This week a new blog post about Windows Autopilot. More specifically, Windows Autopilot self-deploying mode. Autopilot self-deploying mode is really useful for devices that are function specific, like for example kiosk devices. The biggest benefit is that a device with a wired network connection (with Internet) can be completely configured without any user interaction. Simply connect the device to the wired network and power it on! Real zero touch provisioning! In this post I’ll provide the configuration steps to create that experience, followed by some known errors and the end-user experience.
Configuration
Let’s start with a few important requirements and limitations:
- The device must run Windows 10, version 1809 or later;
- The device can only be Azure AD joined (Active Directory join is not supported);
- The device must be a physical device with TPM 2.0 (virtual machine is not supported);
Now let’s continue by looking at the available configuration options. In this case I’ll look at the different available configurations options and the related impact of those configuration options. The following four steps walk through the steps to get create a new Windows Autopilot self-deploying profile (including the available settings). That deployment profile can be assigned to an Azure AD group that contains devices.
| 1 | Open the Azure portal and navigate to Microsoft Intune > Device enrollment > Windows enrollment to open the Device enrollment – Windows enrollment blade; |
| 2 | On the Device enrollment – Windows enrollment blade, select Deployment Profiles in the Windows Autopilot Deployment Program section to open the Windows Autopilot deployment profiles blade; |
| 3 | On Windows Autopilot deployment profiles blade, select Create profile to open the Create profile blade; |
| 4a |
Note: The Self-Deploying (preview) deployment mode, defines the available Azure AD settings and the available out-of-box experience (OOBE) settings. |
| 4b |
On the Out-of-box experience (OOBE) blade, provide the following information and click Save.
|
| — | 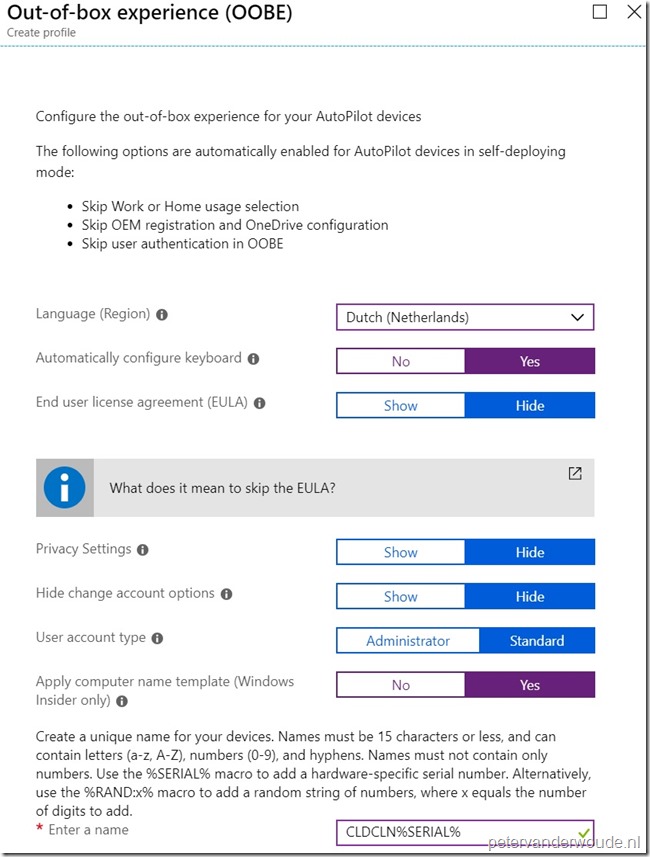 |
Note: The Autopilot settings can only be downloaded when a network connection is in place. That’s the reason why a wired network connection should be in place. When a wired network connection is not available, it’s required to configure the region, the keyboard and a Wi-Fi.
Known errors
During the testing of Windows Autopilot self-deploying, I ran into multiple errors. More information about an error can always be found in the Event Viewer, at Application and Services Logs > Microsoft > Windows > Provisioning-Diagnostics-Provider > AutoPilot (thank you for the reminder Sandy!). The errors that I’ve seen on screen are documented and explained in the table below. If you’ve seen errors that are not on this list, let me know and I’ll add them.
| Error | Description |
| 0x800705B4 | This error means that the device is either a virtual machine, or does not have TPM 2.0, and is not capable of running Autopilot self-deploying. |
| 0x801c03ea | This error means that the device is TPM 2.0 capable, but that the TPM still needs to be upgraded from 1.2 to 2.0. |
| 0xc1036501 | This error means that the device cannot do an automatic MDM enrollment, because there are multiple MDM configurations in Azure AD. |
End-user experience
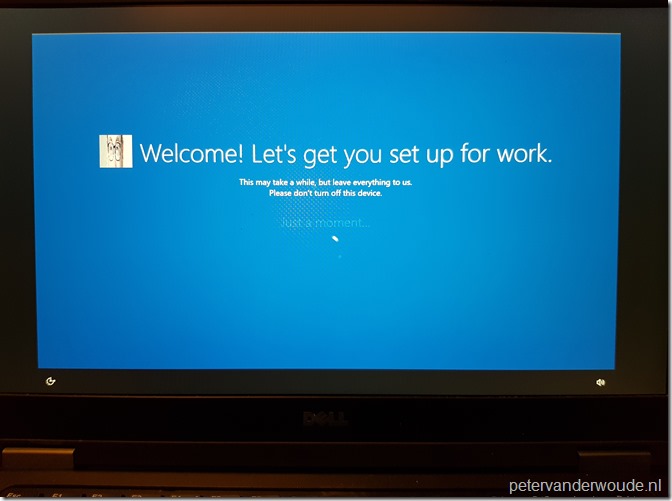
As always, let’s end this post by having a look at the end-user experience. The end-user experience will provide a welcome message (see below) after receiving the Autopilot deployment profile and an automatic restart. An easy differentiation between the Autopilot user-driven experience and the Autopilot self-deploying experience, besides the interaction, is the logo that’s used. At this moment the Autopilot user-driven experience uses the square logo of the Azure AD company branding and the Autopilot self-deploying experience uses the banner logo of the Azure AD company branding.
Note: From and administrator perspective, an Autopilot self-deploying device can be easily recognized by the Management name of the device. It contains a GUID instead of a username.
More information
For more information about enrolling Windows devices by using Windows Autopilot self-deploying mode, please refer to the documentation named Windows Autopilot Self-Deploying mode.
Great post Peter. Good to mention you need wired connection otherwise internet connection comes too late to Connect to intune 🙂
Was thinking how and why i got the keyboard and region questions 🙂
Thank you, Rkast! There is already a note regarding that below the configuration.
Regards, Peter
Sorry i mean (typo) , good you mentioned it Peter 🙂
No problem, Rkast!
I am getting 0x800705B4 still with 1809 on a Lenovo M920q with TPM 2.0. Any ideas?
Hi Nigel,
Did you check the Event Viewer for some more details?
Regards, Peter
Hi there Peter,
I exported the event logs and don’t actually see the TPM error event #171 as described here : https://docs.microsoft.com/en-us/windows/deployment/windows-autopilot/troubleshooting
I do see event #153 ‘AutoPilotManager reported the state changed from ProfileState_Unknown to ProfileState_NotProvisioned.’
To set the context – I am testing this with Offline Autopilot – I have an autounattend.xml placing the json .
Any other events of interest I should be looking for in your experience?
Hi Nigel,
Did you already successfully test it without trying an offline Autopilot?
Regards, Peter
Hey there,
Same results with online autopilot.
Some further event logs now after a few re-tries – Event 176 – MSA TPM keystate has been updated. New server state = 3, new client state = 6, followed by 152, 182, 150, 183, and finally 177 ‘TPM attestation retry is being attempted. Current retry attempt 3 of 3 maximum’. This is a modern TPM 2.0 device as stated.
online still creates the same results, I’ve tested on a Surface Laptop, M920q, and a T450s now. I have an issue with MS now – https://github.com/MicrosoftDocs/windows-itpro-docs/issues/2360
Unsure what I am missing….
Hi Nigel,
Did you already create a (free) support ticket with Intune support?
Regards, Peter
Yes I did – thank you for your time on all this. Microsoft basically told me it’s not fully supported in 1809 and is still a preview feature. They said to try the latest Preview build.
Hi Nigel,
Not a problem. Did you already manage to test it with the latest Insider Preview build?
Regards, Peter
Yes – but not with an Offline JSON file as I was hoping 🙂
Thanks again
Thank you for letting us know, Nigel! I was also referring to testing it with an offline JSON file 🙂
Hello Peter, Nigel
I also run into trouble with Self Deploy, see my post on the issue that Nigel opened with MS:
https://github.com/MicrosoftDocs/windows-itpro-docs/issues/2360#issuecomment-453153411
Any idea what is required to have the TPM Attestation feature supported, after a fresh install of Win 10 1809?
Thanks for any hint. Werner
Wenrer
Hi Werner,
Not sure what the difference would be between those Windows version in relation to the TPM attestation. Did you already create a support case with Intune support?
Regards, Peter
I am getting error code: Registering your device for mobile management (Failed: 6, 0x80180005). Using a Surface Pro (2017 model aka Pro 5 and also tried a Pro 4) both failed with the exact same error. These are not hybrid joined, straight up Azure AD AutoPilot with a bare bones 1903 image. It works just fine with a user driven profile but I want to set this up with the self deploying profile as these device will be shared among many so I would like to take advantage of the shared device guest mode the self deploying profile offers. Any ideas?
Hi Andrew,
Do you get some more details in the Event Viewer?
Regards, Peter
The event viewer recorded zero events in the AutoPilot folder. I did tell it to collect the logs and I have those but have no way of viewing them or understanding them if I was able to view them most likely.
What about the DeviceManagement event logs, Andrew?
I am getting registering your device for mobile device failed 6, 0x80180005 error. Windows 10 build 1809.
TPM 2.0
Hi Peter,
Would you be able to answer the questions that I asked to Andrew earlier?
Regards, Peter
So just to follow up. I reset the device and let it try one more time and it failed again but later on in the setup. I powered off and back and it tried one more time and completed without fail. Looks like Microsoft has some bugs still to work out. I have one working exactly like I needed it to after about 20 attempts and about a week of trying…..
Thank you for the update, Andrew!
I’m getting the same 0x80180005 error on an HP EliteBook x360 1030 G2 with TPM 2.0 and 1903.
Frustrating, especially with the lack of meaningful errors in Intune.
Hi Fergus,
Also nothing in the Event Viewer?
Regards, Peter
Tbh I’m not sure how I get any events if on failure it forces me to reset the laptop!
Clearly I’m missing something, so prepared to be schooled, but I selected “Save logs” (or whatever the button is) and it seems like it saved a cab file from the successful (user-driven) deployment that happened after the failure.
However, I did ask Mike Niehaus and he said it’s a failure to enroll into InTune (as opposed to the AAD join), so I wonder if the fact that in “AAD – Mobility (MDM and MAM) – Configure” I am allowing only a specific user group to autoenroll might have something to do with it.
Going to test it tomorrow.
Hi Fergus,
You can use Shift+F10 to start a Command Prompt, which you can use to start Event Viewer (or anything else).
Regards, Peter
We are getting that same failed 6, 0x80180005 error using self-driven autopilot and are stuck on it. There are four errors in the event log that repeat over and over.
MDM Enroll: Server context (dca58854-66bc-42e8-8082-8b089122133a).
MDM Enroll: Server Returned Fault/Code/Subcode/Value=(EnrollmentServer) Fault/Reason/Text=(ZTD Profile was not found).
MDM Enroll: Failed to receive or parse certificate enroll response. Result: (Unknown Win32 Error code: 0x80180005).
MDM Enroll: Failed (Unknown Win32 Error code: 0x80180005)
Not sure if we’re missing something or what. The device joins Azure AD fine but doesn’t enroll in Intune. We did manage to get one of these devices enrolled into Intune manually and this error doesn’t occur if the device is already enrolled. We plan to open a case with Microsoft as well but if you have any idea on this we’d appreciate the help!
Hi Bryan,
It almost sounds like the profile is not correctly assigned to the device.
Regards, Peter
Hi Peter,
Thanks for the reply. Just wanted to let you know we figured this out. In our case there were a couple of issues that solved this for us.
First, up until this point we were using the Microsoft Store for Business to assign a profile to our devices. After reviewing the Microsoft documentation for a self-deploying autopilot profile it says that this is not supported and to assign the profile through Intune. After doing this we got further but a different error showed up.
The second error occurred because there was a policy to hybrid-join devices that was assigned too broadly. After looking around I found either hybrid join isn’t currently supported for self-deploying mode or there was an issue with hybrid join and using a variable (like %SERIAL%) for naming a device. I haven’t yet had a chance to see which of these was causing the issue. For our devices AAD-only join was ok so we narrowed the scope of the hybrid join profile and after that everything started working perfectly.
Hope that helps someone!
Thank you for the information, Bryan!
Hi Peter, great blog! Could you please confirm that the option “Privacy settings = Hide” is not there anymore for “self deploying” mode? Keep getting this screen every time running self deploy, a little frustrating.
Thank you, Trond!
Yes, I can confirm that I’m not seeing that option anymore (see also for another confirmation: https://oofhours.com/2019/10/01/inside-windows-autopilot-self-deploying-mode/)
Regards, Peter
I have a Windows 10 1909 installed on HP G2 device with TPM 2.0. The device fails with the error 0x800705B4 Tried to reset the device multiple times but without luck. When I had collected the logs interestingly enough that I found no errors in neither events. I checked the following events:
– microsoft-windows-devicemanagement-enterprise-diagnostics-provider-admin
– microsoft-windows-moderndeployment-diagnostics-provider-autopilot
– microsoft-windows-provisioning-diagnostics-provider-admin
Unfortunately with no luck. I found this TpmHliInfo_Output file, and I thought for a second let me check the TPM. What’s interesting about this file is that I found that no valid EK Cert found. I have used a different wire that connects the PC directly to the internet. The deployment succeeded. I have then added the manufacturer’s domains and subdomains to the whitelists to allow the access to the manufacturer’s domains. This has surprisingly resolved the issue. I tested it on anothr machine and it worked.
Thank you, Eronad, that is great information!
Regards, Peter
@Bryan Haakensen; Where did you find the hybrid-join policy? I’m getting the exact same “failed 6, 0x80180005” error, with the same event viewer logs. Removed the variable in the computer name, and also deleted the computer from the Business store and added it again through InTune. I’m still stuck and kinda clueless on whats going wrong. 😉
Hi Ben,
I think Bryan is referring to a domain join profile.
Regards, Peter
Same here, Autopilot runs, user can login, all apps are installed, but after a reset a black screen.
Hi Ronald,
And also after a restart it works again?
Regards, Peter
No, I even did a new MDT run without drivers. Everything is fine, apps are installing, policies applied but after the first restart as a user, the screen is black and nothing is happening. HP Desktop, Windows 1909, MDT with Windows Updates applied, Autopilot Selfdeployment as in this article
Okay Ronald, so if I’m understanding it correctly the device is completely useless after an Autopilot reset?
Regards, Peter
Yes Peter, after the first restart a blank screen appears. Hard drive LED is blinking in a slow pace. Even after 24h no signs of improvements
Hi Ronald,
That’s quite bizarre. I haven’t had those experiences yet. Have you contacted Microsoft already about this behavior?
Regards, Peter
I removed Windows updates from the MDT Task Sequence and skipped a restart. Things seem to be better now. No more black screens
Hi Ronald,
That’s actually good news, but that still doesn’t feel stable.
Regards, Peter
I’ve got 400 or so self deployed devices out in the wild right now. They work well, but seem to have an issue picking up apps deployed as required to the device. Some install, some don’t seem to apply. No logs or anything. I use them on a user driven deployment and they work fine.
It weird.
Hi Jason,
Is there nothing in common? App deployment type, device type, log information, etc.?
Regards, Peter
Great post. Really helped me get my Intune Autopilot deployment setup and working.
I’ve been using it for a few months now without any issues but yesterday I Autopilot’d 5 devices and every single one, after going through the deployment stages, went to a Black screen with just the mouse cursor.
I’ve already run the process on 15 devices last week without issue so I’m reasonably confident it’s nothing to do with the configuration. Every device is a Surface Pro 4 so it cannot be a hardware spec related issue either!
I tried reboots, different combinations of button presses etc (as suggested by a comment above) but it had no effect. I did find though that by initiating an Autopilot Reset from the device screen in Intune, the device then picks up and carries on.
I just thought I’d post this in case anyone else has the issue… or finds the cause! Thx
Thank you for sharing that information, Mike!
I have today found that you can just hit the ‘Sync’ button for the device rather than the ‘Autopilot Reset’ option.. this saves a bit of user time.
Thank you for that addition, Mike!
Peter,
Forgive me, I’ve just realised I forgot to thank you for your earlier replies! Very bad form. 🙂
all the best,
f.
Not a problem, Fergus!
@Mike Halsey
I just got some Surface devices (pro 7/laptop 3) and both have the black screen after the user gets the machine and completes the MFA part (this is a device with White Glove).
Shutting down the machine and turning it on again will load Windows and you can logon and complete the enrollment.
Hi Patrick,
Do you see anything in the Event Viewer?
Regards, Peter
Hi Peter,
because a hard shutdown worked for me, I did some other checks first before I was able to continue with this issue.
So I did not check anything locally yet, but I found out that there are possible reasons why this error can occur. Like when there is a Interactive logon message (and we have this) or a custom Startmenu layout XML.
Also MS says that some DeviceLock settings can give ESP issues.
When I skip the white glove key-combo, the machine will not hang.
I will try to do something with the Interactive Logon message first and run a 2nd machine, and check the logs on the first “sealed” machine.
Peter,
maybe you can edit my last post and add this URL in it:
https://microsoftintune.uservoice.com/forums/291681-ideas/suggestions/40310866-support-for-the-logon-message-added-in-the-intera
I guess this is my issue (assumption:))
Ok for me it is solved now by disabling the Interactive Logon Message.
Thank you for all the information, Patrick!
We moved the setting from a Device assigned profile to a user assigned profile (with only the message in it, so other settings are still based for the device).
Thank you for the update, Patrick!
Hi Peter,
Thank you for your great blog, it has helped me many times.
Now however, I have an issue that I haven’t managed to solve yet:
I want to self-deploy Windows 10 (en-US language), but since the computers have a Swedish keyboard, this needs to be configured. I have tried everything i can think of, but the devices are still configured with a US-layout.
I have a powershell script that sets the keyboard layout for the current user on login, but the Windows login screen is still having the US-keyboard.
Letting the user choose the keyboard layout is not an option (the computers are lab classroom computers at an university). As we have a large number of international students, w we can not use Swedish only either.
Do you know a way to solve this? Any suggestions are welcome!
Hi Jasper,
When automatically configuring the keyboard layout, it will select based on the chosen language/region.
Regards, Peter
Hi Peter,
Thank you for your reply. I know it is supposed to be that way, but unfortunately it doesn’t seem to work.
The language/region in the deployment profile is set to Swedish, and Automatically set keyboard is set to yes, but after installing the device, it has a US keyboard layout on the logon screen.
I’ll guess I will need to open a support case with Microsoft.
Please let me (and other readers) know the response of the support case.
Regards, Peter
Hi Peter,
Unfortunately Microsoft confirmed that it isn’t possible to automatically a different keyboard layout (input-locale) that is different from the OS language. So if you have an US English Windows OS, it is not possible to, automatically, set for example a Swedish keyboard.
I believe this is a serious issue since the above scenario shouldn’t be unusual, especially in international organizations. The support engineer I talked to agreed on this point.
I filed a feature request to the Feedback hub (previously Uservoice): https://feedbackportal.microsoft.com/feedback/idea/ccaa6471-cb79-ec11-a81b-6045bd7bf64c
Feel free to upvote the request if you agree that this should be added.
//Jasper
Thank you for providing that information Jasper!