This week a follow-up on my post of last week. Last week was about onboarding Windows 10 devices for Windows Defender Advanced Threat Protection (ATP) and this week will be about offboarding Windows 10 devices of Windows Defender ATP. For devices that are leaving the company, for whatever reason, it’s good to first offboard those devices of Windows Defender ATP. That will remove the Windows Defender ATP settings from the device and the device will stop collecting and sending data. In this post I’ll show how to offboard Windows 10 devices, via Configuration Manager and Microsoft Intune, and I’ll show the end result. The steps in this post will be similar to the steps in the post of last week.
Configuration
Just like last week, there are multiple methods available to offboard Windows 10 devices of Windows Defender ATP. Those methods are Group Policy, Configuration Manager, mobile device management (including Microsoft Intune) and a local script. I’ll have a closer look at the configurations for offboarding Windows 10 devices via Configuration Manager and Microsoft Intune.
Create offboarding configuration file
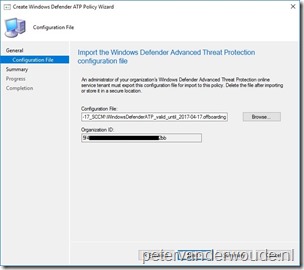
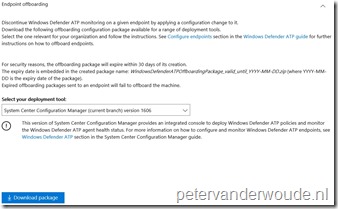
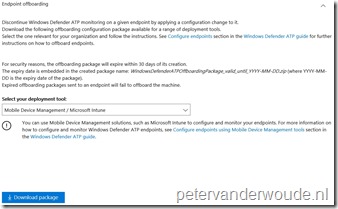
Before starting with the configuration, it’s required to create an offboarding configuration file. The process for this is fairly simple and straightforward. Logon to the Windows Defender Security Center and select Endpoint Management. Now select Endpoint offboarding, select the configuration method and download the required file, as shown below. After selecting download, an additional confirmation message will show, mentioning the expiration date of the offboarding package. For security reasons an offboarding package will always expire after 30 days.
| System Center Configuration Manager | Mobile Device Management |
 |
 |
Configure endpoints using Configuration Manager
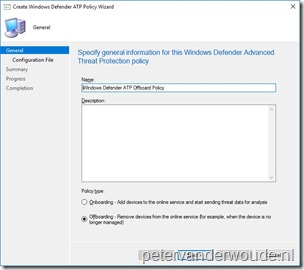
The first configuration method that I would like to show is using Configuration Manager, by creating and deploying a Windows Defender ATP Policy. This configuration method is only supported on Windows 10 devices, version 1607 and later, running the Configuration Manager client. On-premises mobile device management and Microsoft Intune hybrid MDM-managed computers are not supported. The following 6 steps show how to create the Windows Defender ATP Policy. After that, simply deploy the created policy.
Note: Make sure that a device is not targeted with an onboarding and offboarding configuration at the same time. This might cause unpredictable behavior.
Configure endpoints using Microsoft Intune
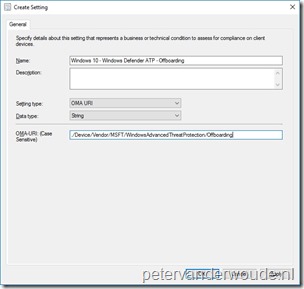
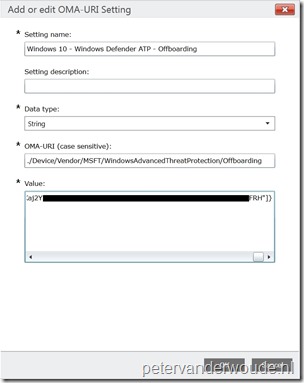
The second configuration method that I would like to show is using Microsoft Intune hybrid and Microsoft Intune standalone, Windows Defender ATP supports Microsoft Intune by providing OMA-URI settings to create policies to manage endpoints. To achieve this the following OMA-URI configuration can be used:
- OMA-URI: ./Device/Vendor/MSFT/WindowsAdvancedThreatProtection/Offboarding
- Date type: String
- Value: [Content of the WindowsDefenderATP.offboarding file that is available in the downloaded WindowsDefenderATPOffboardingPackage_valid_until_yyyy-mm-dd.zip file]
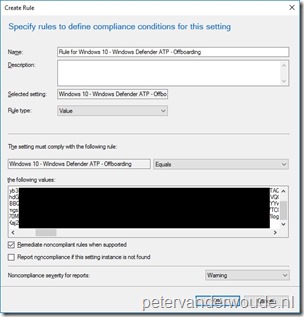
Just to make sure that it’s absolutely clear, the value, of the OMA-URI configuration, is literally a copy-paste action of the content available in the WindowsDefenderATP.offboarding file. This information can be used in Microsoft Intune hybrid and Microsoft Intune standalone, by using the configuration guidelines shown below.
Note: Make sure that a device is not targeted with an onboarding and offboarding configuration at the same time. This might cause unpredictable behavior.
End result
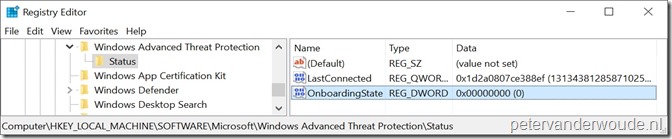
Let’s end this blog post by having a look at the end result. I’ll do that by showing that a successful offboarding can be verified in the registry of the Windows 10 device, as shown below. The OnboardingState should be set to 0.
More information
For more information about Windows Defender ATP and the offboarding, please refer to the following articles:
- Windows Defender Advanced Threat Protection: https://docs.microsoft.com/en-us/sccm/protect/deploy-use/windows-defender-advanced-threat-protection
- Configure endpoints using System Center Configuration Manager: https://technet.microsoft.com/itpro/windows/keep-secure/configure-endpoints-sccm-windows-defender-advanced-threat-protection
- Configure endpoints using Mobile Device Management tools: https://technet.microsoft.com/itpro/windows/keep-secure/configure-endpoints-mdm-windows-defender-advanced-threat-protection
- Troubleshoot Windows Defender Advanced Threat Protection onboarding issues: https://technet.microsoft.com/itpro/windows/keep-secure/troubleshoot-onboarding-windows-defender-advanced-threat-protection