This week is all about configuring Windows Package Manager. With the ability of standard users installing apps by using winget and with release of the new Microsoft Store apps within Microsoft Intune, the configuration of Windows Package Manager gets more and more important. Of course, it was already important to have a solid configuration, but with Windows Package Manager getting a more prominent role, a good configuration is required. The good thing is that with the introduction of Windows 11, version 22H2, Microsoft also introduced new configuration options for Windows Package Manager. Before, the configuration was limited to Group Policy settings and the settings.json file. Now there are also Configuration Service Provider (CSP) settings. The Policy CSP now contains nodes for the configuration of the Windows Package Manager. This post will have a closer look at the new configuration options, followed with the steps to configure the new settings. This post will end with experiencing the applied configurations.
Important: Keep in mind that completely disabling Windows Package Manager also seems to impact apps of the new Microsoft Store app type in Microsoft Intune that are deployed to the configured Windows device.
Note: The new nodes in the Policy CSP are not yet available for devices running different versions of Windows.
Introducing the Windows Package Manager configuration options
When looking at the configuration of Windows Package Manager, by using the Policy CSP, it’s important to be familiar with the configuration options. The Policy CSP contains new nodes that are all related to the Desktop App Installer, and used for configuring the Windows Package Manager. All of those nodes are ADMX-backed policies and with that those policies rely on existing ADMX templates that are available on the device. More specifically, the DesktopAppInstaller.admx. The table below provides an overview of all those new settings in the Policy CSP, and the root node for all the mentioned settings is ./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/.
| Setting and values | Description |
|---|---|
| EnableAdditionalSources Enabled: <enabled/><data id=”” value=””/> Disabled: <disabled/> | This policy setting controls additional sources provided for Windows Package Manager. When not configured, no additional sources will be configured. When enabled, additional sources can be added, by using AdditionalSources as data id and the sources as value, and those sources can’t be removed. When disabled, no additional sources can be configured by the user. |
| EnableAppInstaller Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls whether Windows Package Manager can be used by users. When not configured or enabled, users will be able to use Windows Package Manager. When disabled, users won’t be able to use Windows Package Manager. |
| EnableDefaultSource Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls the default source included with Windows Package Manager. When not configured, the default source will be and can be removed. When enabled, the default source will be available and can’t be removed. When disabled, the default source won’t be available. |
| EnableLocalManifestFiles Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls whether users can install packages with local manifest files. When not configured or enabled, users will be able to install packages with local manifests. When disabled, users won’t be able to install packages with local manifests. |
| EnableHashOverride Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls whether Windows Package Manager can be configured to enable the ability to override SHA256 security validation in settings. When not configured or enabled, users will be able to enable the ability to override SHA256 security validation. When disabled, users will not be able to enable the ability to override SHA256 security validation. |
| EnableMicrosoftStoreSource Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls the included Microsoft Store source with Windows Package Manager. When not configured, the Microsoft Store source will be available and can be removed. When enabled, the Microsoft Store source will be available, and can’t be removed. When disabled, the Microsoft Store source won’t be available. |
| EnableMSAppInstallerProtocol Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls whether users can install packages from a website that is using the ms-appinstaller protocol. When not configured or enabled, users will be able to install packages from websites that use this protocol. When disabled, users will not be able to install packages from websites that use this protocol. |
| EnableSettings Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls whether users can change their settings. The settings are stored inside of a .json file on the user’s system. When not configured or enabled, users will be able to change settings. When disabled, users will not be able to change settings. |
| EnableAllowedSources Enabled: <enabled/><data id=”” value=””/> Disabled: <disabled/> | This policy setting controls additional sources approved for users to configure using Windows Package Manager. When not configured, users will be able to add or remove additional sources. When enabled, only the sources specified, by using AllowedSources as data id and the sources as value, can be added or removed. When disabled, no additional sources can be configured by the user. |
| EnableExperimentalFeatures Enabled: <enabled/> Disabled: <disabled/> | This policy setting controls whether users can enable experimental features in Windows Package Manager. When not configured or enabled, users will be able to enable experimental features. When disabled, users will not be able to enable experimental features. |
| SourceAutoUpdateInterval Enabled: <enabled/><data id=”” value=””/> Disabled: <disabled/> | This policy setting controls the auto-update interval for package-based sources. When enabled, the number of minutes specified, by using SourceAutoUpdateIntervalInMinutes as data id and the number of minutes as value, will be used. When not configured or disabled, the default interval or the value specified in settings will be used. |
Important: The settings described in the table above are all only available in the scope of the device.
Note: The data id information of the settings described in the table above is available in the ADMX-file that is used to back all of these settings. That ADMX-file is the DesktopAppInstaller.admx.
Configuring Windows Package Manager
When looking at the actual configuration of Windows Package Manager, by relying on the new settings in the Policy CSP and using Microsoft Intune for the configuration, the configuration is actually pretty straight forward. In the future it will probably even become easier. For now the configuration of Windows Package Manager will still rely on using a custom device configuration profile. The following nine steps walk through the creation of that custom device configuration profile, with a few examples of often used configurations of the Windows Package Manager.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later as the platform for the configuration profile
- Profile type: Select Templates as the profile type for the configuration profile
- Template name: Select Custom as the template name for the configuration profile
- On the Basics page, specify a valid Name and optionaly a Description and click Next
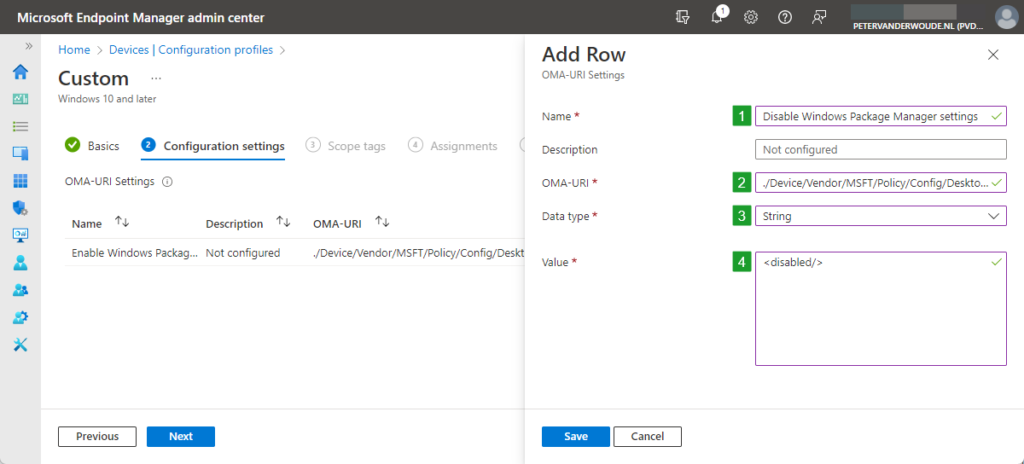
- On the Configuration settings page (see Figure 1), click Add to add rows for the following custom settings and click Next
- OMA-URI setting 1 – This setting is used to enable Windows Package Manager on the device
- Name: Provide a name for the OMA-URI setting to distinguish it from other similar settings
- Description: (Optional) Provide a description for the OMA-URI setting to further differentiate settings
- OMA-URI: Specify ./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/EnableAppInstaller as OMA-URI
- Data type: Select String as data type for the configuration of the value of the setting
- Value: Specify <enabled/> as value to enable the Windows Package Manager on the device
- OMA-URI setting 2 – This setting is used to prevent users from configuring Windows Package Manager settings
- Name (1): Provide a name for the OMA-URI setting to distinguish it from other similar settings
- Description: (Optional) Provide a description for the OMA-URI setting to further differentiate settings
- OMA-URI (2): Specify ./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/EnableSettings as OMA-URI
- Data type (3): Select String as data type for the configuration of the value of the setting
- Value (4): Specify <disabled/> as value to disable Windows Package Manager settings
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the required assignment and click Next
- On the Applicability rules page, configure the required applicability rules and click Next
- On the Review + create page, verify the configuration and click Create
Note: At some point in time these settings might become directly available within Microsoft Intune.
Experiencing Windows Package Manager
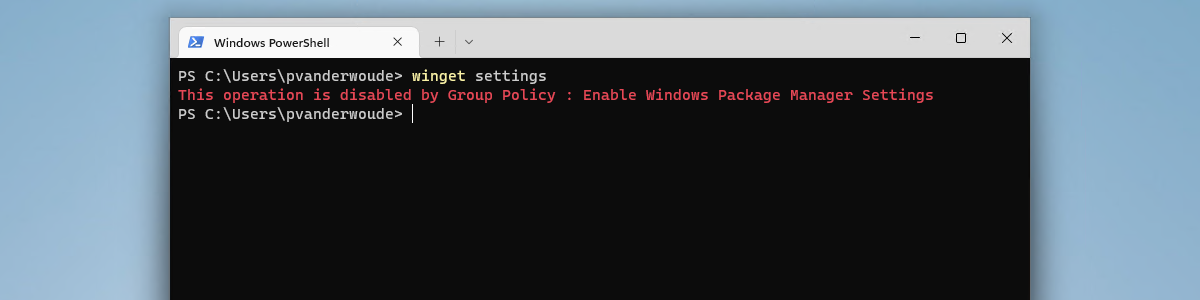
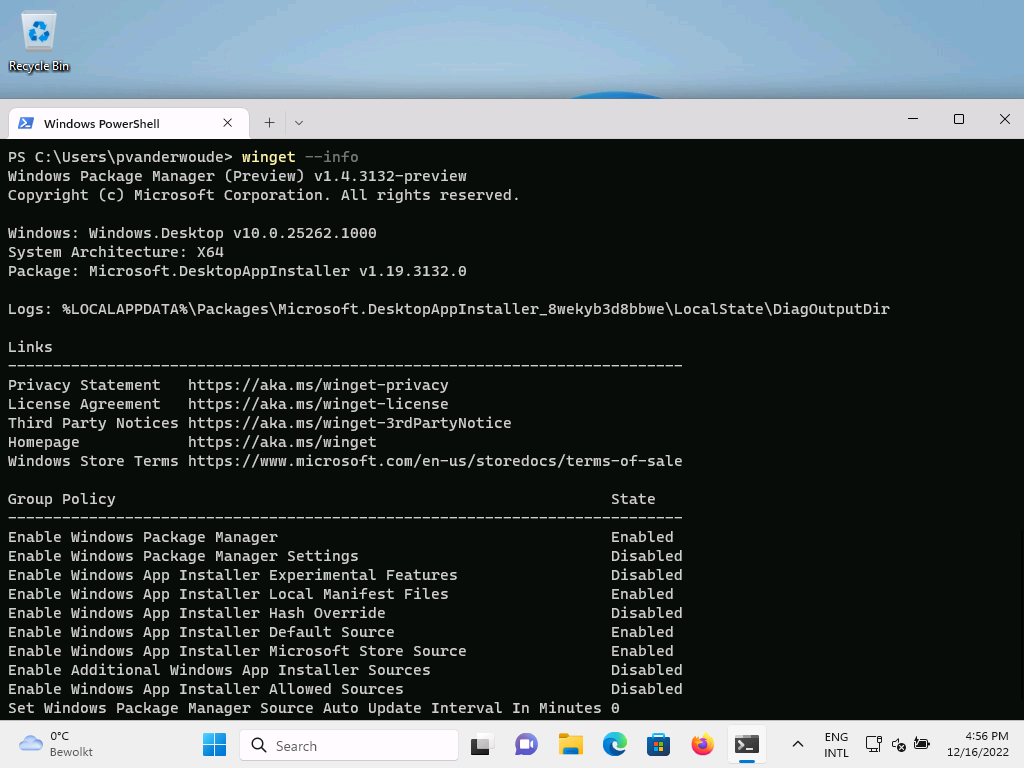
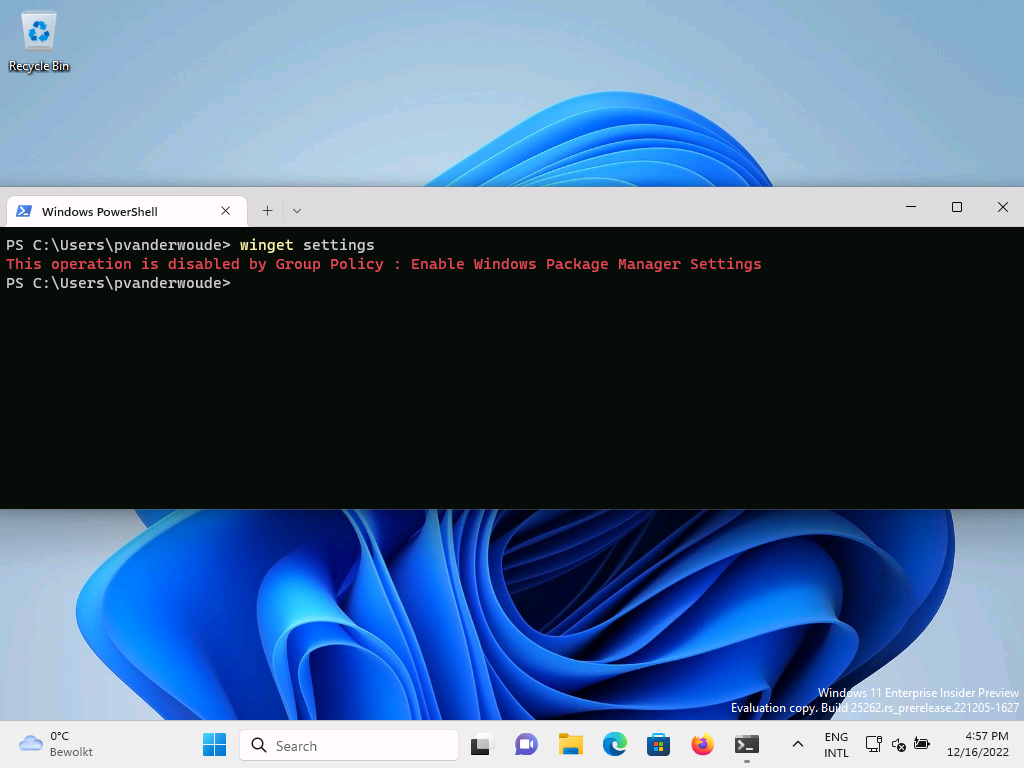
When looking at the experience with the configured Windows Package Manager, it’s all about the user experience. That can be experienced relatively easy on a Windows device that is managed by Microsoft Intune. The easiest is by looking at the experience with using the winget command line tool. Using the winget --info command provides an overview of the applied Group Policies settings (see Figure 2). That includes the ADMX-backed CSP settings. Using the winget settings command provides an overview of the impact of the specific configuration of disabling the settings of Windows Package Manager (see Figure 3). To prevent users from actually installing apps by using the winget command, think about also disabling the Microsoft Store Source and the Default Source.
Important: Keep in mind that completely disabling Windows Package Manager also seems to impact apps of the new Microsoft Store app type in Microsoft Intune that are deployed to the configured Windows device.
More information
For more information about configuring Windows Package Manager, refer to the following docs.
Hi there, I found importing the Admx also allowed for easy configuration.
Hi Nigel,
I like the native functionality more. But as with a lot of things, there are more roads to achieve the same goal.
Regards, Peter
Hi Peter!
Thanks for great article.
Just wanted to ask one thing. You say:
“To prevent users from actually installing apps by using the winget command, think about also disabling the Microsoft Store Source and the Default Source.”
When I disable those two, the software deployment of Microsoft Store apps gets blocked completely. Do you know how to avoid this?
What I want to obtain is to keep Microsoft Store, but as you suggest disable using winget command for users.
My config:
./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/EnableAppInstaller – Enabled
./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/EnableSettings – Disabled
./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/EnableMicrosoftStoreSource – Disabled
./Device/Vendor/MSFT/Policy/Config/DesktopAppInstaller/EnableDefaultSource – Disabled
Hi Piotr,
Yes, the challenge is the combination with Microsoft Intune. I’ve seen it work, but I’ve seen it fail a lot too (due crashes of the agentexecutor). There is an open item around that subject on Github.
Regards, Peter