuration service provider (CSP), to create a local user account on Windows 10 devices. This area was added in Windows 10, version 1803, which is currently available as Insider Preview build.
This week is all about creating local user accounts via Windows 10 MDM. That can for example make life a bit easier with troubleshooting an offline device. A fallback account. In this post I’ll show how this can be achieved by using the Accounts CSP. I’ll show the available nodes and I’ll show how to configure them. I’ll end this post by showing the end-user experience. Also, spoiler alert, it’s good to note that this is not a pretty administrator experience at this moment, but I’m pretty sure that will be fixed when it’s a built-in configuration in Microsoft Intune.
Overview
Let’s start by having a look at the tree of the Accounts CSP.
Available nodes
The Accounts CSP contains nodes for renaming a computer account and for the creation of a user account. To get a better understanding of the different nodes, it’s good to walk through the available nodes. Specifically those related to user accounts, as those are the subject of this post. Let’s go through those related nodes.
- .Device/Vendor/MSFT/Account – Defines the root node for the Accounts CSP;
- Users – Defines the interior node for the user account information;
- [UserName] – Defines the username of the new local user account;
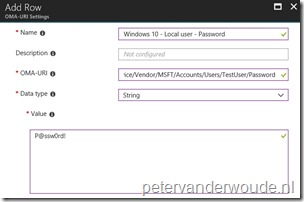
- Password – Defines the password for the new local user account;
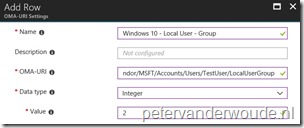
- LocalUserGroup – Defines the local user group for the new local user account.
Configurable nodes
There are basically two configurable nodes related to the creation of a local user account. The Password node and the LocalUserGroup node. The [UserName] node should contain the username and can be anything. The table below provides an overview of the configurable nodes.
| Node | Value | Description |
| Password |
String |
This required setting allows the administrator to set the password for the new local administrator account. |
| LocalUserGroup | Integer 1 – (Default) Users 2 – Administrators |
This optional setting allows the administrator to control the local user group of the new local administrator account. |
Note: The password value can be any valid string and is visible as plaintext in the Azure portal.
Configure
Now let’s continue by having a look at the required and optional configuration to create a local user account on the device. In other words, create a device configuration profile with the previously mentioned custom OMA-URI settings. The following three steps walk through the creation of that device configuration profile. After that simply assign the created profile to a user or device group.
| 1 | Open the Azure portal and navigate to Intune > Device configuration > Profiles; |
| 2 | On the Devices configuration – Profiles blade, click Create profile to open the Create profile blade; |
| 3a |
On the Create profile blade, provide the following information and click Create;
|
| 3b |
|
| 3c |
|
Note: At some point in time this configuration will probably become available in the Azure portal without the requirement of creating a custom OMA-URI.
End-user experience
Let’s end this post by having a quick look at the end-user experience. There’s actually not that much to be shown. Only the created account. Below on the left is a screenshot of the default configuration of the created user account, including the full name, and below on the right is a screenshot of the group memberships of the created user account.
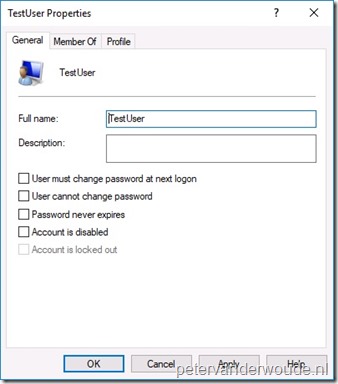 |
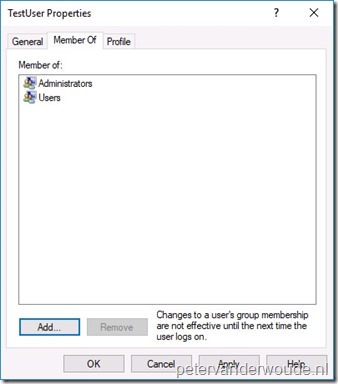 |
Note: The reporting in the Azure portal still provides me with a remediation failed error message, while the actual account creation was a success.
More information
For more information about the Accounts CSP, refer to this article named Accounts CSP.
Thanks for sharing Peter. Especially the ‘Domain/ComputerName’ is a very nice CSP for renaming all those Autopilot desktop-guid devices!
Thanks, Peter! Altijd goede content!
Dank je, Stefan!
Does this work only on Windows 10 1803? If not, then it does not appear to be working. I noticed the “; ” at the end of the OMA-URI. Should that be there?
This is Windows 10, version 1803 and newer. Having said that, the “;” is not part of the OMA-URI.
Regards, Peter
Werkt goed.
Alleen jammer dat het wachtwoord niet wordt aangepast als het account al bestaat op het device. Het werkt dus niet al password – changer voor reeds bestaande accounts.
Hi Jan,
I’ll switch to English. This is indeed only for creating new accounts and not for changing the password of existing accounts. If you want to manage something about the builtin administrator and guest account, you can use the Endpoint protection policy.
Regards, Peter
Hi Peter,
Is there a way to either set the password not to expire or set an expiry time (e.g. 90 days)?
Hi NVader2000,
I haven’t seen a OMA-URI and/or Intune policy for that, yet. Via PowerShell it should be possible.
Regards, Peter
Also just noticed that the Integer value of 2 does not place this newly created account into the Administrators group, just the User group. Please advise.
Another odd bit is that this account does not appear on the login screen. I have done this with PowerShell and I am able to set the expiry, Administrator group, this account appears as a listed account at the login screen. So I am not sure why this one does not.
Hi NVader2000,
Haven’t seen my local users on the login screen either (only when I’ve used them). Not sure if why you would want that..
Regards, Peter
Hi Peter,
Please disregard my post in regards to the account not being placed in the local Administrators group. Found a typo in my OMA-URI. However, the other issues are still open.
Hi NVader2000,
Yes, with a correct OMA-URI it should add the user to the local Administrators.
Regards, Peter
Hi Peter,
Is there any way we can set the new account created not to enforce for changing the password for initial login?
Hi Sandy,
That’s currently not possible through the CSP. You could use a PowerShell script to achieve that.
Regards, Peter
Thanks Peter for quick reply.
I was trying for PS Script but unlucky to accomplish the task since the machine is not joined in AD(Auto pilot – AAD Device) , i am unable to execute the below code.
Set-ADUser -ChangePasswordAtLogon:$True.
I have also checked win32_useraccount class and could see only below options for the object “passwordchnagable \ passwordexpires\passwordrequired”
Could you please suggest me some useful links or your thoughts to achieve ?
Hi Sandy,
Did you look at Set-LocalUser?
Regards, Peter
Is it possible to use this and to setup an autologin user?
Hi Nigelb,
Theoretically, yes, but practically it might be challenging with policy orders. If it’s for Kiosk mode, I’m planning a post on that subject this week.
Regards, Peter
There seems to be some issues with this in 1709, it automatically logs you into the admin account every time you restart. IT seems to work fine with 1803
Hi Misho,
Please see the note at the top of the post. The CSP is introduced in 1803.
Regards, Peter
Hello,
Let Me begin by saying — Thank you for great articles, have helped us very much.
We applied this new profile, but we have issues with actually login into these local users. Only workaround I found was to manually “reset” password from lusrmgr.msc for the user to one from policy. If we try to logon without manually setting it, just getting classic incorrect username or password.
Any ideas?
Hi Janis,
I haven’t seen that. Are you using a specific version of Windows 10? Also, did you see any errors in the Event Viewer?
Regards, Peter
Hello again,
Figured out the issue – password string was modified after initial profile creation and password “change” in Intune does not sync.
However, a new question arose – can you remove these local accounts for all devices from Intune? Looking at the Accounts CSP article, and only supported function was ”Add”.
Hi Janis,
Good to hear. Via the CSP you currently can’t remove the account. You could try that by using PowerShell.
Regards, Peter
Hello Peter,
Yes, simple PS published to to all devices via Intune resolved the issue.
However Account CSP is not as “admin/user friendly” as one would wish, for instance, if you rename the account in CSP profile it will create a new user object and not update the existing one. So good thing to remember for less experienced Intune-rs.
But thank you for all the pointers. Keep up the good job 🙂
Thank you, Janis!
Has anyone figured out how to uncheck the “Change pwd at logon”?
Hi Guu,
Have you looked at PowerShell?
Regards, Peter
Hi Peter,
A compliance policy seems to be the reason it got enabled in the first place. I disabled that and from now on the local admin is created without the “Change pw at logon” enabled.
Hi Guu,
That’s really good information, thank you! Do you also know which specific setting caused that behavior?
Regards, Peter
I’m having the same issue with the local admin being created with the “User must change password at next logon” enabled. If you could provide what setting caused this issue that would be great!
Hi Melissa,
I haven’t tested this myself, but I would expect it to be in the password settings of the compliance policy.
Regards, Peter
Hello,
Have anyone figure out which compliance setting is causing “User must change password at next logon” enabled ?
Hi Matej,
A few comments earlier, Guu mentioned that in his case it was a compliance policy causing that behavior.
Regards, Peter
Hi ,
I’ve assumed somebody knows the exact which settings causes problems.
Anyway, I’ve found old cmd : net user username logonpasswordchg:{yes | no}
But it fails with the:
System error 1938 has occurred.
Logon Failure: EAS policy requires that the user change their password before this operation can be performed.
Thank you, Matej! That’s really good information.
The complaince policy setting that caused it was ”require password”, IF i remember correctly. Ill get back tomorrow
Hello again,
Back at it again, seems like with recent updates to either OS or Intune, Accounts CSP has become broken for us.
It was working fine until recently, now when attempting, f.example, running Program “Run as Different User ” with that account returns errror – “Account restrictions are preventing this user from signing in. For example: blank passwords aren’t allowed, sign-in times are limited, or a policy restrictions has been enforced.”
Safe to mention that any policy restrictions hasn’t been made from our side.
Any ideas or anyone else is experiencing same issue?
Hi Janis,
I haven’t noticed that specific behavior.
Regards, Peter
Anyone solve for prompting to change password using this method.? Read the comments and didnt see if anyone had worked around this
Hi Miguel,
It’s often related to a compliance policy.
Regards, Peter
Great article and the steps you’ve outlined are working on a test machine.
Question: Thinking long-term, I’d like the ability to change the pw per our ISMS (would also be nice to change it when IT admins leave the organization). Do you know of a way to change the password of a local (admin) account in a cloud-only environment?
I’ve researched doing this using powershell via Intune but I hit my limitations getting the script to execute the actual pw change on the local machine. I also understand the Intune log on the local machine will have the password listed in plain text. So, I assume if using this method, the password needs to be hashed and packaged into a msi?
Thanks again, and hopefully MS will add the ability to change the local passwords!
J
Hi John,
Yeah, sadly there’s no easy way to adjust the password (at this moment).
Regards, Peter
Does anyone know what the integer would need to be to have the account just be in users? Not needing it in the admin account.
Disregard question. I saw in the beginning it is 1 for just user.
Correct, Sam. And yes it was in the beginning of the post 🙂
Hello,
This is working for me, however, I am unable to create another account with a different name besides “TestUser”
Shouldn’t it work if I change the “TestUser” name here to “WorkAdministrator” for example? This does not seem to create the account below.
OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/WorkAdministrator/Password
and
OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/WorkAdministrator/LocalUserGroup
Hi Dylan,
Yes, that should work with any other name. Did you try anything else (something shorter)?
Regards, Peter
hi!
I got the following error:
-2016281112 (Remediation failed)
Why doesn’t it work?
Hi Johan,
As mentioned in the post, I’m also receiving an error message after successfully creating the accounts.
Regards, Peter
I and others may be misreading your instructions.
./Device/Vendor/MSFT/Accounts/Users/TestUser/Password;
however, there is no “;” in the string, as can be seen in your screenshot.
For clarity on your instructions, i think the “;” can be removed. You end the line and use italics to identify what should be used, i don’t think the “;” helps, and just caused confusion for me.
Since in many programming languages ; is critical as a terminator, I didn’t question it when adding it into my string for Intune.
Thank you for the feedback, John!
Hi Peter,
I followed the steps you have mentioned and Local user account got created using intune but it is part of only Users group. Can It be made a part of Administrator group as well?
Regards,
Santosh
Hi Santosh,
That’s step 3c.
Regards, Peter
Peter, can we change password of existing local account?
Not at this moment, Biljana.
Thx for this great work around, I hope Microsoft will make this possible in the near future without the oma uri settings.
Just a quick question, I get the same error even if they are created, is there also a workaround to check if the user really is created ?
Not really, Sam..
Regards, Peter
This works great.
Except, I cannot un-join the domain with this local account unless I remove the “Users” from “Members of:” shown in the test users picture above under what would be TestUsers properties.
Is there a way where it will only add to the “Administrators” group?
I see that, integer wise…
1 – (Default) Users
2 – Administrators This optional setting allows the administrator to control the local user group of the new local administrator account.
Hi Dylan,
See step 3c. That will add the user to the local administrators group.
Regards, Peter
Hey Peter,
It works great adding the user to the administrator’s group, but the odd issue I’m having is, it’s also a member of the “users” group at the same time as shown in the picture. I actually have to remove the “users” group from the account leaving only a member of “administrators”.
While having this account as a member of both users and administrators, It will not allow me to un-join Azure AD with the credentials until its a member of “administrators” only.
Hi Dylan,
From an MDM perspective we sadly don’t have any other controls available to do additional configurations.
Regards, Peter
Hello,
Is there also a way to add the Local user to the Remote Desktop Users Group and check the box for Password never expires?
Hi Gaeme,
At this moment not by using the CSP.
Regards, Peter
You can use a powershell or command prompt to make group membership changes. For example –
net localgroup users AzureAD\full azure username /delete
Change out users for administrators or another local group name as needed. You can also change /delete to /add. I am using powershell scripts like the above which are running for me through intune without issue.
That is correct, Phil! Outside of using the CSP (and OMA-URI), you can always use PowerShell to achieve all the other stuff.
Regards, Peter
IT has been a year since your blog post and Intune still displays a remediation failed error message, while it actually works.
Peter, thank you for this write up, works exactly as specified. I have added this successfully and do get the remediation error as well. Since I have to pass a plain text password, is there an option to force a password change at first login? If not CSP then powershell or net user command? If I have to use powershell or net user then how can I be certain that the script runs after the account is created?
Hi Mark,
At this moment you would need to use PowerShell for something like that. Determining the order is currently “challenging”…
Regards, Peter
Thanks for this Peter, I am testing this in our environment and worked besides the known issues stated (remediation failed etc). My question is I noticed we cannot log into the created account until an Azure AD account has logged in first. Is that normal? Thanks again!
Hi Marc,
Is the configuration policy assigned to devices or users?
Regards, Peter
using the CSP the account gets created and is member of the local admins, however: the password is set to ‘must change at next logon’ – this is apparently a known issue, according to https://github.com/MicrosoftDocs/windows-itpro-docs/issues/1753
sigh…
That is correct, Siegmund!
Hi all,
I did have this policy working at first when I was in my initial test phase, now at some point it stopped working. When deploying the profile now I get in error and when you drill down its states under STATE DETIALS ‘
-2016281112 (Remediation failed)’ does anyone know why this might happen? Not found anything that helps me yet.
Hi Duncan,
Is it really not working? Reason for asking is what I mentioned in the post, that I’m getting an error even with a successful configuration.
Regards, Peter
Found the problem, it was my fault doh! On another policy to rename the admin account (which I had forgot I set ) I had already change the name of the Administrator account to the same name, silly mistake!
Thank you for the update, Duncan!
Peter thanks for another excellent article…I was successfully able to create the local user..but when I am trying to update the password of the local user it’s not working. Is there is a way to update the local user password??
Hi Avinash,
At this moment you can only set the initial password via OMA-URI.
Regards, Peter
Works like a charm, thanks! 🙂
When will local admin password expire with this solution. Doesn’t seem to set “password never expires”
Is it possible to set “password never expires” by OMA-URI too?
Thank you, Kimmd!
At this moment you cannot achieve that via OMA-URI.
Regards, Peter
this worked great. all the sudden it has stopped working. I haven’t changed my policy but it wont create the accounts anymore that it once was. I create a new policy and it still doesn’t work. anyone have any suggestions?
Hi Joe,
What are you seeing in the Event Viewer?
Regards, Peter
peter,
this is what i am seeing in event viewer its throwing an error.
MDM ConfigurationManager: Command failure status. Configuraton Source ID: (52972517-C3FC-493B-8229-CD9F6FD45B0D), Enrollment Type: (MDMDeviceWithAAD), CSP Name: (Accounts), Command Type: (Add: from Replace or Add), Result: (./Vendor/MSFT/Accounts/Users/TestAdmin/LocalUserGroup).
Hi Joe,
What are the differences with when it was still working?
Regards, Peter
Peter,
there was no difference once i had the policy working it was left alone and working until i just happened to check the user accounts for something and i notice the account wasn’t created anymore. i opened a case with MS they were able to reproduce the issue on other tenets and gave a workaround to use the PS script. which works but it stores the PS script in plain text in the log files which isn’t good. So it seems like maybe something broke on their end.
Hi Joe,
Yes, in that case there indeed seems to be something broken. And yes PS is an alternative, but not pretty.
Regards, Peter
Hi- I have done the configuration as suggested by above but during first time logon through admin account it’s asking password to change.
Can you please advice how to remove this setting in Azure Intune
Hi Ragav,
You cannot configure that at this moment via OMA-URI settings.
Regards, Peter
”
Hello,
This is working for me, however, I am unable to create another account with a different name besides “TestUser”
Shouldn’t it work if I change the “TestUser” name here to “WorkAdministrator” for example? This does not seem to create the account below.
i had the same problem. just create a brandnew profile. This worked for me
OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/WorkAdministrator/Password
and
OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/WorkAdministrator/LocalUserGroup”
Thank you for letting us know, Emanuel
Hi Peter,
thanks, this worked for me as well, but I am wondering how secure this is? Since the password is entered in plain text in Intune, does it also get sent to / stored on the client in plain text? I can’t find any information on how the connection from Intune cloud to client is secured (I assume it is, but how?) Do you have any info on this?
Hi Mathias,
A plain text password is probably never a good idea, no matter the connection between the device and the MDM provider. I haven’t found the plain text password on the device yet. And to answer your question: I don’t have any information to share about the connection more than published by Microsoft.
Regards, Peter
Hello,
I created user and add local admin rights but policy results -2016281112 (Remediation failed)
How can i fix this problem?
Hi Omer,
On what version of Windows 10 are you seeing that behavior?
Regards, Peter
Hi.
Thank you for this information. I am using it without problem, but I would like to configure it by adding the option that this local user’s password never expires. Would it be possible? What value should I add for it?
THANKS.
Hi Alvaro,
No, that’s sadly not possible via an OMA-URI. You would have to look at something like PowerShell to address that.
Regards, Peter
In order to avoid the expiration of the password of the local user and taking into account the information I have seen on this official page https://support.microsoft.com/es-es/help/2648402/you-cannot-change-an-expired -user-account-password-in-a-remote-desktop Would an OAM rule like this make sense?
./Device/Vendor/MSFT/Accounts/Users/TestUser/PasswordChangeEnabled
Setting Boolean value “False” ?
Hi Alvaro,
No that won’t help, because that’s not an existing OMA-URI. You can only configure OMA-URI’s that are available within a CSP.
Regards, Peter
Is there away to set the flags to uncheck change at next login or to check never expire
Hi Andy,
Not by using OMA-URI. That would require custom scripting.
Regards, Peter
Hi Peter,
Thanks this works well!
I was wondering now that we have a working admin account “testuser” how we could add a feature to this profile that removes the default administrator account or other accounts.
Thanks
PC
Hi PC,
This CSP only allows you to create the account.
Regards, Peter