This week back in conditional access. More specifically, the recently introduced requirement, in the grant control, to Require approved client apps, which is currently still in preview. That requirement feels a bit like MAM CA, but more about that later in this post. In this post, I’ll provide more information about the Require approved client apps requirements and I’ll show how to configure that requirement. I’ll end this post with the end-user experience.
Introduction
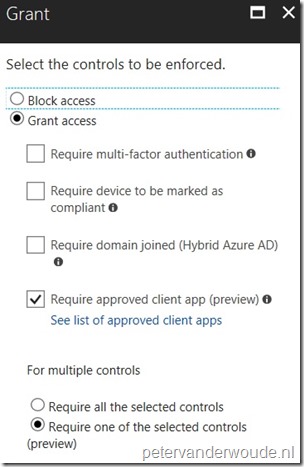
When configuring a conditional access policy, it’s now possible to configure the requirement to grant access only if a connection attempt was made by an approved client app. That’s done by using the Require approved client apps requirement. This requirement could be described as something similar as MAM CA, but with less options and straight from Azure AD. The main difference, from a configuration perspective, is that MAM CA provides more granular control over the client apps that can be used to access a specific cloud app, while this requirement in conditional access is simply on or off. On the other hand, this requirement in conditional access can be used with every cloud app, while MAM CA is only available for Exchange Online and SharePoint Online.
The approved client apps for the Require approved client apps requirement are the following apps (that all support Intune MAM):
- Microsoft Excel
- Microsoft OneDrive
- Microsoft Outlook
- Microsoft OneNote
- Microsoft PowerPoint
- Microsoft SharePoint
- Microsoft Skype for Business
- Microsoft Teams
- Microsoft Visio
- Microsoft Word
Keep in mind that the Require approved client apps requirement:
- only supports iOS and Android as selected device platforms condition;
- does not support Browser as selected client app condition;
- supersedes the Mobile apps and desktop clients client app condition.
Configuration
Now let’s have a look at the required configuration of a conditional access policy in the Azure portal. To be able to use the Require approved client apps requirement, create a conditional access policy as shown below. The following 7 steps walk through the minimal configuration for, for example, Exchange Online.
| 1 | Open the Azure portal and navigate to Azure Active Directory > Conditional access > Policies; |
| 2 | On the Policies blade, click New policy to open the New blade; |
| 3 | 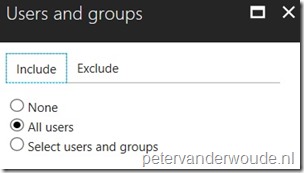 On the New blade, select the Users and groups assignment to open the Users and groups blade. On the Users and groups blade, select All users and click Done; On the New blade, select the Users and groups assignment to open the Users and groups blade. On the Users and groups blade, select All users and click Done; |
| 4 |  On the New blade, select the Cloud apps assignment to open the Cloud apps blade. On the Cloud apps blade, select Select apps to select Office 365 Exchange Online and click Done; On the New blade, select the Cloud apps assignment to open the Cloud apps blade. On the Cloud apps blade, select Select apps to select Office 365 Exchange Online and click Done; |
| 5 |
Note: This configuration will make sure that only the mentioned approved client apps can access Exchange Online. |
End-user experience
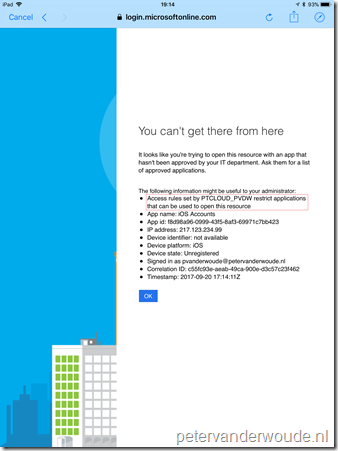
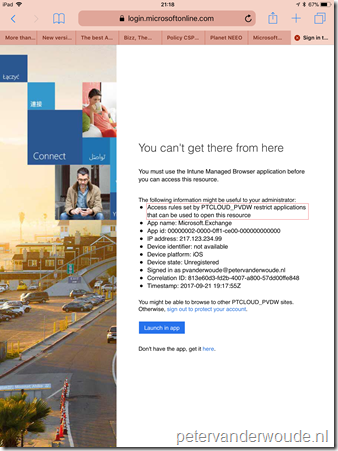
As usual with this type of posts, I’ll end this post with the end-user experience. On the left is an example of the iOS 11 default mail app that is trying to connect with Exchange Online. This provides a clear message that the app can’t be used, as it’s not approved. On the right is an example of the iOS default browser that is trying to connect with outlook.office365.com. This provides a less clear message and refers to the Intune Managed browser, which is currently not on the approved apps list. This is very likely the reason why the browser functionality is currently not yet supported, but it’s very good to see that the access is blocked. That removes a big potential backdoor of a great feature!
 |
 |
More information
For more information about conditional access and requiring approved client apps, please refer to this article about Azure Active Directory Conditional Access technical reference | Approved client app requirement.
Hi Peter, thanks for the write up, this is good stuff! Any news / plans for the Microsoft Managed Browser (IOS/Android) becoming one of the apps? This would be useful for Intranet / O365 resources to ensure MAM controls on those sites. Thanks John
Good question, John. I haven’t heard anything about that yet.
Regards,
Peter
Hi Peter,
I hope you’re well! I’m still loving the blog!
I wanted to ask for your help in understanding whether it is possible to add 3rd party apps to this Approved client app list?
Eg. we want to only allow access to O365 to the list of apps from Microsoft and additional ones we approve.
Hi Richard,
No, at this moment that list is the documented Microsoft apps only. It’s an often heard request though, so make sure to post it on UserVoice.
Regards, Peter
Hi Peter,
Thank for you the prompt reply – that is a great suggestion and I’ll be upvoting it on UserVoice.
Rich
Hi,
I have a customer who has ported to Microsoft and they are using Conditional Access Policy.
I’ve made an UWP application and two mobile (android and iOS) apps which are using an Enterprise Application I created in order to let users login with their Microsoft accounts to browser their calendar and onedrive items.
The customer is saying that because the Conditional Access Policy and my application not being listed as an approved client app, they cannot use it. So, they are requesting me to get the application added as an approved application to be able to use it.
I have tried to find information on what I should do in order to get the problem solved, but I’m a little bit lost and not sure what I should do.
I would appretiate it if you can point me in the right direction in order to sort this issue.
Hi Jose,
At this moment that’s the Require approved client app setting applies to a fixed list of apps. The eventual idea, to my knowledge, is that the Require app protection policy setting will replace that list and will support apps that include the Intune SDK. Until that time you might want to contact Microsoft, via a support case, to see what the possibilities are to get an app added to the first list.
Regards, Peter
Hi Peter,
Thanks for your answer. So at the moment, there is nothing we can do to help our customer using our application with the Conditional Access Policy set? Unless we get added to the approved clients app list, right?
Best regards, Jose.
Hi Jose,
Yes, without creating exceptions, I think that’s a correct conclusion.
Regards, Peter
Hi Peter,
I have a similar situation with an app that is not on the approved client app list but have a customer who wants to enable the Request approved client app conditional access policy. Is it still the case that the list of approved apps is fixed or is it possible to get an app added to the list?
Thanks,
James.
Hi James,
Yes, that’s still the case. When they’re creating their own app, they might want to look at Require app protection policy instead and include the Intune MAM SDK in their app.
Regards, Peter
Hi Peter
I found your blog during my search for opinions on the following.
We have an intranet where the mobile app uses Microsoft Graph backend during authentication.
we have a policy for mobile devices
using ‘require approved client app’ for ‘all users’ and ‘all cloud apps’
> in your example you only have this for the MS apps.
Because of ‘require approved apps’ MS Graph is being blocked as it is not an approved client app, but is a backend…
and because of that policy the authentication is not working.
I am now wondering
> by only choosing the MS applications in the require approved app policy + mfa
what would be the security risk ?
A second policy would be ‘all cloud apps > MFA ‘
and a 3th policy would be ‘selected apps > require intune app protection policy
> in the 3th the intranet app would be added as do some others.
I’m a bit stuck here I would absolutely appreciate your advice
we have a company w/ 16k users
IT security very easily says no to everything so If I would go to them saying the below I would need to backup my claims.
But I’m not sure myself and feel a bit lost..
‘i want to change the CA and stop using ‘all app’ + ‘require approved client app’
anyinput would be appreciated ‘even a sorry I can’t help’ 🙂
thank you
Hi Quiten,
This blog was only providing a simple example of how it works. For creating conditional access policies, I also usually start with targeting everything, to make sure that everything is assigned and protected. Especially something like Graph should be protected well. For the app, did you look at using the app protection policy alternative by implementing the Intune SDK?
Regards, Peter