This week is all about another nice feature that was recently introduced in Windows, Microsoft Intune, and Azure AD. That feature is Windows Local Administrator Password Solution (Windows LAPS). Windows LAPS is basically the evolution of the already existing LAPS solution for domain joined Windows devices. Big difference, however, is that Windows LAPS is now a built-in solution in Windows that can be configured via Microsoft Intune and that can use Azure AD as a storage location for the local administrator password. Windows LAPS can be used to manage the password of a single local administrator account on the device. The most obvious account for that would be the built-in local administrator account, as that account can’t be deleted and has full permissions on the device. So, securing that account is another important step in further securing the devices in the environment. This post will start with a quick introduction about Windows LAPS, followed with the steps to configure Windows LAPS and the options for retrieving, rotating and auditing the password of the local administrator account.
Note: This post will focus on Azure AD as the storage location for the local administrator account and password.
Introducing Windows Local Administrator Password Solution
Windows LAPS is the new built-in functionality in Windows that can be used for managing the password of a local administrator account on the device. The use of Windows LAPS helps organizations to further protect Windows devices from attacks that are aimed at exploiting local user accounts. Think about attacks like pass-the-hash or lateral-traversal. Besides that, Windows LAPS can also help with improving the security when providing remote support and with simply providing an alternative path for temporarily elevating permissions. Another common use case is providing an entrance to recover devices that became inaccessible for Azure AD accounts. And all of that by relying on native functionality that’s available on Windows devices with Windows 10 20H2 or later, and Windows 11 21H2 or later. That functionality can be enabled and configured by using Microsoft Intune and can use Azure AD as the storage location for the local administrator account and password.
When using Microsoft Intune for the configuration of Windows LAPS, the configuration relies on the new LAPS CSP on Windows devices. Via that CSP, Microsoft Intune provides support for the following capabilities of Windows LAPS:
- Configuring password requirements: Configuring password requirements for the local administrator account.
- Configuring password rotation: Configuring automatic password rotation on a schedule for the local administrator account and manually rotating the password for the local administrator account by using a device action.
- Configuring account and password backup – Configuring automatic account and password backup for the local administrator account in Azure AD, or Active Directory, by using strong encryption.
- Configuring post authenticating actions – Configuring the password expiration behavior (including how long the device waits) that a device takes when its local admin account password expires.
- Viewing account details – Viewing information about the local administrator account and its current password, and see when that password was last rotated and when it’s next scheduled to rotate.
- Viewing reports – Viewing reports on password rotation with details about manual and scheduled password rotation.
Note: The Windows LAPS functionality relies on the installation of the April 11, 2023 update.
Enabling Local Administrator Password Solution in Azure AD
The usage of Windows LAPS, with Azure AD as the storage location for the local administrator account and password, starts with a small configuration in Azure AD. That configuration is used to enable LAPS in the Azure AD tenant. The following two steps walk through the steps for enabling LAPS in that tenant.
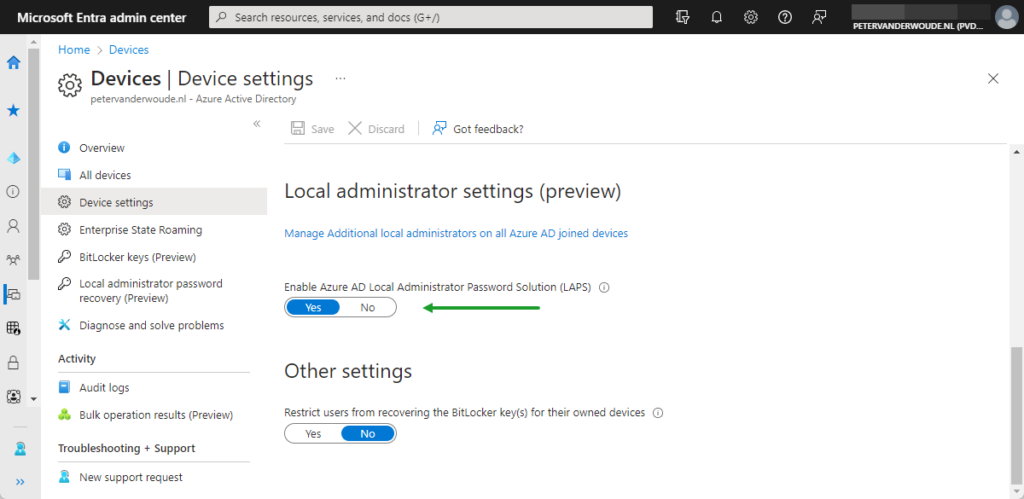
- Open Microsoft Entra admin center navigate to Azure Active Directory > Devices > Overview > Device settings
- On the Devices | Device settings page, as shown below in Figure 1, switch the slider with Enable Azure AD Local Administrator Password Solution (LAPS) to Yes and click Save
Configuring Local admin password solution profile
After enabling the LAPS functionality in Azure AD, the Windows devices must be configured to enable and configure Windows LAPS. That configuration can be achieved by using Microsoft Intune. More specifically, that configuration can be achieved by using an Account protection profile. When using Microsoft Intune for the configuration, it relies on the new LAPS CSP in Windows. That CSP can handle the required configuration options. The following eight steps walk through the configuration of an Account protection profile that enables and configures Windows LAPS by using Azure AD as the storage location.
- Open Microsoft Intune admin center and navigate to Endpoint security > Account protection
- On the Endpoint security | Account protection page, click Create Policy
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile: Select Local admin password solution (Windows LAPS) as value
- On the Basics page, specify a valid name to distinguish the policy from other similar policies and click Next
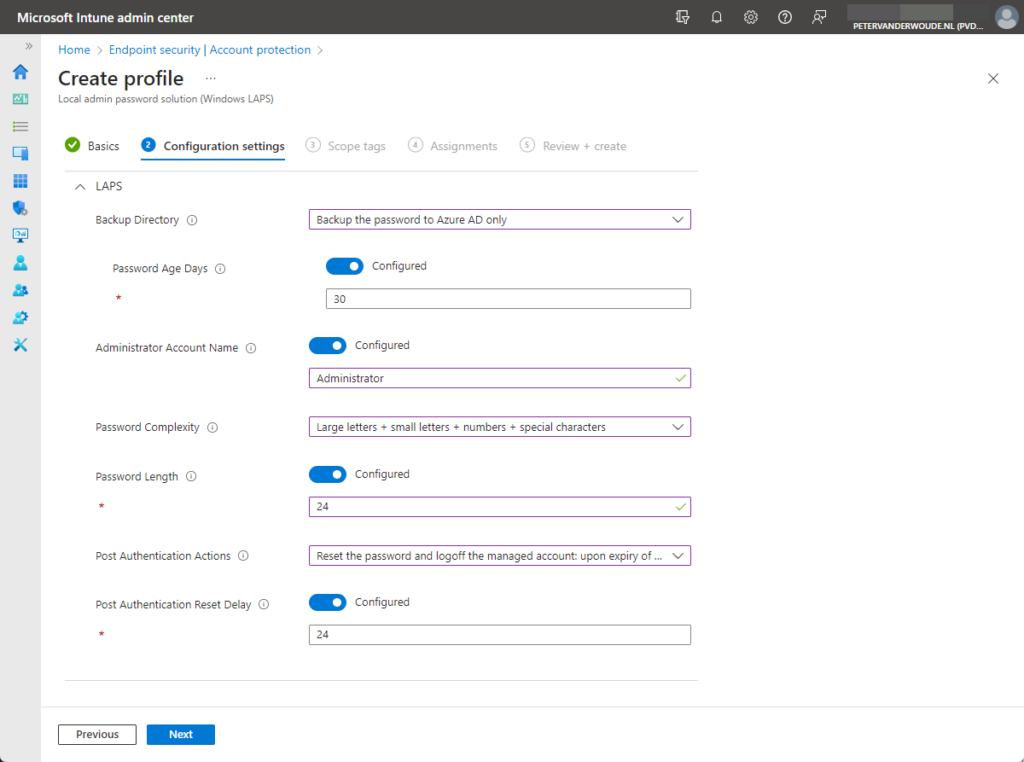
- On the Configuration settings page, as shown below in Figure 1, provide at least the following information and click Next
- Backup Directory: Select Backup the password to Azure AD only to make sure that it’s stored in Azure AD
- With Password Age Days switch the slider to Yes to enable password age and specify the age in days
- With Administrator Account Name switch the slider to Yes to enable the account name configuration and specify the account name of the managed local administrator account
- Password Complexity: Select Large letters + small letters + numbers + special characters, or one of the other less complex options, to add password complexity
- With Password Length switch the slider to Yes to enable password length and specify the password length
- Post Authentication Actions: Select Reset the password and logoff the managed account, or one of the other options, to configure the behavior upon expiration of the configured grace period
- With Post Authentication Reset Delay switch the slider to Yes to enable the password reset delay configuration and specify the reset delay in days
Note: Keep in mind that this will not enable the specified account, as that will require a separate configuration.
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the required assignment by selecting the applicable group and click Next
- On the Create + Review page, review the configuration and click Create
Note: The applied configuration is stored in the registry at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Policies\LAPS.
Verifying applied Local Administrator Password Solution configuration
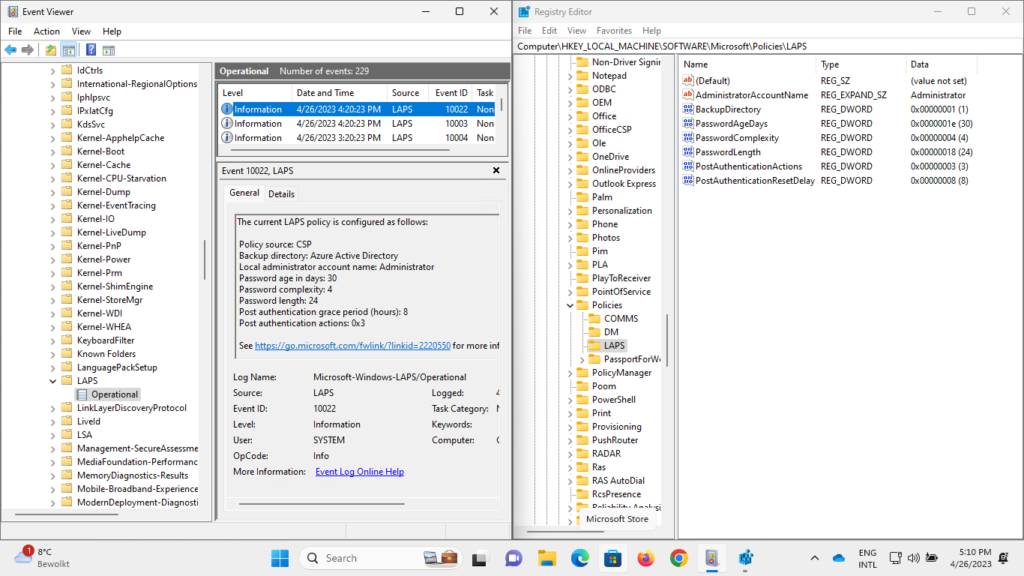
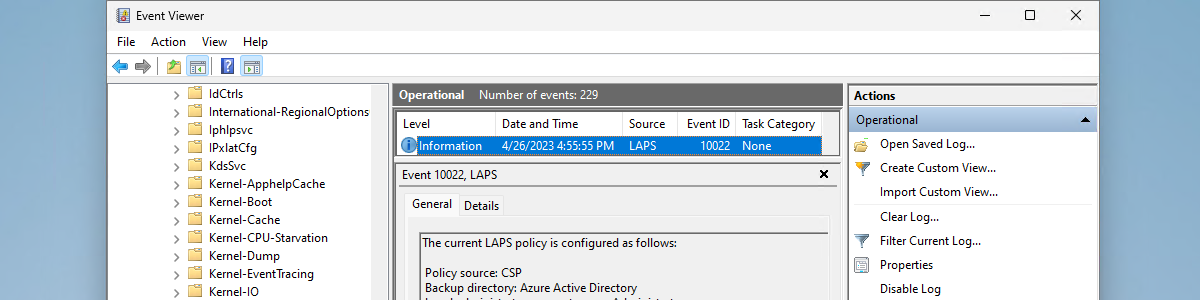
After using Microsoft Intune for applying the configuration to a Windows device, Windows LAPS will be enabled and configured. The status can be followed in Microsoft Intune, but it’s also good to know how to easily verify the configuration on the device itself. The configuration is stored in the registry at HKLM\SOFTWARE\Microsoft\Policies\LAPS, as shown below in Figure 3 on the right. That registry key contains values for the different configuration options of Windows LAPS. Besides that, there is a new Event Log named LAPS available on the device, as shown below in Figure 3 on the left. That log contains all the events related to Windows LAPS. From the applied configuration, till any performed actions (like rotating the password).
Retrieving the password of the managed local administrator account
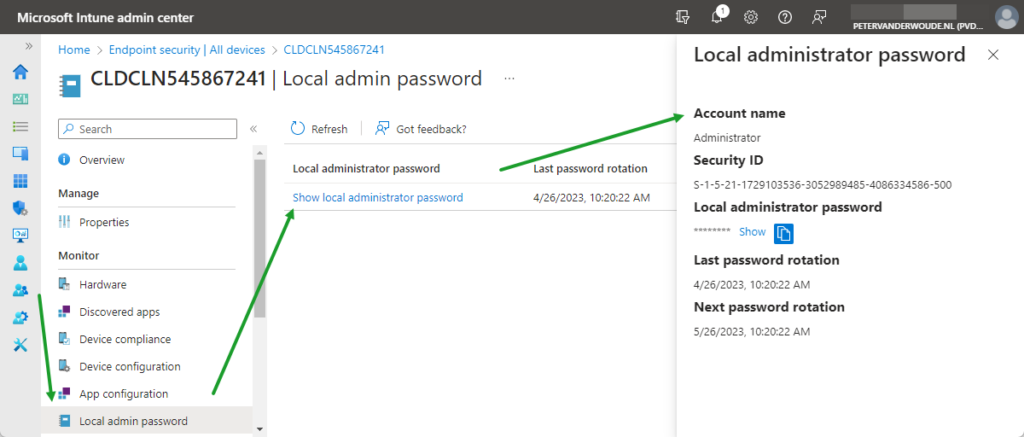
When Windows LAPS is enabled and configured for a device, the managed local administrator account and its password are stored in Azure AD and available via Microsoft Intune and Azure AD. That information is easily accessible for any IT administrator with the required permissions. Via Microsoft Intune, as shown below in Figure 4, the information is available via the Local admin password section of a device. After that, simply select Show local administrator password and click Show with Local administrator password, to retrieve the password of the managed local administrator account.
Note: During the public preview of Windows LAPS with Azure AD, the required permissions are available via the Global Administrator and the Cloud Device Administrator roles.
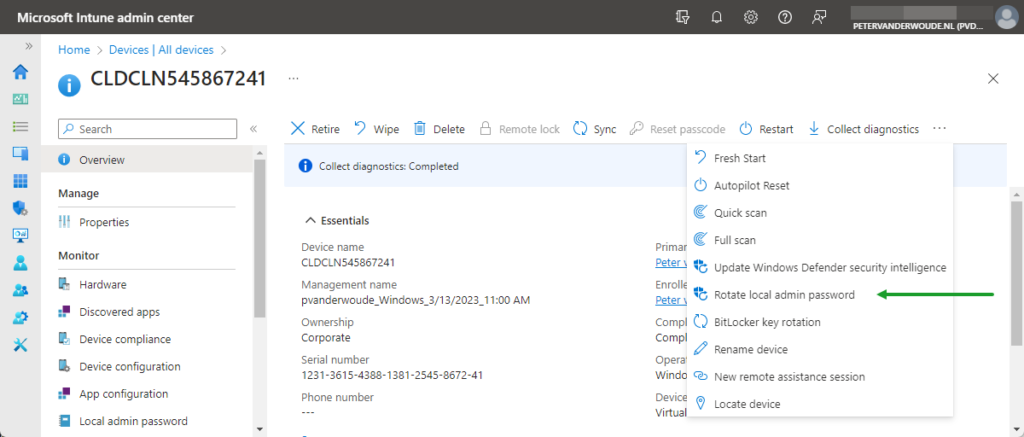
Rotating the password of the managed local administrator account
When using the password of the managed local administrator account, the configuration of Windows LAPS can make sure that the password will automatically rotate. Besides that, it’s also a relatively easy task for any IT administrator with the required permissions of: Read managed devices, Read organization, and Rotate Local Admin Password remote task. That task can be achieved in Microsoft Intune, as shown below in Figure 5, via the Overview section of a device. After that, simply select the three dots and click Rotate local admin password, to trigger the remote action to rotate the password of the selected device.
Auditing the managed local administrator account password activities
Besides all the configuration options and insights of Windows LAPS, there is also important audit information available. That provides any organization with the required information about the activities around the local administrator password on Windows devices. That information is easily accessible for any IT administrator, with the right permissions, and is available in the Audit logs in Azure AD, as shown below in Figure 6. The selected line is an example of a rotated password.

More information
For more information about Windows Local Administrator Password Solution, refer to the following docs.
Great run through , really helpful. One question
“Note: Keep in mind that this will not enable the specified account, as that will require a separate configuration”
What is the best way to enable the account?
Hi Neil,
That depends. Do you want to create an account or just enable the default account.
Regards, Peter
Create a new local account and give that account administrator permissions… I found a couple of helpful PS scripts via Intune to achieve this. So in conjunction with your helpful LAPS Intune walkthrough, I’m sorted!
Great to hear, Neil!
Hi Peter,
It looks like a great function, however I can’t get it to work.
I use the default account Administrator, and it does generate a password for the specified computer. However, when I try the combo of Administrator + the generated password, it still says it’s wrong.
In figure 2 you specified the account name. When I did this, the password was never generated. So I turned off that function, which makes it default to Administrator. Does that change anything?
I hope you have an idea, because i’ve been scratching my head at this for too many hours.
Regards,
Liam
Hi Liam,
The screenshot shows how I’ve done it for my default admin account. Have you looked at the Event Viewer for some more details?
Regards, Peter
Hi
I have set this up for a clients. It shows 28 devices have the LAPS policy and the policy is working fine. However in AAD under “local admin password recovery” only 6 devices are listed. It has been 3-4 weeks since I have enabled this. No errors, just not showing up.
Any ideas?
Hi Michael,
And do you have the information with the device object in Intune?
Regards, Peter
Hi. It has no errors in Intune, found errors in the PC ‘s event viewer.
I resolved this issue by changing the password complexity to at least 3 ways. I had it on Large letters + small letters .Changes it to Large letters + small letters + numbers.
It is stupid that they give you options though if it does not work.
Good to hear that you found it, Michael!
Regards, Peter