This week another (short) blog post about Windows AutoPilot. More specifically, about automatically assigning a Windows AutoPilot deployment profile to Windows AutoPilot devices. That makes it a lot easier for administrators, as this prevents the administrators from potentially forgetting to assign the deployment profile to newly imported devices. Great improvement. Also, I have to say that this subject is documented pretty good, but it could be easier to find. This post is mainly for creating awareness regarding this subject. I’ll provide the options regarding to grouping Windows AutoPilot devices and I’ll show how those options can be used to create a dynamic group.
Options
Let’s start by having a look at the configuration options regarding the grouping of Windows AutoPilot devices. The imported Windows AutoPilot devices are pre-created in Azure AD and, during that creation process, a few values are automatically set for those devices. Below is an overview of those different values.
| Value | Devices | Explanation |
| [ZTDId] | All Windows AutoPilot devices | A unique value assigned to all imported Windows AutoPilot devices |
| [OrderID]:{YourOrderId} | All Windows AutoPilot devices with a specific order Id | An optional Id that can be specified when importing Windows AutoPilot devices |
| [PurchaseOrderId]:{YourPurchaseOrderId} | All Windows AutoPilot devices with a specific purchase order Id | An Id that is set by the OEM when importing Windows AutoPilot devices |
Those different values can be used to create dynamic device groups within Azure AD. Below is an overview of the required queries per grouping of Windows AutoPilot devices.
| Devices | Query |
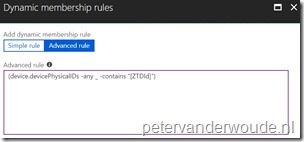
| All Windows AutoPilot devices | (device.devicePhysicalIDs -any _ -contains “[ZTDId]”) |
| All Windows AutoPilot devices with a specific order Id | (device.devicePhysicalIds -any _ -eq “[OrderID]:{YourOrderId}”) |
| All Windows AutoPilot devices with a specifc purchase order Id | (device.devicePhysicalIds -any _ -eq “[PurchaseOrderId]:{YourPurchaseOrderId }”) |
Note: These values can be seen by simply using Graph Explorer, querying https://graph.microsoft.com/v1.0/devices and looking for the physicalIds value.
Configuration
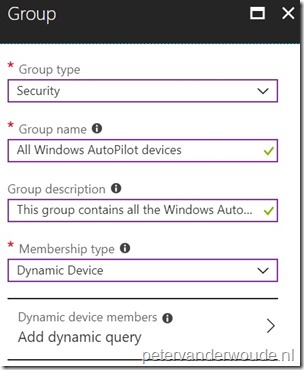
Let’s continue by having a look at how to use these different values and queries for actually grouping all Windows AutoPilot devices. The following 3 steps walk through the creation of a dynamic device group that can use the different queries mentioned earlier.
| 1 | Open the Azure portal and navigate to Intune > Groups or navigate to Azure Active Directory > Groups to open the Groups – All groups blade;; |
| 2 | On the Groups – All groups blade, click New group to open the Group blade; |
| 3a |
|
| 3b |
Note: The example on the right is showing the query for all AutoPilot devices. |
Once the dynamic device group is created it can used for assigning Windows AutoPilot deployment profiles. That enables the administrator to automatically assign a Windows AutoPilot deployment profile to all Windows AutoPilot devices.
Result
Let’s end this post by having a look at the results. Below, on the left, is a quick overview, via Microsoft Graph, about the device information of CLDCLN879139238. That shows the name of the device and the value related to all imported Windows AutoPilot devices. Below on the right is an overview of that same device, showing it as a member of the earlier created dynamic device group.
 |
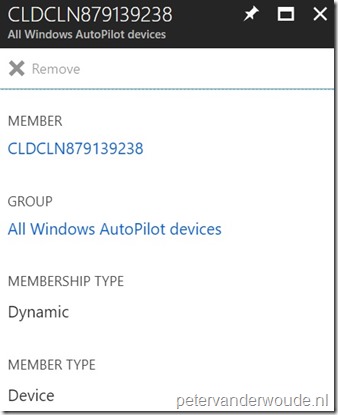 |
More information
For more information regarding the latest Windows AutoPilot features and the configuration steps, please refer to the following articles:
Hi Peter,
I’m getting the following error that invalid characters were found in the rule:
Dynamic membership rule validation error: Invalid characters found in the rule.Invalid characters found in the rule: “ ”
I’ve tried this on several tenants, do I need to activate Graph before I can use this query?
Hi Michel,
That’s a current issue with my blog that it messes with special characters like the double quotes. Simply paste the query and manually redo the quotes, as a workaround.
Regards, Peter
Hi Peter, great post. I think the website layout messed up the quotes in the membership value. When I copy them straight of your website and paste them into my dynamic rule, the group will not be created due to an error: Invalid characters found in the rule. Invalid characters found in the rule: “ ”
(device.devicePhysicalIDs -any _ -contains “[ZTDId]”) <- Not working
(device.devicePhysicalIDs -any _ -contains "[ZTDId]") <- Works
Notice the slight difference in the quotes…..
Hi Jan,
Yes, that’s a “known” issue. I still need to make time to fix that somehow.
Regards, Peter
Thanks Peter and Jan! I completely missed this!
Is it possible to add physicalIds [OrderID] afterwards?
So devices are already enrolled by autopilot but without OrderID. Can this be added trough Microsoft Graph?
Hi Marco,
No a 100% sure, should test this, but if I’m not mistaken the information of a device will be updated when the device already exists.
Regards, Peter
Hi Peter,
I have added a windows 10 Surface Pro device to Autopilot through importing the .csv which shows up under Windows AutoPilot devices but doesn’t appear when I want to manually assign the device to a device group by searching its serial number. Any thoughts on this?
Hi Jenny,
It could take a while for the devices to show up. There has been a time that it could take up to 72 hours, but that should not be the case anymore.
Regards, Peter
What query do you use with the Microsoft Graph to get the device information?
Hi Craig,
That’s just a simple query for device information (nothing fancy).
Regards, Peter
Hi Peter,
I’ve found that after Autopilot reset on a Windows 10 device that the ZTDID value no longer appears in the physicalIds for the device under the GraphAPI – and therefore cannot be targeted with the dynamic device group query for Autopilot devices.
Just wondering if you’ve found the same? And if there is another method to create a dynamic device group for Autopilot devices?
Hi Jordan,
I don’t recall seeing that behavior, but I also haven’t looked at that recently. It would beat the purpose of using Autopilot Reset. I’ll try one of these days again.
Regards, Peter
I’ve just tried to create the dynamic groups, and it doesn’t like those statements. Just found these on the MS site
(device.devicePhysicalIDs -any (_ -contains “[ZTDId]”))
Apparently needs the extra brackets
Thank you for the information Chris.
Regards, Peter
Hi Peter.
I want to make a dynamic group with
(device.devicePhysicalIds -any (_ -eq “[PurchaseOrderId]:123456789”)) and
(device.devicePhysicalIds -any (_ -eq “[PurchaseOrderId]:012345678”))
But every time when adding the second rule I get an syntax error, is it not posible to ad 2 almost the same lines?
Harmen
Hi Harmen,
I had no problems using your query (besides adjusting the quotes).
Regards, Peter
Hoi Peter,
Ik denk dat je https://unicode-table.com/en/201D/ gebruikt ipv https://unicode-table.com/en/0022/
Zo staat het inderdaad ook bij Microsoft
https://docs.microsoft.com/en-us/mem/autopilot/windows-autopilot-hybrid#create-a-device-group
Alvast bedankt voor de goede informatie. Top!
Hi Perry,
Yes, the WordPress theme automatically changes the quotes in many scripts…
Regards, Peter