This week I’ll open a new world of conditional access. The world of conditional access in Azure AD. I’ll open that world of conditional access by looking at conditional access for Yammer. Conditional access for Yammer cannot be configured through the Microsoft Intune administration console. However, that doesn’t mean that conditional access for Yammer doesn’t exist. The configuration of conditional access for Yammer is available through the Azure Management portal. In this post I’ll go into more detail about conditional access via Azure AD, the required configurations and the end-users experience.
Introduction
About a month ago Microsoft released conditional access policies as a preview feature in Azure AD for iOS, Android and Windows (Windows 7, Windows 8.1 and Windows 10, build 1607). These policies can help IT organizations with controlling data, by restricting access to managed devices only. Policies can be applied on a per-application basis to require that devices are managed by the IT organization and that devices are configured correctly.
In case that conditional access functionality sounds familiar, that’s possible. At this moment this conditional access functionality creates an overlap with the conditional access policies that can be configured through Microsoft Intune. Conditional access configurations done via Microsoft Intune will reflect to the configurations in Azure AD and vice versa. However, Azure AD already provides more configuration options and supports a lot more applications. Every application, that authenticates with Azure AD, is supported!
Configuration
The configuration of conditional access for Yammer contains two steps. The first step is to enable device access rules for Yammer and the second step is to configure the compliance policy.
Step 1: Enable devices access rules for Yammer
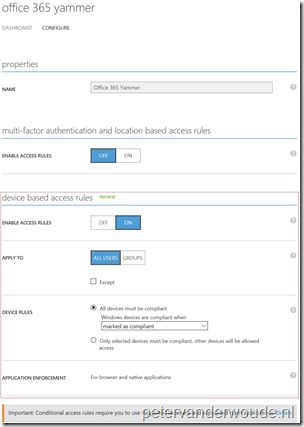
Let’s start with the first step, which is the configuration of the device access rule in the Azure Management portal. This configuration will make sure that all access attempts from a device that doesn’t meet the configuration will be denied. The configuration has to be done through the Azure Management portal and takes effect immediately after saving the configuration,
| Environment | Configuration |
| Microsoft Intune standalone and Microsoft Intune hybrid |
To enable conditional access for Yammer, switch ENABLE ACCESS RULES to ON and select with APPLY TO the users which the rules should apply. To make sure that all the devices must be compliant to access Yammer, make sure to configure the applicable platforms with DEVICE RULES and click SAVE. Note: With Yammer this configuration will be enforced for browsers and native applications. |
Step 2: Configure compliance policy
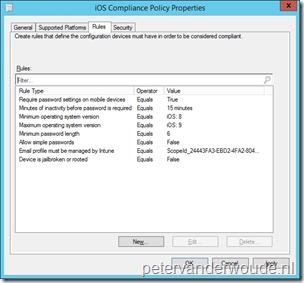
The second step is the configuration of the compliance policy in Microsoft Intune standalone and Microsoft Intune hybrid. This configuration part hasn’t changed and is still the right addition to require additional settings on a device. A compliance policy defines the rules and settings that a device must comply with in order to be considered compliant. The configuration of the compliance policy differs between Microsoft Intune standalone and Microsoft Intune hybrid. After creating the compliance policy, it can be deployed to users like any other policy. It’s not required to configure and deploy a compliance policy. When no compliance policy is configured and deployed, the device will automatically be considered compliant.
| Environment | Configuration |
| Microsoft Intune standalone |
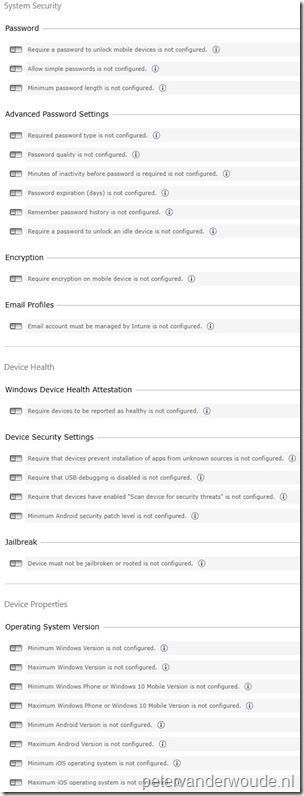
To configure a compliance policy, choose, based on the requirements, between the applicable available Password, Advanced Password Settings, Encryption, Email Profiles, Windows Device Health Attestation, Device Security Settings, Jailbreak and Operating System Version settings. |
| Microsoft Intune hybrid |
To configure a compliance policy, choose, based on the requirements, during the Create Compliance Policy Wizard the Supported Platforms and choose between the applicable Password, Advanced Password Settings, Encryption, Email Profiles, Windows Device Health Attestation, Device Security Settings, Jailbreak and Operating System Version Rules. |
Note: Compliance policies can be used independently of conditional access. When used independently, the targeted devices are evaluated and reported with their compliance status.
End-user experience
After the configuration of the device access rule and the compliancy policy is completed, it’s time to look at the end-user experience. An enrolled and compliant device will give the end-user the normal experience. A not enrolled device, or a not compliant compliant device, will give the end-user a message based on the status of the device, when the end-user is trying to access Yammer. Those messages are shown below, using an iOS device using the default browser as an example.
| Not enrolled | Not compliant |
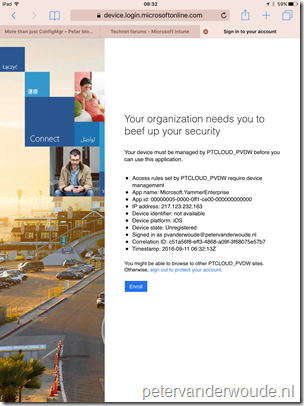 |
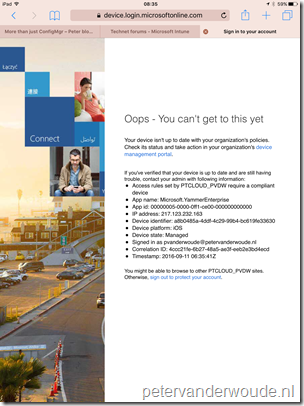 |
More information
For more information about conditional access, related to applications in Azure AD and compliance policies, please refer to the following articles:
- Conditional access support for applications: https://azure.microsoft.com/en-us/documentation/articles/active-directory-conditional-access-supported-apps/
- Azure Active Directory conditional access: https://azure.microsoft.com/en-us/documentation/articles/active-directory-conditional-access/
- Azure Active Directory Conditional Access technical reference: https://azure.microsoft.com/en-us/documentation/articles/active-directory-conditional-access-technical-reference/
1 thought on “Conditional access for Yammer”