This week a short blog post to address a scenario that’s been challenging for a while. That scenario is around removable USB-drives and automatic encryption. When organizations have configured that removable drives require encryption, that introduces challenges with storage built into specialized devices like video cameras, voice recorders, conferencing systems, medical devices and many more. That would also require that type of storage to be required, when read access wasn’t sufficient. That, however, would often cause more problems than solutions. To address that challenge, Microsoft has introduced a new policy. That policy can be used to create an exclusion list of devices for which the user will not be prompted for encryption. Even when encryption of removable drives is required. This post will introduce that new policy setting and will walk through the configuration of that policy setting. This post will end with the user experience.
Note: The configuration to require encryption of removable drives is referring to using the RemovableDrivesRequireEncryption policy setting when using MDM, or to using the Deny write access to removable drives not protected by BitLocker when using Group Policy.
Important: This post relies on functionality that is at the moment of writing only available in Windows 11 Insider Preview Builds in the Dev Channel. Setting is available starting with Windows 11 Insider Preview Build 22579.
Creating custom device configuration policy to exclude removable drives
Starting with Windows 11 Insider Preview Build 22579, Microsoft introduced a new policy setting as part of the BitLocker CSP. That new policy setting is RemovableDrivesExcludedFromEncryption. A nice self explanatory setting that can be used exclude removable drives from the encryption requirement. That setting requires a String data type value of the Hardware ID of the removable drive. The Hardware ID can be found in the Details tab in the Properties of a device in the Device Manager. When multiple drives should be listed, the different values can be separated by a comma. The following nine steps walk through the process of adding this new policy setting in Microsoft Intune and distributing it to Windows 11 devices.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile to open the Create a profile page
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile type: Select Templates as value
- Template name: Select Custom as value
- On the Basics page, provide a unique Name to distinguish the profile from other custom profiles and click Next
- On the Configuration settings page (as shown below in Figure 1), click Add to open the Add Row page. On the Add Row page, provide the following information and click Add (and click Next back on the Configuration settings page)
- Name: Provide a valid name for the OMA-URI setting as value
- Description: (Optional) Provide a valid description for the OMA-URI setting as value
- OMA-URI: Provide ./Device/Vendor/MSFT/BitLocker/RemovableDrivesExcludedFromEncryption as value
- Data type: Select String as value
- Value: Provide the HardwareID of the USB-drive as value
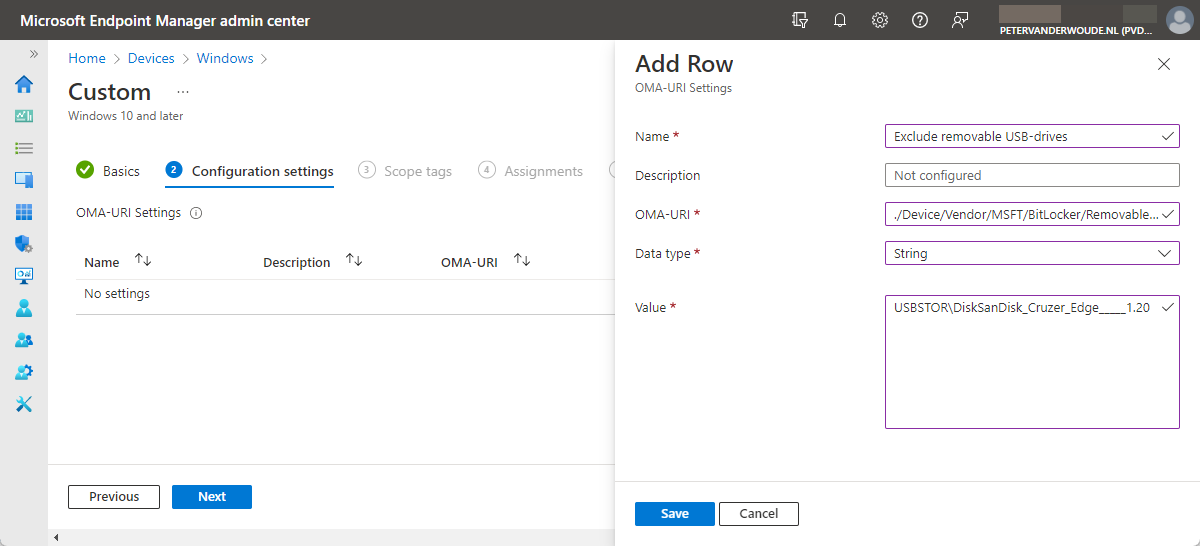
Note: The configuration in Figure 1 is using the Hardware ID of a SanDisk removable USB-drive as an example.
- On the Scope tags page, configure the applicable scopes and click Next
- On the Assignments page, configure the assignment and click Next
- On the Applicability rules page, configure the applicability rules (think about the existence of this setting for only the specific Windows Insider build and later) and click Next
- On the Review + create page, verify the configuration and click Create
Note: The expectation is that this policy setting will, in time, become directly configurable within the Microsoft Endpoint Manager admin center, as part of one of the existing configuration templates (or the Settings Catalog).
User experience with excluded removable drives
When looking at the user experience, the most important part is that the removable USB-drive works for the user. That can be shown by physically insertting a removable USB-drive in to the device. That, however, is impossible to show in a screenshot. What can be shown is a succesful exclusion in the Event Viewer. The System log contains Event ID 24701 that provides information about the exclusion, once the user inserts the removable USB-drive. That event revers to the volume (as shown with number 1 and 3 in Figure 2) and the specific Hardware ID (as shown with number 2 in Figure 2). The Hardware ID relates to the configured Hardware ID in the created configuration.

More information
For more information about the new setting to exclude removable USB-drives, refer to the following docs.

Hi Peter, thank you for yet another clear instruction of new functionality coming from Microsoft. Your blogs are always interesting to read. I do have a couple of questions on this if you could help.
The first one is easy, do you know if the settings will be back-versioned to Windows 10?
The second one is an odd one, your instructions state to put the HardwareID of the device into the Value, you are testing with “USBSTOR\DiskSanDisk_Cruzer_Edge____1.20”, if, for example I plugged in a new Cruze Edge USB and the version was____1.21, could I change the original string to “USBSTOR\DiskSanDisk_Cruzer_Edge____1” to incorporate both or would I need to create a new config?
Hi Rob,
There is not a lot of documentation around this setting yet, but at this moment it’s Windows 11 only. Besides that, I think it’s not allowing variables and it would require a full string of the HardwareID.
Regards, Peter
Thankyou Peter, your response is much appreciated. Hopefully it will be made available for Win10 at some point.
Good Morning guys,
is it possible to exclude an existing user from being encrypted by their USB while using bitlocker in intunes?
Thanks!
Regards, Armin
Hi Armin,
You can create a separate configuration profile for that user.
Regards, Peter
Hi Peter, I need your guidance in this. Do we have option to block automatic encryption for all removable drives/usb irrespective of model .If yes, how this can be accomplished ?
Hi Magesh,
Can you provide some more context about your scenario?
Regards, Peter
Hi Peter,
Thank you very much, awesome read.
Even better than the first-party-knowledge-base!
is there any way to integrate this feature into classic Microsoft Endpoint Configuration Manager (the on-prem one)?
Thanks again, Christoph.
Hi Christoph,
As it configures via a CSP, you can always use PowerShell for the configuration.
Regards, Peter
What would the command or syntax look like to apply this with PowerShell, I have been unable to find it and I am trying to run this on a test endpoint no connected to InTune.
Hi Barclay,
I haven’t checked, but when it’s available via the MDM Bridge WMI provider, this will get you started: https://www.petervanderwoude.nl/post/windows-10-mdm-bridge-wmi-provider-settings-template/
Regards, Peter
Hi Peter,
How do i add multiple USBs?
If i add one it works perfectly fine, however when i add a second usb it doesn’t work?
Can you assist?
Kind regards,
Jack
Hi Jack,
Good news. The settings is now also available via the Settings Catalog. That enables you to easily add multiple lines.
Regards, Peter
multiple lines to the Value field?
Nope. A value per line.
Regards, Peter
In the Settings catalog, the setting is labelled “Removable Drives Excluded From Encryption (Windows Insiders only)”.
Is this accurate that it only applies to Windows Insiders, or is that likely to be outdated or to indicate it works for Windows 11 only?
I would have thought if the OMA-URI works to configure the CSP, the settings catalog would work too.
Hi Matt,
The CSP docs mention that it’s now Windows 11 21H2 and later: https://learn.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp#removabledrivesexcludedfromencryption
Regards, Peter
I have tried this and it is still only Windows 11. But there is a serious problem with the implementation. The HardwareID you have to put in is not unique to a specific USB drive. It is the same value for all drives of the same type from the same manufacturer. I bought several of the same USB drives. I needed to bypass the encryption for write access to one of them. But this bypassed for all of them.
Hi David,
Is that specific to a vendor, or in general?
Regards, Peter
Hi Peter
It is specific to a vendor. Here are Hardware IDs from some of our USB drives:
USBSTOR\DiskSanDisk_Ultra___________1.00
USBSTOR\DiskSanDisk_Cruzer_Blade____1.00
USBSTOR\DiskSony____Storage_Media___0100
USBSTOR\DiskImation_Classic_________PMAP
The ID includes the vendor name.
According to Microsoft, “A hardware ID is a vendor-defined identification string that Windows uses to match a device to a driver package. A hardware ID identifies what a device is to some level of specificity and is indicating that any driver package that declares it can work with a device that has that ID can work with this device for some degree of functionality.”
So it is really up to the vendor to determine how many different types of their brand of USB drive would have the same Hardware ID.
This does not work well in our scenario. We want the general rule to be that removable storage is encrypted as it could store personal, private or confidential information. But sometimes we need to be able to write to a USB drive that will then be used in a situation where having it Bitlocker encrypted is not appropriate.
What I would really like to be able to do is provide an exception list based on the serial number of the USB drive. If you use the following command, you can get the serial number of the drives in a system:
wmic diskdrive get Model, Name, InterfaceType, SerialNumber
The output from this command for my SanDisk Ultra USB drive is:
InterfaceType : USB
Model: SanDisk Ultra USB Device
Name: \\.\PHYSICALDRIVE3
SerialNumber: 4C530001291026121572
Regards
David
Thank you for that suggestion, David!
You also might want to provide that as feedback to Microsoft: https://feedbackportal.microsoft.com/feedback/forum/ef1d6d38-fd1b-ec11-b6e7-0022481f8472
Regards, Peter
Is it possible to retrieve a list with hardware ID’s with KQL. In other words – is it possible to retrieve the devices that ‘hit’ the Bitlocker to go (removable devices) possible with the devicename and the primary user. I don’t want to bother people in the org to investigate by themself which specific USB device is used to make the exceptions (if allowed)
Hi Maarten,
It depends. Are you storing the information centrally? If so, you can use that the find the required information.
Regards, Peter
Not sure. I’m trying to figure out if the action to force the encryption of the USB storage device is written to a Device Event table. If so, than i should be able to KQL the thing. I’m going to investigate this.
Keep me posted. I only know for sure that it’s in the System log on the local device.
Regards, Peter
Hello Peter,
We have a user based policy from Intune to enforce bitlocker encryption on USB for all users.
However, I would like to try out your steps on a user who has a need to use a specific USB device which is already encrypted by a third party vendor, I wanted to make sure the user still gets bitlocker prompt whenever user insert any other USBs.
Question: Where do I apply your policy? to user system?
Thanks in advance.
Solu E
To apply to a specific device, you should assign it to a device.
Regards, Peter