This blog post uses the BitLocker configuration service provider (CSP) to manage drive encryption on Windows 10 devices. This CSP was added in Windows 10, version 1703, which is currently available as Insider Preview build.
This blog post will be about requiring BitLocker drive encryption on Windows 10 devices. Until Windows 10, version 1703, this was not possible. It was only possible to create a compliance policy that would block access to Windows 10 devices without BitLocker enabled. Windows 10, version 1703, introduces the BitLocker CSP, which enables the administrator to manage BitLocker settings via Windows 10 MDM. In this post I’ll briefly go through the available settings in the BitLocker CSP and I’ll show how to require BitLocker drive encryption via Microsoft Intune hybrid and Microsoft Intune standalone. I’ll end this post by showing the end-user experience.
Configuration
I’ll split the configuration in two sections. The first section about the available settings in the BitLocker CSP and the second section about how to configure the BitLocker drive encryption requirement. As the BitLocker CSP is new in Windows 10, version 1703, I thought it would be good to briefly go through the available settings.
Available settings
Let’s start by going through the available settings in the BitLocker CSP. The root node for the BitLocker CSP is ./Device/Vendor/MSFT/BitLocker and it contains the following settings.
| Setting | Description |
| RequireStorageCardEncryption | This setting allows the administrator to require storage card encryption on the device. |
| RequireDeviceEncryption | This setting allows the administrator to require encryption to be turned on by using BitLocker. |
| EncryptionMethodByDriveType | This setting allows the administrator to configure the algorithm and cipher strength used by BitLocker. |
| SystemDrivesRequireStartupAuthentication | This setting allows the administrator to configure whether additional authentication is required each time the computer starts. |
| SystemDrivesMinimumPINLength | This setting allows the administrator to configure a minimum length for a TPM startup PIN. |
| SystemDrivesRecoveryMessage | This setting allows the administrator to configure the recovery message or replace the existing URL. |
| SystemDrivesRecoveryOptions | This setting allows the administrator to control how operating system drives are recovered. |
| FixedDrivesRecoveryOptions | This setting allows the administrator to control how fixed data drives are recovered. |
| FixedDrivesRequireEncryption | This setting allows the administrator to require BitLocker for fixed data drives to be writable on a computer. |
| RemovableDrivesRequireEncryption | This setting allows the administrator to require BitLocker for a removable drive to be able to write data. |
Configure settings
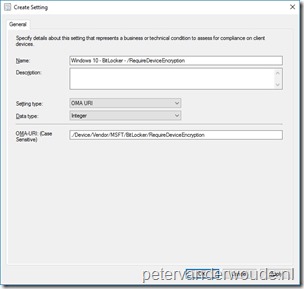
Now that I’ve been through all the available settings in the BitLocker CSP, let’s have closer look at the setting that enables the administrator to require BitLocker drive encryption. That’s the setting RequireDeviceEncryption. However, keep in mind that this still does require an interaction with the end-user. The end-user has to provide information about the currently used drive encryption and the end-user has to start the BitLocker drive encryption process. More about that in the end-user experience section. To require BitLocker drive encryption the following OMA-URI configuration can be used:
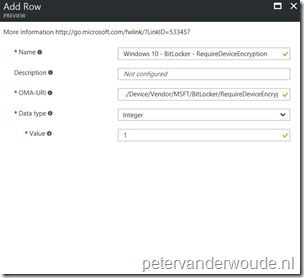
- OMA-URI: ./Device/Vendor/MSFT/BitLocker/RequireDeviceEncryption
- Date type: Integer
- Value: 1
This configuration information can be used in Microsoft Intune hybrid and Microsoft Intune standalone, by using the configuration guidelines shown below.
End-user experience
Let’s end this post with the end-user experience. As I mentioned earlier, the end-user must still interact with the messages generated by the configuration to require BitLocker drive encryption. Once the configuration arrives at the Windows 10 device, the end-user will receive a toast message stating that “Encryption is needed”, as shown below on the left. After selecting that notification, the end-user will receive a dialog box with the question “Are you ready to start encryption”, as shown below on the right.
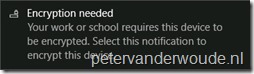 |
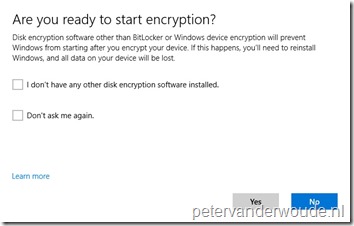 |
After checking the applicable boxes and clicking Yes, the end-user will get the standard BitLocker Drive Encryption wizard. During that wizard the end-user must specify the location to back up the recovery key, choose the encryption method and the end-user can start the encryption.
More information
For more information about the BitLocker CSP, please refer to this article about the BitLocker CSP.
Hi Peter
Does this only apply to InstantGo devices? I tried deploying to a ThinkPad T460 but received this error: “0x87D10196 : Syncml(406): The requested command failed because an optional feature in the request was not supported.”
Documentation doesn’t exactly specify which device types are supported, unless I’m over-reading. Thanks!
Hi Phil,
I actually don’t know. Like you mentioned, the docs don’t mention anything specific about InstantGo capable devices. That being said, to my knowledge an InstandGo capable device should automatically encrypt during Azure AD join.
Regards,
Peter
Does it also work if the logged on user is not a local administrator?
Don’t know. However, at this moment the user needs to be local administrator to enroll the device anyway. So not sure how it would matter at this moment.
@Phil: This should work for all devices not just instant go that have Bitlocker. Bitlocker is not available on home edition and not available by default on server editions. Was your device one of these?
@Rene: right now, yes you need to be a local admin for encryption to start and recovery key to be escrowed
Hi
Any options to control where user saves recovery key, force them to use AAD?
According to the docs you can only force the use of AD DS. I haven’t explicitly tested those options in combination with AAD.
Old post I know, but can anyone shed any light on the function of the ‘Don’t ask me again’ tick box? Does this allow the user to select No to encryption, and ‘don’t ask me again’ to stop the notification ever coming up again. Seems to defeat the object of an admin controlled configuration setting if that’s the case. Thanks.
PS: Great blog by the way!
Hi Alex,
Starting with Windows 10, version 1803, you can use AllowWarningForOtherDiskEncryption of the BitLocker CSP and starting with Windows 10, version 1809, you can use AllowStandardUserEncryption.
For more information see: https://docs.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp
Regards, Peter
Great post! Thank you as always Peter!
Peter,
Great read — thanks! Wondering if you may be able to shed some more light… Have an Intune endpoint protection policy that’s erroring out on the following BitLocker settings:
BitLockerFixedDrivesRequireEncryption
BitLockerSystemDrivesRecoveryOptions
Warning for other disk encryption
BitLockerRemovableDrivesRequireEncryption
Same error details for all 4 — “Syncml(406): The requested command failed because an optional feature in the request was not supported.”
Target device is a Surface Pro running Win 10 Pro. Any idea what “optional feature” isn’t present? I even tried modifying the policy settings where they would appear to affect those 4 settings but nothing seemed to make much difference.
Thanks!
Hi Steve,
Which version of Windows 10 are you using? The BitLocker CSP is supported on Windows 10 Pro starting with 1809.
Regards, Peter
@Steve – good to know you’re having the same issues as me. Surface Pro LTE’s running Win10 Pro 1803 & 1809. Most of the fleet are showing errors with
BitLockerSystemDrivesRequireStartupAuthentication
BitLockerSystemDrivesRecoveryMessage
BitLockerFixedDrivesRecoveryOptions
BitLockerSystemDrivesRecoveryOptions
With the error being: Syncml(406): The requested command failed because an optional feature in the request was not supported.
Sorry for the late reply… We’re running Win10 Pro 1803 (10.0.17134.523). Still have the same errors as recently as my Intune checking this afternoon. It would just be nice to be able to know that errors on our Intune dashboard were legitimate errors. Maybe a warning if I’m pushing a policy that a target device doesn’t support. Then again maybe I’m just being high maintenance…
Steve
Hi Steve,
The BitLocker CSP is supported on Windows 10, starting with version 1809…
Regards, Peter
Yep read that, just waiting for the update to grace me with its presence.