This week is still all about conditional access. More specifically, the recently introduced feature to create conditions based on the use of legacy authentication (including older Office versions), which is currently still in preview. By now, I’ve done my fair share of posts regarding blocking legacy authentication (see for example here and here), but now it’s literally getting super easy. And no need for AD FS anymore. This helps with easily closing another backdoor, as previously legacy authentication simply bypassed any conditional access policy. In this post I’ll walk through the required configurations followed by the end-user experience.
Configuration
Before going through the configuration let’s start with a quick reminder about legacy authentication. Very simplistically said, legacy authentication is basic authentication that uses a single authentication factor in the form of a username and password and cannot force a second authentication factor (think about protocols like, POP3, IMAP, SMTP, MAPI and EWS and apps like, Office 2010). As I have no need for legacy authentication in my environment, I will block all legacy authentication to my apps. The following seven steps walk through the simple configuration to create a conditional access policy that blocks the access to all cloud apps for all users when using legacy clients.
| 1 | Open the Azure portal and navigate to Intune > Conditional access > Policies or to Azure Active Directory > Conditional access > Policies; |
| 2 | On the Policies blade, click New policy to open the New blade; |
| 3 | 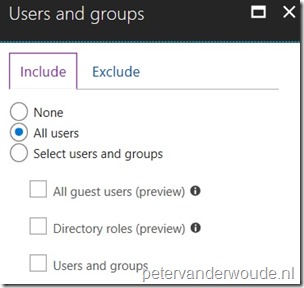 On the New blade, select the Users and groups assignment to open the Users and groups blade. On the Users and groups blade, select All users and click Done; On the New blade, select the Users and groups assignment to open the Users and groups blade. On the Users and groups blade, select All users and click Done; |
| 4 | 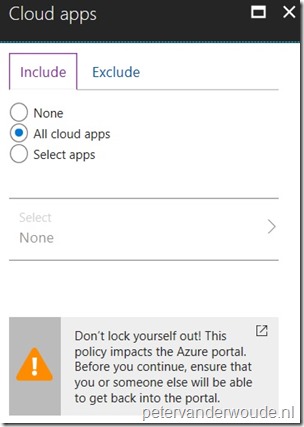 On the New blade, select the Cloud apps assignment to open the Cloud apps blade. On the Cloud apps blade, select All cloud apps and click Done; On the New blade, select the Cloud apps assignment to open the Cloud apps blade. On the Cloud apps blade, select All cloud apps and click Done; |
| 5 | 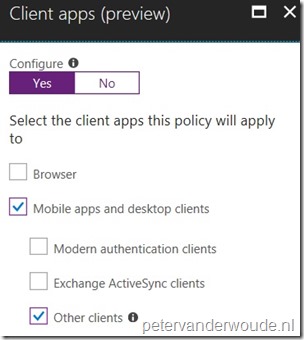 On the New blade, select the Conditions assignment to open the Conditions blade. On the Conditions blade, select Client apps (preview) to open the Client apps (preview) blade. On the Client apps (preview) blade, click Yes with Configure, select Mobile apps and desktop clients > Other clients and click Done and Done; On the New blade, select the Conditions assignment to open the Conditions blade. On the Conditions blade, select Client apps (preview) to open the Client apps (preview) blade. On the Client apps (preview) blade, click Yes with Configure, select Mobile apps and desktop clients > Other clients and click Done and Done; |
| 6 |
Note: Make sure that there are no apps within the environment that still need basic authentication, as this configuration will block all of it. |
| 7 | Open the New blade, select On with Enable policy and click Create; |
Note: It can take up to 24 hours for the policy to take effect.
End-user experience
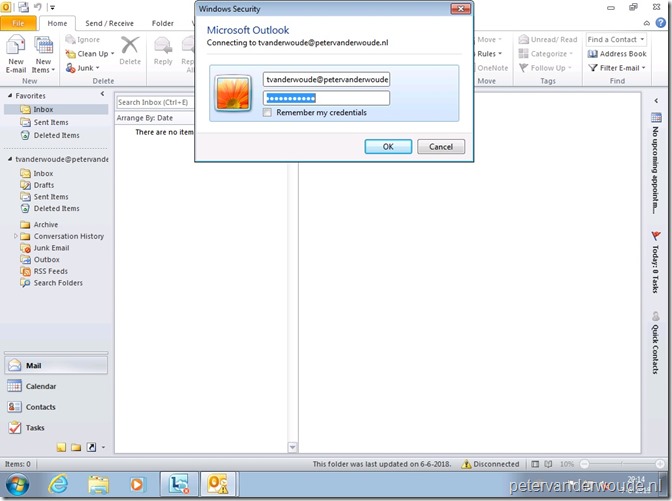
One of the best use cases is an old Office version. Office 2010 and the default configuration of Office 2013, both use basic authentication. Office 2016 and later use modern authentication by default. Due to the way basic authentication works the end-user experience is not pretty and will not be pretty. Below is an example of the end-user experience when using Outlook 2010 for connection to Exchange Online. As mentioned, it’s effective and not pretty.
More information
For more information about conditional access and device state, please refer to this article about Conditions in Azure Active Directory conditional access | Client apps.

Hi
I just tried to create the CA as you instructed. It’s just that if I choose All Users and All Cloud Apps and set Access Control to Block, I get error message
“Policy configuration not supported. Review the assignments and controls.”
Error message is a link to AAD documentation
https://docs.microsoft.com/en-us/azure/active-directory/active-directory-conditional-access-best-practices#what-you-should-avoid-doing
which says that one should avoid All User, All Cloud Apps with Block. It seems that CA doesn’t even accept that kind of CA.
Hi Livo,
That’s new behavior and I’m seeing the same. You can work around it by for example excluding your global administrators.
Regards, Peter
So what happens if we want modern auth enabled with CA for EXO where 80% users are on o2016 but remaining 20% are still on outlook 2010?
Hi Mikke,
You mean if you’re blocking legacy authentication? If so, that would prevent those Outlook 2010 users from accessing EXO.
Regards, Peter
Same, the policy doesnt seem to be support anymore.
Error: “Policy configuration not supported. Review the assignments and controls.”
Hi Gd,
Correct. You need to make a differentiation nowadays. For example target a specific user group.
Regards, Peter
Hi Peter,
I have a CA policy to block any connection that comes from public Internet (for some accounts), so I only configured the Location blade to all locations except our trusted IPs and I’m “blocking” for All Cloud apps. One account that has this CA policy applied was accessed from internet using legacy protocols. Should I create an additional policy to block specifically “others clients”? is this an expected behavior?
Hi Jean,
When configured correctly, that should not be necessary. Also, what’s the legacy protocol that you’re using?
Regards, Peter
Hi Peter,
Thanks for your replied. I just realized that in the “Client apps” blade, if it is not configured, there is a message that says “This policy only applies to browser and modern authentication apps. To apply the policy to all client apps, enable the client app condition and select all the client apps.” So, I configured it for all client apps and I’m testing it out. I’m testing SMTP and ActiveSync protocols.
Regards,
Jean Carlos
Thank you for the update, Jean!