This week another blog post about Windows 10. This time in combination with mobile app management without enrollment (MAM-WE). Due to the size of the blog post, I’ve decided to divide this post in 2 parts. This weeks post will provide a short introduction, followed by the required configurations. Next weeks blog post will be about the end-user experience.
Introduction
MAM-WE, for Windows 10, relies on Windows Information Protection (WIP) in combination with a new enrollment flow in Windows 10, version 1703. That new enrollment flow enables users to enroll their personal device for receiving only MAM policies. Those MAM policies are only applicable to activities performed by the work account and do not apply to the personal account. The part that makes it a bit funny is that it’s named MAM-WE and it’s still required to do an enrollment. However, that enrollment is only for MAM. It’s correct that it’s without MDM enrollment. In other words, no policies are applied to the personal device of the user. This is a very powerful combination with conditional access.
Configuration
Now let’s have a look at the configuration of the MAM-WE enrollment, the configuration options of the MAM-WE app policy and the assignment of the MAM-WE app policy. I’ll show the locations of the configuration options and the available configuration options. In addition I’ll provide additional information about settings, to clarify the available configuration options.
Enable MAM-WE enrollment
Let’s start with the first step, which is enabling MAM-WE enrollment. The following steps will go through the steps to enable MAM-WE enrollment in the Azure portal.
Create MAM-WE app policy
Let’s continue with the second step, which is creating the MAM-WE policy. The following steps will go through the steps to create the MAM-WE app policy in the Azure portal. The first 4 steps are required actions, the last 4 steps are mainly used for providing information about the available settings.
| 1 | Open the Azure portal and navigate to Intune mobile application management; |
| 2 | Select App policy to open the App policy blade; |
| 3 | On the App policy blade, click Add a policy to open the Add a policy blade; |
| 4 |
Now let’s go through the remaining configurations. Allowed apps in step 5, Exempt apps in step 6, Required settings in step 7 and Advanced settings in step 8. After going through these steps simply click Create to create MAM-WE policy; |
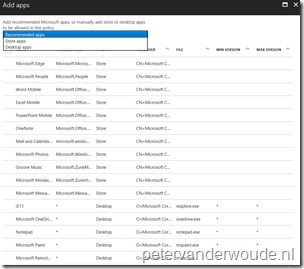
| 5 |
Note: Make sure that every configured app is enlightened for WIP. Without that confirmation the app can behave different than expected. For a lot more information see this article. |
| 6 | 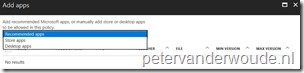 On the Exempted apps blade, click Add apps to open the Add apps blade. On the Add apps blade, the configuration options are the same as with the Allowed apps. The only difference is that there are no Recommended apps preconfigured; On the Exempted apps blade, click Add apps to open the Add apps blade. On the Add apps blade, the configuration options are the same as with the Allowed apps. The only difference is that there are no Recommended apps preconfigured; |
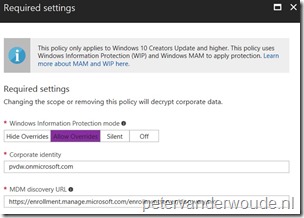
| 7 |
Note: Make sure to start with Silent or Allow overrides for a pilot group. This enables the administrator to add the used apps to the allowed apps list. |
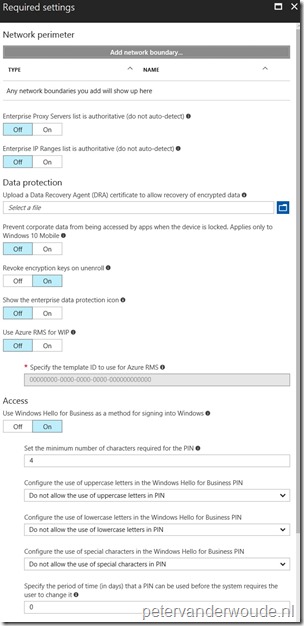
| 8 |
Note: Make sure to be aware of the remaining available settings related to subjects like RMS and Windows Hello for Business, before finalizing the configuration. |
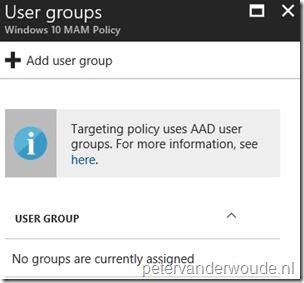
Assign the MAM-WE app policy
The third and last step is assigning the MAM-WE app policy. The following steps will go through the steps to assign the MAM-WE pp policy to an Azure AD user group in the Azure portal.
More information
For more information about app policies and WIP, please refer to:
- General guidance and best practices for Windows Information Protection (WIP): https://docs.microsoft.com/en-us/windows/threat-protection/windows-information-protection/guidance-and-best-practices-wip
- Get ready to configure app protection policies for Windows 10: https://docs.microsoft.com/en-us/intune/app-protection-policies-configure-windows-10
- Create and deploy Windows Information Protection (WIP) app protection policy with Intune: https://docs.microsoft.com/en-us/intune/windows-information-protection-policy-create
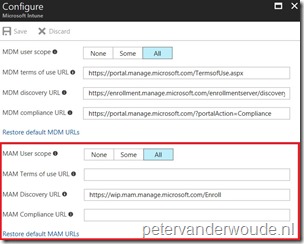
After configuring a MAM-WE policy using the recommended network boundaries from https://docs.microsoft.com/en-us/windows/threat-protection/windows-information-protection/recommended-network-definitions-for-wip, and the recommended apps for the Allowed Apps list, I’m getting some odd behaviour.
In Chrome and Firefox, I am suddenly blocked from visiting a lot of websites (non-microsoft domains). They work fine in Edge and IE, however. Am I missing something in regards to the network boundaries and the use of non-enlightened apps?
To my knowledge that configuration should only affect managed apps and the specified network boundaries. I can’t align that with the behavior you’re specifying.
You might need to specify /*AppCompat*/ string to avoid blocking Chrome and Firefox for SSL sites. Please see https://docs.microsoft.com/en-us/windows/threat-protection/windows-information-protection/app-behavior-with-wip
That is correct. Thank you for explicitly mentioning the information and the link to the docs.
Hi Peter,
“Also, when using that as a starting point, make sure to also configure conditional access for those resources”.
Can you point me in the right direction for such a CA policy?
From the Intune App Protection, you can choose CA Exchange or SharePoint Online (so limited to just those apps) and these are for iOS and Android only.
When setting up a CA policy from Azure AD/ Intune there must be some control to block all devices and grant access to a MAM Win10 device. But how do I do that?
Thanks
Hi Peter,
No, there is no specific MAM configuration in Device CA. Those technologies should simply be used together to create a “complete” solution.
Regards,
Peter
Hi Peter,
Oh dear me again 🙂
Is there a way (that i dont know of) to enroll a Windows 10 device in Intune/MDM and also use MAM (for Windows 10 it’s called WIP btw.) ?’
We want to check compliance of a device but also able to remove company data of the device.
The button remove company data in Intune only removes Intune managed company data and onedrive/outlook are not Intune managed.
Idea was to use MAM for this but you cannot use MAM (WIP) and MDM together on a Windows 10 device, or is there a workaround ?
Regards,
Hi RKast,
Not sure if I completely understand the question, but you can create an app management policy for enrolled Windows 10 devices.
Regards, Peter
Hi Peter,
Correct we can create a MAM policy with enrollment for Windows 10 but unfortunately a Selective Wipe is not supported/working on Windows 10 (only iOS and Android). Using Remove Company Data from Intune portal only removes Intune managed apps so not Outlook, OneDrive etc. You any bright idea’s how to remove company data from those applications without factor reset the device 🙂 ?
The problem with MDM scope and MAM scope both seth to All Users is that a Windows 10 device gets ‘enrolled’ for MAM/WIP , so it will not be enrolled in Intune. Also tried to enroll via Company Portal after this but then you get message the device is already in organization administration. So how can we use MAM and MDM for one user that is scoped for MAM and MDM?
Hi Rkast,
The most logical thing to say would be company-owned versus personal-owned.
Regards, Peter
Hi Peter,
MAM and MDM scope is set on User level. So hoe can we actieve this with personal vs Company?
And maybe got an idea how we can remove Company data from full outlook and OneDrive cliënt?
Thanks!
Hi RKast,
Think about the whole chain. Company devices are AutoPilot and/or Azure AD joined, anything else will be personal.
Regards, Peter
Hi Peter,
Any experience with organizations that hire contractors bringing their Windows 10 device which is already enrolled in their company? Since WIP doesn’t support multi identity (yet) both MDM enrollment and MAM-WE isn’t an option on these devices.
Hi Tom,
That depends on the functionality that you would like to provide.
Regards, Peter
requirement is to allow access to some lob (cloud) applications incl sharepoint online and exchange online making sure we protect the company data against leakage.
Hi Tom,
When it’s really about preventing data leakage, you don’t have any other options than waiting for WIP to support multi-identity…
Regards, Peter
Hi Peter,
Great work as always!
I have 2 questions.
1) Can Windows MAM-WE CA work nicely with MAM-WE CA for Android and IOS?
2) I see there is a huge bug that anytime a user can change the file ownership from Corp to Personal and then the data can be leaked. Ever had this?
Hi Aron,
The challenge with MAM-WE for Windows 10 is that it can’t really be enforced by using CA. Also, it relies on WIP and I wouldn’t want to call WIP a security feature. More a convenience and awareness feature. It indeed also provides your users with adjusting the file ownership of files.
Regards, Peter