Getting started with Device Control Printer Protection
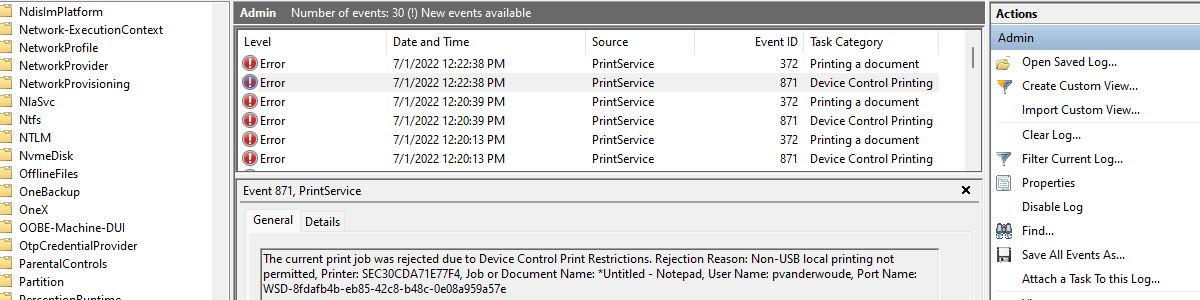
This week is a follow-up on an earlier post about controlling devices connected to Windows devices. That post was focussed on device control as a feature of Microsoft Defender for Endpoint, in general. This post will specifically focus on Device Control Printer Protection. Device Control Printer Protection is the printer protection feature that can be used to prevent users from printing via non-corporate network printers or non-approved USB-printers. That adds an additional layer of data protection and security. This post will look in more detail at the printer protection configuration options, at applying printer protection and at the experience with printer protection enabled (the user experience and the administrator experience). Note: The configuration options (protect) are available within a Microsoft 365 E3 license and the …