This week is all around the User Enrollment option that was introduced with iOS 13 and iPadOS 13.1 and that is currently available as preview functionality in Microsoft Intune. User Enrollment feels similar to what already can be achieved on Android devices with Work Profiles. A separation between personal data and company data. In this post I’ll start with a short introduction about User Enrollment, followed with the steps to created an enrollment profile that will facilitate the User Enrollment. I’ll end this post by show the end-user experience during the enrollment and after the enrollment.
Introduction to User Enrollment
User Enrollment is created and designed by Apple to facilitate an enrollment and management scenario for Bring Your Own Devices (BYOD). That enrollment and management scenario requires Managed Apple IDs. Those Managed Apple IDs are used to create an additional user identity on the device and can live perfectly alongside personal Apple IDs. Actually that’s the main idea. User Enrollment can be compared to the Work Profile for Android devices. It creates a clear separation between personal and company data. During the enrollment a separate volume is created on the device that contains managed versions of Apps, Notes, Calendar attachments, Mail attachments and Keychain.
User Enrollment also impacts the apps that can be deployed to users. The managed parts on the device are related to the Managed Apple ID and not to the personal Apple ID that is connected to the store. That means that an IT administrator must rely on Apple Volume Purchase Program (VPP) with user licenses for the distribution and licensing of store apps when working with User Enrollment. Besides that, by using Microsoft Intune it’s also possible to assign weblinks and line-of-business apps.
When looking from a management perspective, Microsoft Intune can be used to manage everything related to the Managed Apple ID and nothing related to the personal Apple ID. Also, after enrollment, an administrator can only use Microsoft Intune to retire the device and not to wipe the device. When looking from a enrollment perspective, Microsoft Intune contains a new enrollment type that can be used to facilitate User Enrollment. That profile provides the following options:
- User enrollment: This option will use User Enrollment for all the assigned users. That means that only work-related apps and data will be secured and that the device will be marked as personally-owned.
- Device enrollment: This option will use Device Enrollment for all the assigned users. That means that the whole device will be managed and that the device will be marked as company-owned.
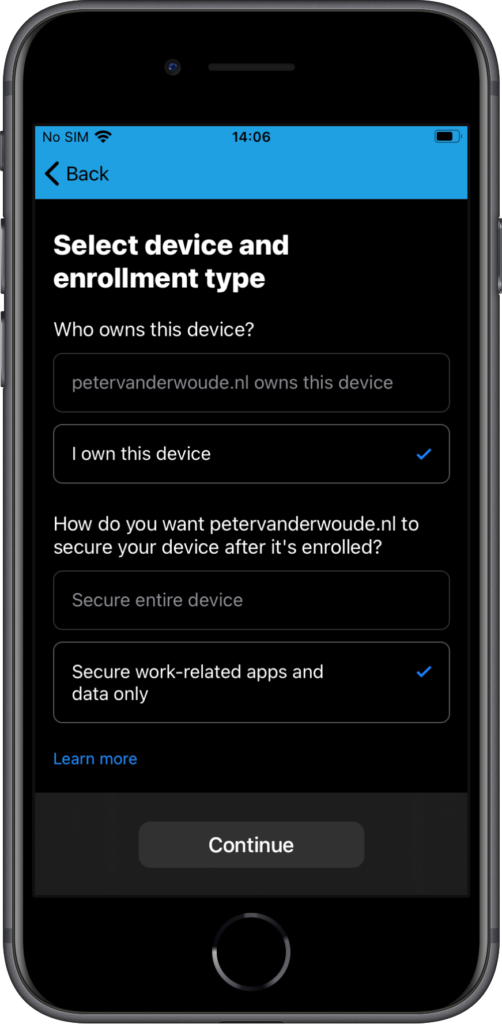
- Determine based on user choice: This option will provide the assigned users with a choice. Users must choose between I own this device and {company} owns this device. When they choose the latter option, the device will be enrolled using device enrollment and when they choose the first option they’re provided another choice. User must choose between Secure entire device and Secure work-related apps and data only. With both options, the device will still be marked as personal, but the level of management will differ. For an overview of these choices, see also Figure 3.
Create an enrollment type profile for iOS/iPadOS
The User Enrollment can be facilitated by using an enrollment type profile. That enrollment type profile contains the configuration of the enrollment type for the assigned users. The following six steps walk through the process of creating and assigning an enrollment type profile for iOS and iPadOS devices.
Important: Keep in mind that User Enrollment requires the use of Managed Apple IDs.
Note: The best user experience is provided by using provisioning and federated authentication for Managed Apple IDs, by using Azure AD. More information regarding that subject can be found in my previous post.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > iOS/iPadOS > iOS/iPadOS enrollment > Enrollment types to open the Enrollment type profiles blade
- On the Enrollment type profiles blade, click Create profile > iOS/iPadOS to open the Create enrollment type profile wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the enrollment type profile
- Description: (Optional) Provide a description for the enrollment type profile
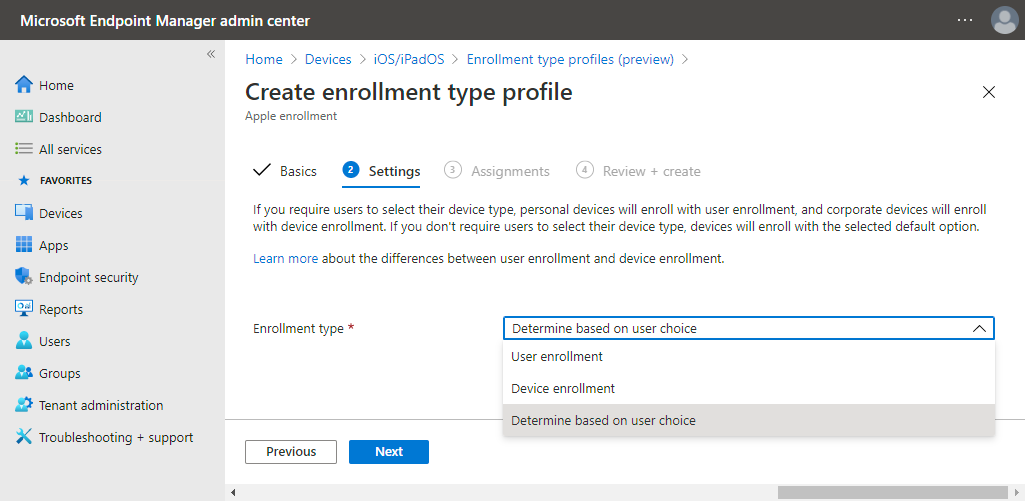
- On the Settings page, select one of the earlier explained enrollment types (for an overview see Figure 1 below) and click Next
Note: For showing the end-user experience options, I’m using Determine based on user choice.
- On the Assignments page, configure the assignment of the profile and click Next
Important: The assignment must be a user group, as this feature is based on user identities.
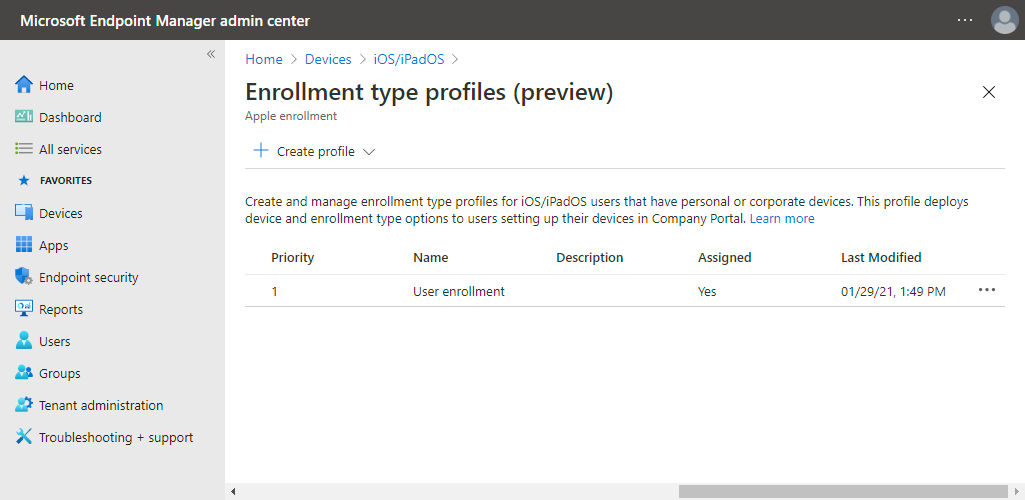
- On the Review + create page, verify the configuration and click Create (for the result see below Figure 2)
Note: Enrollment type profiles are created with a priority. The administrator can adjust the priority and the profile with the highest priority will be applicable to the enrollment.
End-user experience when enrolling a personal iOS device
The best method to have a look at the end-user experience, is by enrolling a personal iOS device. In the following example that will be an iPhone 8. The 15 steps below walk through enrolling that iPhone 8, by relying on the User Enrollment. Those steps also include a few useful notes and some screenshots from were the enrollment differs from the “normal” device enrollment for personal iOS devices.
- Download and install the Company Portal app
- Open the Company Portal app and sign in using a work or school account
- On the Set up {company} access page, tap Begin
- On the Select device and enrollment type page, select I own this device and select Secure work-related apps and data only (as shown in Figure 3) and tap Continue
Note: Selecting {company} owns this device will result in a company-owned device and selecting I own this device will result in a personally-owned device.
- Back on the Set up {company} access page, tap Continue
- On the Device management and your privacy page, review the information and tap Continue
- Back on the Set up {company} access page, tap Continue
- On the This website is trying to download a configuration profile. Do you want to continue? dialog box, tap Allow
- On the Profile Download dialog box, tap Close
- Open the Settings app (as shown in Figure 4) and tap on Enrol in {company}
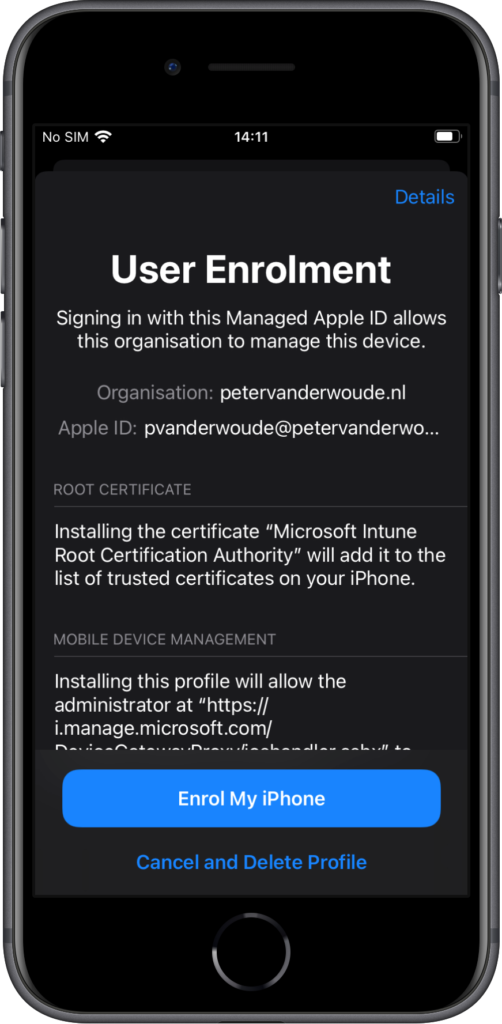
- On the User Enrollment page, review the information (as shown in Figure 5) and tap Enrol My iPhone
- On the Enter iPhone Passcode To Install Profile page, provide the passcode of your iPhone
- On the Apple ID for {company} page, tap Continue and sign in with your Managed Apple ID
- Back to the Company Portal app, tap Continue now
- Back on the Set up {company} access (now renamed to You’re all set!) page, tap Done
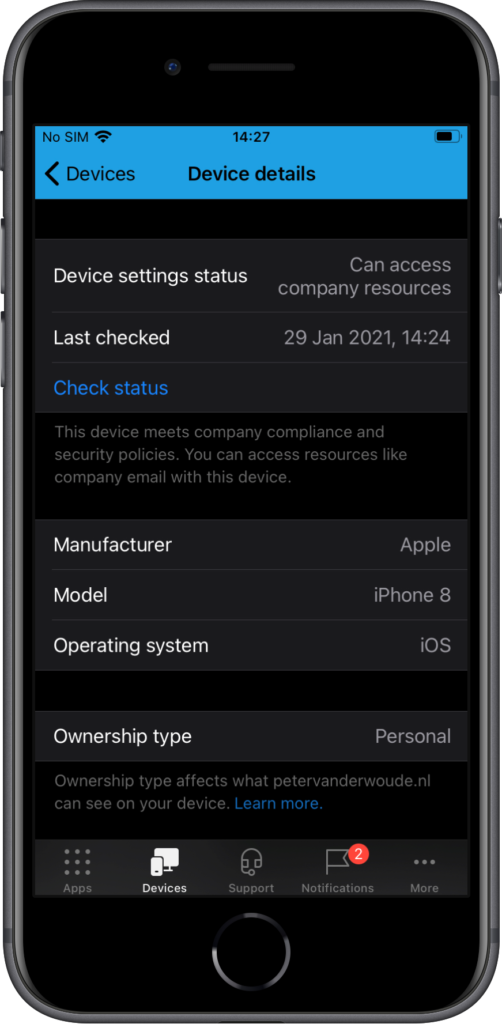
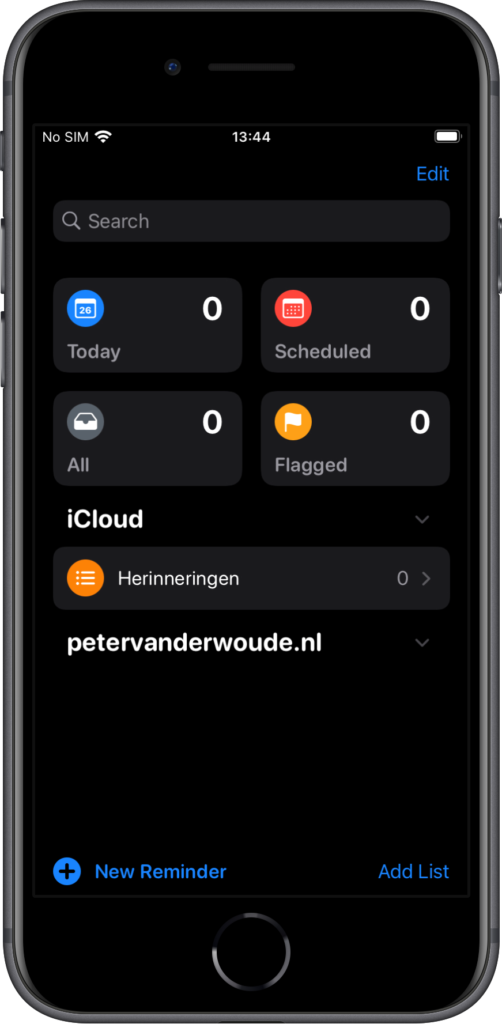
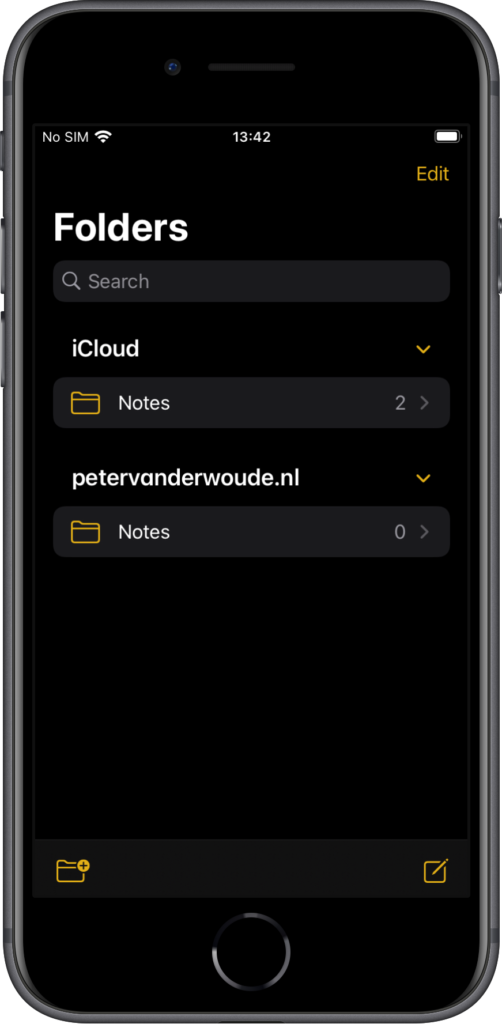
Once the enrollment is successfully completed, there are still some interesting places to look and to verify a successful enrollment. The first place to look, is of course the Company Portal app. That app shows information regarding the enrollment and the ownership of the device. The ownership is set to Personal (as shown in Figure 6). Besides that, this enrollment model also separates personal and business data. That separation is clearly shown in apps like Reminders (see Figure 7) and Notes (see Figure 8).
More information
For more information about the user enrollment for iPhone and iPad devices, refer to the following docs.
- Enrolment types for mobile device management with Apple devices – Apple Support
- User Enrolment in MDM – Apple Support
- Enroll iOS/iPadOS devices in Intune in Microsoft Intune – Microsoft Intune | Microsoft Docs
- Enroll iOS/iPadOS devices with user enrollment in Microsoft Intune – Microsoft Intune | Microsoft Docs
- Intune actions and options supported with Apple User Enrollment – Microsoft Intune | Microsoft Docs

Hi Peter
Which iOS device emulator do you use for testing your settings?
Greetings, Ákos
Hi Akos,
I’m not using an emulator, I’m still relying on physical devices. Wether it’s iOS or Android, you still need physical devices to be able to test all scenario’s.
Regards, Peter
Hi Peter,
Thanks for sharing this! I have a question regarding Figure 3, if I were to apply the exact same configuration as you did and would setup a brand new ADE device, would that automatically be excluded from this process? Since it is clearly a company device, the user shouldn’t be getting the option to chose right?
Kind regards, Julio
Hi Julio,
User Enrollment is mainly for personally-owned devices, which is what I’ve showed in this post. The device management option that you see in Figure 3 is – in my opinion – only for company-owned devices that require a manual enrollment. That means, devices that are not enrolling via ADE. When using ADE, this is not applicable.
Regards, Peter
Hi Peter,
thanks for the clarification.
Regards, Julio
Other than the need to use managed Apple ID’s, How does managing personal devices with user enrollment compare with managing them through MAM policies? Why would I choose one over the other?
Hi Steve,
I would say that the main difference is in the apps that can be used and the integration with the platform.
Regards, Peter
Hi Peter, interesting presentation yesterday!
What’s the difference between “Secure entire device” and “Secure work-related apps and data only” when it comes to pushing apps, does that even work in both scenarios? And what about Configuration Policies, do they work in either one of the scenarios?
Last one, in this blog, you picked “Determine based on user choice”, does the user still see “Secure entire device” and “Secure work-related apps and data only” during enrollment?
Thank you Jordi!
You should still be able to push apps and the policy described which settings are available for which scenario. In my blog I deliberately chose that the user can pick. That provides the user with the choice. Either other option would force a specific enrollment and would take the choice away from the UI.
Regards, Peter
So if i understand correctly, only apple services get data separation. We cannot have a work outlook and a personal outlook like Android for work?
Correct Adeel. The other data separation is within the Microsoft apps with multi-identity.
Regards, Peter
Nice article! Just a quick questions. So we could say ADE is for corporate enrolled devices and this user enrolment can be used to control BYOD devices?
Yes, that’s correct Roger!
Regards, Peter
Thank you for this article. It was very helpful. I’m looking at deploying User Enrollment with Intune for MDM and use MAM policies. Has anyone else deployed this configuration? We have 100% byod iOS devices.
We just completed Apple Business Manager enrollment. Apple support will ask who owns the devices. I told them all devices are byod. They gave me a hard time, saying ABM was for company owned devices. They must not be up to date on user enrollment. I guess they haven’t seen this Apple documentation. They did finally approve our ABM account.
https://support.apple.com/guide/deployment-reference-ios/user-enrollment-apdeb00576b2/web
Thank you for sharing your experience Brant. It’s indeed true that even their own docs refer to the requirement of ABM.
Regards, Peter
Hi Peter,
Thank you so much for the valuable information about this. I can’t found a decent documentation on Microsoft about this.
We are trying to implement the BYOD on our company and i follow the steps but i have some doubts.
I understand that we need Managed Apple ID’s for the User enrolment, but they need to be created with ABM Federation ?
I ask this because i follow your other post about how to configure the ABM federation with Azure but i found a big issue … a lot of users (54 at least) are using already our enterprise domain for personal Apple ID’s.
It’s possible to make some tests with User Enrolment without having the Federation between ABM and Azure working ?
Thank you so much
Best regards
Hi Joao,
Federation is not required, but it does provide the best user experience. So, for your testing you should be fine.
Regards, Peter
Hi managed to move forward without the federation between ABM and Azure but in the end i don’t see any data separation between personal and corporate ?
any ideas on what could be ?
Thank you so much
Hi Joao,
The differentiation is at app level. So, within some apps, there is a separate section for corporate data (as shown in the example).
Regards, Peter
Wiping a device … a little off topic but a device is company owned and are assigned directly to certain users, they pickup and quit how do we wipe the unit? I sent a wipe and it doesnt wipe the device. The device is on LTE currently and therefore i though this would work.
Hi Brian,
For an Internet-connected device, a wipe should do the trick.
Regards, Peter
Great article. Coming from a school environment where our younger students never had to use the AppStore and therefore have not needed AppleID’s in order to enroll their BYOD devices, is this the only way for a BYOD device to be user enrolled? (By downloading the Company Portal app and then logging in and enrolling).
Hi Chris,
Enrolling personal devices requires, the Company Portal app. It doesn’t, however, require an Apple ID. Only with user enrollment.
Regards, Peter
Hi Peter,
I follow up the instructions in the article as I have about 10 personal Iphones need to enroll them in intune but when I try to sign in to the company portal on the Iphone , it just login successfully and it doesn’t show the setup page.
I tried different Iphones and different users , the issue is still the same.
Iphone version is IOS 15.0
Any clue to resolve this issue?
Hi Farid,
What configurations do you have in place?
Regards, Peter
Hi Peter,
I am not able to see my device information such as Serial number on Microsoft Endpoint manager portal. However, after device enrollment, I can see it.
Is it something related to this user enrollment?
Hi jordanpal,
That is expected behavior, see also: https://docs.microsoft.com/en-us/mem/intune/enrollment/ios-user-enrollment-supported-actions
Regards, Peter
Hello,
Thank you for taking the time to share all this information, it is really difficult to find useful help for iOS devices.
In terms of the “user experience”, I tried reading your scenario as if I was a user and I stumble upon this:
“sign in with your Managed Apple ID”
What does that mean? As a user, I do not recall having a “managed Apple ID”, even less having a password for it…
How would I successfully pass that step? Will the company administrator give me a password for this account to enter during the enrollment?
Thank you for your time again,
Hi Mark,
That’s a reference to the Apple ID that should be used. It should be an Apple ID that is provided by the IT organization (and is often similar to your daily work email).
Regards, Peter
Do we believe MDM User Enrollment can totally replace MAM? I have created a restriction policy to be used in the MDM User Enrollment scenario and blocked the “Copy and paste…” from an managed to unmanaged app, however that restriction didn’t apply. It works fine on the MAM scenario. Regards, Cata
Hi Cata,
Personally, I prefer MAM above user enrollment at this moment. It’s more intuitive for user and IT administrators.
Regards, Peter
Roger that!
I know MAM for macOS is not an option, at least yet, just wonder if you know or heard if that is something will ever come?
Thx again,
Cata
Hi Cata,
No, I’ve haven’t seen or heard anything about that yet.
Regards, Peter
Hi Peter,
Great work as usual.
In terms of assigning apps and device configuration policies. Would you target these at the device or the user in this instance. Normally we would use a Dynamic device group to target apps and policies based on the enrolment profile used. User enrolled devices just seem to use the default enrolment profile and not the “user enrolment” profile type.
Hi Andy,
Yes, the devices are harder to filter. I often rely on user groups for this.
Regards, Peter
Hi Peter,
Found a little quirk on my tenant. If you choose “My Company owns this phone”, the devices is not tagged with the profile name. However if you choose “Personal”, the device is tagged with the profile name…..would have thought it would be the other way around.
Regards
Andy
Hi Andy,
I would say that the behavior makes sense. User enrollment is for personal devices and not for company devices.
Regards, Peter
Hi Peter… this article helped me a lot, thanks for sharing!
If I may, two questions: right now we’re already using Android-Enterprise and the WorkProfile for BYOD Devices, of course we want to allow iOS Devices as well.. hence reading this article. Am I correct in understanding that with UserEnrollment on a private iPad there’s separation in storage but not in apps like in Android we have – for example – two versions of Outlook running side-by-side. One personal and one from the WorkProfile container. I’m testing this with my personal iPad which is now “AAD registered” and I could setup my work-e-mail in the Outlook app. So basically UserEnrollment allows access (if blocked by ConditionalAccess) and that’s it. Or am I missing something here?
Second question: trying to present or even push apps to personal owned user enrolled devices, like my iPad in this example I made MS-Teams available for my groups. When I open CompanyPortal for a split second I see an overview of those recently added apps (search bar on top, recently published apps, categories) but with a blink of an eye that page is gone an it only shows “Hello… no apps available.” and how many devices I have registered. And there is no way for me to return to the page I saw. What’s going on there? We have ABM setup with all the things, federated domain acconts, vpp-tokens and all this is synced and working fine apparently. Is it even possible on a personal user erolled device to push an app after aad regsistration is completed?
Any hint much appreciated, if not no worries we’ll figure it out. Apple stuff just new to us.
Hi Andreas,
You’re correct. You can’t compare managing Android with iOS. Android has the separation on a profile-level, which creates the experience of two separate apps. iOS, however, has the separation on a data-level. That allows the user to use a single app with a separate location for the data (see also the example screenshots).
Regards, Peter
Hmkay yes it’s just a knot in my head to get the concept right, like how does the feature look at the end. Thanks. Bummer though, really enjoy the Android profile-container feature.
Hi Andreas,
I understand. The best overview is shown in Figure 7 and 8. So, for the user a single app, with multiple storage locations.
Regards, Peter
Personal owned device selected during enrollment and secure work related related apps and data only does NOT allow automated install of apps (doesn’t matter if VPP or ios App Store.. ie. Outlook, Office, Edge, Teams). However if option selected as personal owned device and secure entire device selected then apps are successfully pushed to device.
Issue with this, company or org should not have ability to wipe entire phone for BYOD devices. This ability appears when personally owned and secure entire device selected. But, this is the only way to get apps auto deployed to ios devices.
Do you see this as “by design” or “bug” ? Have you tested this scenerio ?
Hi Grant,
You should be able to deploy user-licensed VPP apps to those devices.
Regards, Peter
Deploying of apps via VPP Licensing is possible – but if the user has the app alredy installed via Apple Appstore these app belive unmanaged – there is no “converting” to managed.
Sample: User installs Outlook mobile on private device, CA-Rule blocks the connection – user have to register the device. User is registering the device with user registration – voila, the alredy installed (unmanaged) Outlook is able to use the corporate account (no CA blocking – device is registered now). In this case the planned VPP-based installation of outlook via intune is waiting and will be not finished.
This is a huge problem, mailbox-content can be shared with any app. Is there a solution for this behavior?
Ah, now I understand. To prevent the mailbox content from being shared, you might want to have a look at app protection policies.
Regards, Peter
With app protection only a limited set of restrictions is available – we want to establish a “real” management of BYOD devices. As i can see i cannot block the usage of personal installed app with app protection policies (right?) – the management of company-apps and -data needs to be done via mdm inside the “coporate” area.
That’s true. However, besides the limited functionality of user enrollment, Apple doesn’t provide real MDM (besides full management).
Regards, Peter
Hi Peter
How do you setup Intune Company Portal, I need tit to pop up, when enrollment is done?
Hi Carsten,
Not sure what you mean. When using user enrollment, it requires the user to download the Company Portal app first, and to start the enrollment via the Company Portal app.
Regards, Peter
Hi Peter,
I trying to find out how iOS user enrollment can be used in our company for supporting BYOD. We are allready using Intune for managing company owned devices and use ADE for this and all works fine.
To test user enrollment I have configured our Intune as explained in your article and have created a managed Apple ID (not federated yet) and managed to enroll a privately owned iOS device though user enrollement. Everything looks as expected and for example Apple data (like notes) are kept seperate. Also a iOS mail config profile gets pushed and mail is kept seperated from the personal email.
Where I get stuck is how I can deploy and configure company apps on this device. Apps do not get enrolled and fail with an error code: 0x87D13BA9. This is a unknown error and Google also cannot clarify this error. However some apps (like Outlook and Teams) were already installed on the device. An for example when I start Teams a company account is added to Teams. But I did not configure any app config policies for that. My guess is that because I am athenticated through the Authenticator app these accounts are created in the MS apps.
Is my assumption correct that only managed app config policies can be assigned to user enrolled devices to configure apps. That would somehow unusable because the apps that can be managed by managed app config policies are limited. Or is it possible to define cutom apps by Bundle ID?
Regards,
Tjitze.
Hi Tjitze,
Are you saying that you can’t deploy any app (via VPP) to those devices?
Regards, Peter
Hi Peter,
That is correct. I cannot deploy an app through VPP to a device which is enrolled through uder enrollment. I get the error mentioned above.
Also app config policies are not applied, but the app config policies I have are managed device app config policies. As the name says they are only for corporate owned devices (or am I wrong about this?).
Regards,
Tjitze.
Hi Tjitze,
Are those apps user licensed?
Regards, Peter
Same error for me
Scenario
User1 with ADE managed iPhone, VPP apps deployed correctly with device assignment/licensing and filtered to Corp devices. All works fine
User1 then also enrols iPad via User enrollment profile. Same VPP Apps have been made Available via Company Portal with User licensing filtered to Personal devices
On iPad, the apps show in Company Portal but when user tries to install it fails. Intune shows 0x87D13BA9 as the reason the apps did not install.
At a guess, it is trying to use the already assigned Device license for the user on the iPad so fails.
Are you saying that the assignment with the device licensing is also applicable to the user enrollment setup?
Regards, Peter
I’m experiencing the same issue code (0x87D13BA9).
In my case there is the need that the company has personal (BYOD) and corporate (COPE, ADE enrolled) devices.
Scenario 1: Use Case: Corporate Devices should auto-install the app silently, personal device users should be able to download the app.
Config 1:
Required: All devices with device based licensing, but only included for COPE devices via Filter (EnrollmentProfile -eq ProfilenameForCOPE)
Available: All Users with user based licensing, but excluded for COPE Devices
Result 1: 0x87D13BA9
—
Scenario 2: Use Case: Corporate Devices as well as BYOD should be able to download the app using the correct licensing method.
Config 2:
Required: none
Available:
– Static User group with users using a corporate device
– All Users with user based licensing, but excluded for COPE Devices
Result 2: seems to be working BUT the downside:
– we have to use a static group. Not that nice.
– What happens if there is a user with two devices, one as COPE, one as BYOD. > not working of course. :-/
Thank you for that, Patrick!
It is indeed important to apply the correct licensing method to the app on the device.
Regards, Peter
Hi Peter,
It seems like that is the problem at my side. I have assigned the apps to a user group but as a device license type.
So for BYOD (User Enrollment) apps have to be assigned as user licensing type?
Regards,
Tjitze.
Yes! For User Enrollment the apps have to be assigned using the user licensing.
Regards, Peter
This is the problem, it is not configuration, it is that Intune doesn’t apply licensing correctly. Even with the correct configuration to apply Device licenses to CORP devices and User licenses to BYOD it fails. From what I can see so far, it is not possible for a single user to have a CORP iPhone and BYOD iPad. CORP works fine but BYOD does not.
Using Microsoft Teams as an example. I enrol CORP iPhone, it auto installs with the device license based on filter. I then enrol BYOD iPad and filter shows that it is a personal device which should receive User license. Instead of assigning a new User type license it tries to assign the existing device license which means the app fails to install on BYOD
Happy to be wrong if anyone has a working solution.
Ah, okay. So, a user with a BYOD device would work correctly? If so, I would suggest to contact support.
Regards, Peter
Hi David,
See my post of july 6th. Licenses are applied correctly of you assign apps the right way with using filters.
I have managed te get it working by assigning apps to users, applying filters which determine if it concerns a BYOD or COPE device and setting the right license type for the corresponding assignment.
Ragards,
Tjitze.
Hi Patrick,
I have tried the following scenario for deploying apps in a COPE / BYOD mixem invironment:
Required:
– User group for COPE, include filter for COPE devices ((device.deviceOwnership -eq “Corporate”)), license type Device
– User group for BYOD devices, include filter for BYOD devices ((device.deviceOwnership -eq “Personal”)), license type User
The user I tested with is member of both groups. Result is that the app is getting deployed on the COPE device as well on the BYOD device enrolled through User enrollment.
In my case the user group for COPE is a AD synced group and the user group for BYOD is a static AAD group. But I think the type of group does not matter here. It’s all about correct use of the filter and license type.
Next step is how to get config profiles and app config profiles applied the right way on the right device. But I guess the correct use of filters will do the trick again.
Regards,
Tjitze.
(Got a few issues while writing the reply, sorry Peter)
Thanks for the discussion and your ideas!
Without wanting to sound snobbish i think i’ve got a quit good understanding of Intune, iOS Deployment and VPP logic. But nevertheless i didn’t manage to get these things working as reliable as necessary.
Sometimes it is working, sometimes it isn’t.
I am not very surprised that the MS Support ticket wasn’t that successful yes.
Afterwards I’ve tested working with dynamic device groups, whats working quite good, but of course not for available asssignments, because this is only possible with user groups.
Hopefully it is allowed to share the techcommunity link to discuss this further?: https://techcommunity.microsoft.com/t5/microsoft-intune/vpp-licensing-issues/m-p/3653323
In my opinion these are the most feasable “workarounds” atm:
– try to don’t have users with more than 1 device (1x Corp, 1x BYOD)
– if still necessary: Corp = MDM, BYOD = MAM/App Protection (
to go around the licensing nightmare :D)
– Case 1 is possible, if a single user only has one type of device: Two assignments with two user groups: (Corporate users group > License Type Device, Personal User Group > License Type Personal)
– Case 2 is possible, if a single user only has one type of device: (Static User group for corporate device users > device licensing & All Users group for User Liensing but with a Filter (Exlcudce COPE)
– didn’t manage to get Case 3 working in a reliable way.
No worries, Patrick! I totally understand that it can be easier to use a public forum for this discussion.
Regards, Peter
Hi Peter,
Thanks for the blog. In my environment I would like to restrict the user not to enroll their personal device. For BYOD, I’ve enabled MAM policy. My question is If I enabled this enrollment type as Device enrollment, will the BYOD device enrollement get restrict?
Hi Karthick,
You should use “Device platform restrictions” to prevent the enrollment of personal devices.
Regards, Peter