Further integrating Apple Business Manager with Microsoft Intune
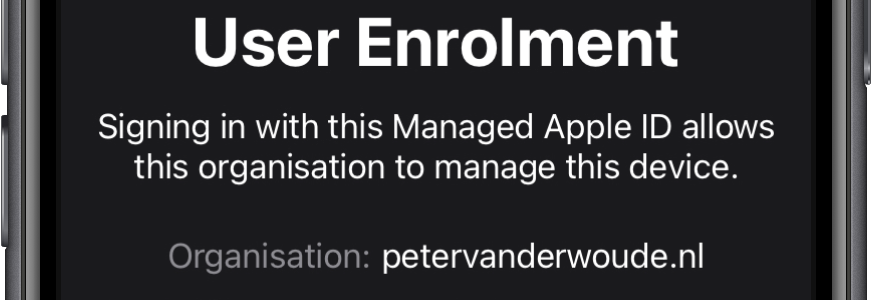
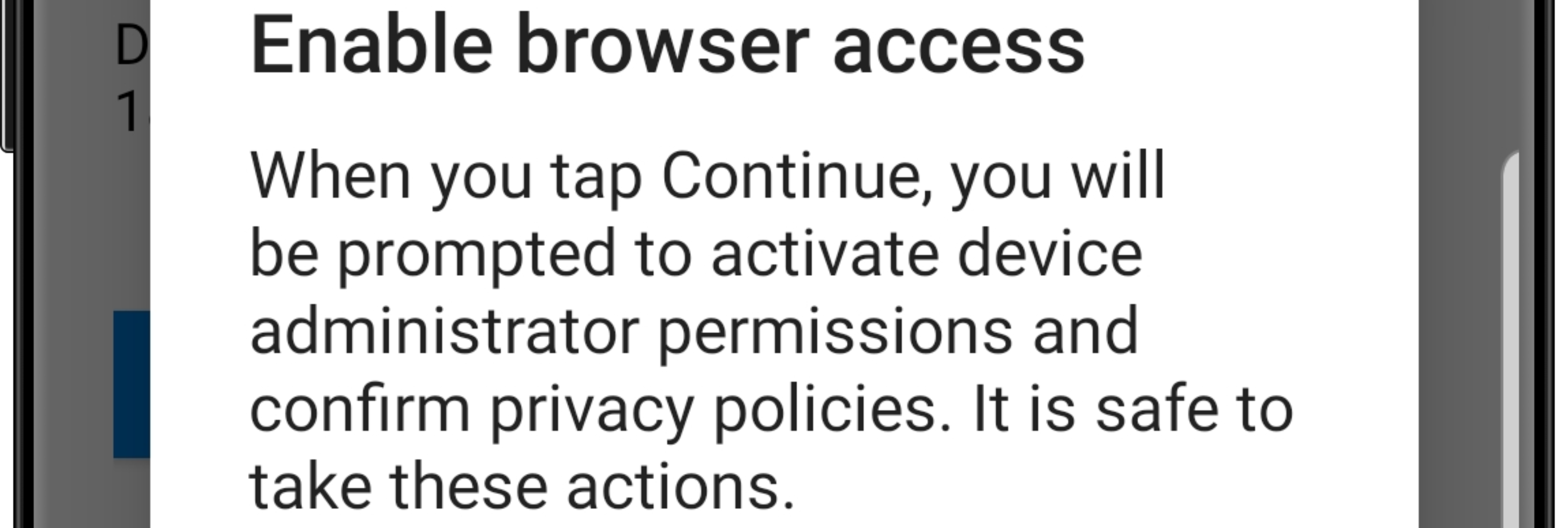
A few weeks ago I’ve discussed the integration of Apple Business Manager (ABM) with Azure AD, to provision the Managed Apple IDs and to provide a federation. That provides a very nice user experience, when used in combination with Microsoft Intune. This week I want to extend on ABM by further integrating it with Microsoft Intune. As a bare minimum for managing Apple devices it’s always required to use the Apple MDM Push certificate. I hope that every IT administrator can dream the required steps for such a certificate by now. On top of that, ABM can be used to facilitate company-owned devices and to facilitate volume purchased apps. That provides an even better experience on company-owned Apple devices. A great out-of-the-box experience together with …