Getting started with the Windows Update for Business deployment service
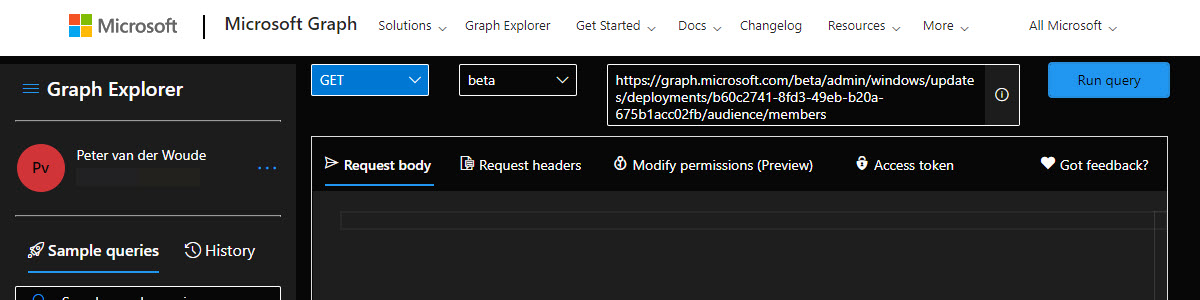
This week is about the Windows Update for Business deployment service. That subject has been touched recently when discussing the different options for upgrading devices to Windows 11, but that subject never got the attention that it deserves. The deployment service provides control over the approval, scheduling, and safeguarding of updates delivered from Windows Update. And the often still unknown part is that it’s actually actively used already within Microsoft Intune. The Feature updates for Windows 10 and later profile and the Quality updates for Windows 10 and later profile, both rely on that deployment service. This post will start with a quick introduction of the Windows Update for Business deployment service, followed with the basics of the deployment service APIs. Introduction to the Windows …