This time I want to address a specific scenario around role based administration. This scenario will be focused on providing different levels of access, for a user, on different applications. I’ve seen this question on different forums over the last year(s) and also had this same question with a customer recently.
Scenario
This scenario is about a enterprise customer that uses ConfigMgr for managing their laptops. Nothing special, so far, not even the fact that they have around 100k laptops spread over the globe. What makes this customer special is the fact that they have a global IT department and a local IT department per country. The global IT department is responsible for making the generic applications available and the local IT department is responsible for making country specific applications available. Because of this, their requirement, for the local IT department(s), is to have read access to all global applications and full access to their own applications.
Solution
Actually the solution to this was a lot simpler then I initially thought. The only thing I could think about was that a user, or group, can only be configured once as a ConfigMgr user. Of course it’s very simple to work around this, by using security group(s), like every one should be in the first place. To solve this scenario, for one local IT department, we need the following:
- Two AD security groups.
- Both security groups contain the local IT department administrators;
- Two Security Scopes;
- One security scope will contain the global IT department applications;
- One security scope will contain the local IT department applications;
- Two Security Roles;
- One security role will contain full access to applications (in this case the built-in role Application Administrator is sufficient).
- One security role will contain read-only access to applications (in this case the built-in role Read-only Analyst is sufficient).
Now put this all together in Administration workspace, via Add User or Group on the Home tab in the Administrative Users node. Via the dialog box combine the AD security groups with the Security Roles and Security Scopes. For this last one make sure to select Only the instances of objects that are assigned to the specified security scopes or collections and select only the specific Security Scope. This should result in something like this: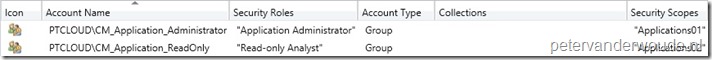
Result
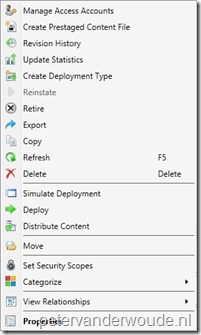
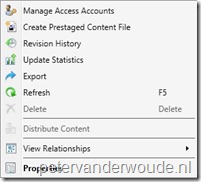
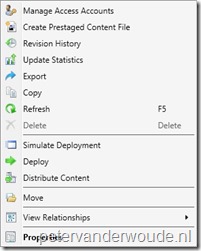
After these configurations it’s time to look at the results of the configurations. I do have to say that I was quite surprised by a part of the result and also can’t explain it, yet. To provide a good overview of the results, I putted three default right-click menu’s, for applications, next to each other. On the left is the right-click menu of a user with only Application Administrator rights on applications. In the middle is the right-click menu of a user with only Read-only Analyst rights on applications. Last, but not least, on the right is the right-click menu of a user with Read-only Analyst rights on the specific application and Application Administrator rights on other applications. Besides the normal read-only access, the user suddenly also has the rights to move, deploy and distribute the application. I can’t explain this behavior, yet.
| Application administrator | Read-only analyst | Read-only analyst (with Application administrator on other applications) |
 |
 |
 |