This week is all about the simplification in targetting groups of apps with app protection policies and a followup on my tweet of last week. That tweet provided a quick peak at the new targetting options of app protection policies for Android and iOS/iPadOS devices. The great thing about that simplification is that app protection policies can now be targeted at different categories (or groups) of apps. Those categories of apps are All apps, All Microsoft apps and Core Microsoft apps, and are dynamically updated to include the appropriate apps. That dynamic update will make sure that the already created app protection policies are automatically updated with the latest apps that are available for the different categories and will also make sure that newly created app protection policies are autmoatically targeted to the latest apps that are available for the different categories. The table below provides a quick overview of the different categories (also known as groups), including a short description and the JSON-property.
| Group | Group description | Group property |
|---|---|---|
| All apps | This group includes all Microsoft apps and all third-party apps that have integrated the Intune SDK. | appGroupType: "allApps" |
| All Microsoft apps | This group includes all Microsoft apps that have integrated the Intune SDK. | appGroupType: "allMicrosoftApps" |
| Core Microsoft apps | This group includes the following specific apps: Microsoft Edge, Microsoft Excel, Microsoft Office, Microsoft OneDrive, Microsoft OneNote, Microsoft Outlook, Microsoft PowerPoint, Microsoft SharePoint, Microsoft Teams, Microsoft To Do, and Microsoft Word. | appGroupType: "allCoreMicrosoftApps" |
Note: Use the Developer Tools in Microsoft Edge to verify the JSON-properties that are used for creating an app protection policy by using the Microsoft Graph API.
Manually creating app protection policies
When looking at the manual creation of app protection policies, the steps are fairly simply. During the creation of the app protection policy, the wizard provides the IT administrator to assign the policy to a category (or group) of apps. The following nine steps walk through the manual creation of an app protection policy, with the focus on the assigned apps (step 4).
- Open the Microsoft Endpoint Manager admin center portal navigate to Apps > App protection profiles
- On the Apps | App protection policies blade, click Add > iOS/iPadOS or Android
- On the Basics page, provide the basic policy information and click Next
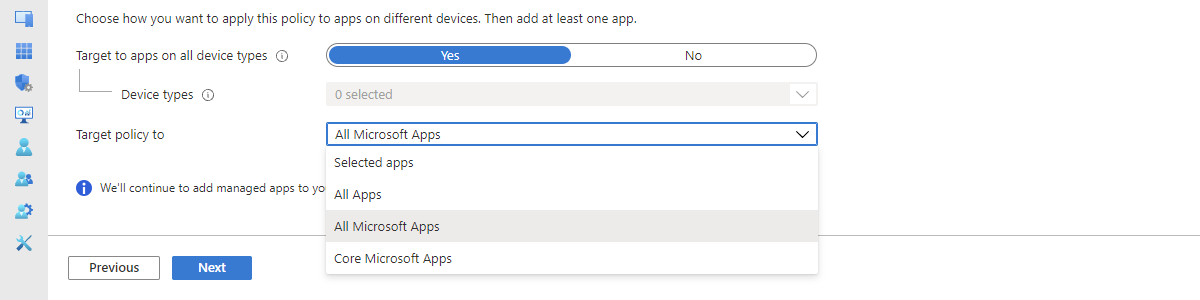
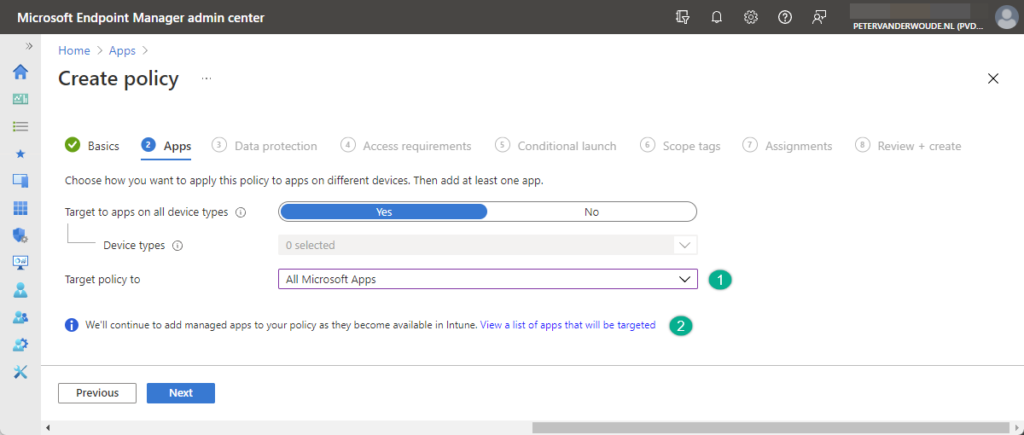
- On the Apps page, as shown in Figure 1, specify the required targetting of apps by at least configuring Target policy to to All apps, All Microsoft apps, or Core Microsoft apps and click Next
Note: When creating an app protection policy, use the link View a list of apps that will be targeted (as shown with number 2 in the figure above, to view the exact list of targeted apps.
- On the Data protection page, specify the required data protection settings and click Next
- On the Access requirements page, specify the required access requirements and click Next
- On the Conditional launch page, specify the required app conditions and device conditions and click Next
- On the Scope tags page, specify the required scope tags and click Next
- On the Assignments page, specify the required assignment and click Next
- On the Review + create page, click Create
Automatically creating app protection policies
When looking at the automatic creation of app protection policies, the change is only in the JSON-file when using a script as provided here. That change is as simple as reusing the existing JSON-file and making a small adjustment in the configured apps. That adjustment is adding the appGroupType property and either removing the apps property or adding a blank value to the apps property. Below is an example snippet of how that could work.
appGroupType: "allMicrosoftApps"
apps: []Note: Keep in mind that this is only a snippet of the added and changed properties.
More information
For more information about creating app protection policies refer to the following docs.