This week is all about Windows Sandbox. About two years ago I wrote a post about simply enabling Windows Sandbox, by using a simple PowerShell script and distributing that script by using Microsoft Intune. Windows Sandbox is a really nice feature for running applications in an isolated environment. That isolated environment supports simple configuration files, which provide a minimal set of customization parameters. With the latest version of Windows 10, the administrator receives some controls for enforcing specific customization parameters. That won’t prevent the user from creating a configuration file, but that does prevent specific customization parameters from applying to the Windows Sandbox. In this post I’ll briefly go through the currently available policies, followed with the steps of configuring those policies. I’ll end this post by showing the configuration result.
Important: This blog post relies on the WindowsSandbox node in the Policy CSP, which is currently only available in the latest Windows insider builds (my current build is 21296).
Available Windows Sandbox policies in the Policy CSP
With Windows 10, version 1903 (19H1), Windows Sandbox was introduced, including different customization parameters. Those parameters can be configured by creating a configuration file. That configuration file can be used to configure vGPU (virtualized GPU), networking, mapped folders, logon command, audio input, video input, protected client, printer redirection, clipboard redirection and memory in MB.
Starting with the latest Windows insider preview builds, some of these settings are coming to the Policy CSP. The Policy CSP now includes a node of WindowsSandbox with policy settings in the device scope. These are ADMX-backed policy settings (WindowsSandbox.admx). By default the different policy settings are enabled and for most of these policy settings, security is the main reason for potentially disabling them. Those policy settings can help with preventing information from leaking via the isolated environment and with preventing the isolated environment from accidentally infecting the production environment.
The currently available policy settings are described below.
| Policy setting | Description |
|---|---|
| AllowAudioInput | This policy setting can be used to configure the audio input to the Windows Sandbox. |
| AllowClipboardRedirection | This policy setting can be used to configure sharing of the host clipboard with the Windows Sandbox. |
| AllowNetworking | This policy setting can be used to configure networking in Windows Sandbox. |
| AllowPrinterRedirection | This policy setting can be used to configure printer sharing from the host into the Windows Sandbox. |
| AllowVGPU | This policy setting can be used to configure virtualized GPU for Windows Sandbox. |
| AllowVideoInput | This policy setting can be used to configure video input to the Windows Sandbox. |
Note: When disabling one of the policy settings, users won’t be able to enable the setting via a configuration file. The setting can still be part of the configuration file, but won’t be applied when the policy setting is disabled.
Configure Windows Sandbox via a custom device configuration profile
The different Windows Sandbox policies, can be configured by using a custom device configuration profile. That profile can be used to apply the different Windows Sandbox policy settings. The next 9 steps walk through the process of creating a custom device configuration profile and adding OMA-URI settings.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Windows > Configuration profiles to open the Windows | Configuration profiles blade
- On the Windows | Configuration profiles blade, click Create profile to open the Create a profile page
- On the Create a profile page, provide the following information and click Create to open the Custom wizard
- Platform: Select Windows 10 and later as value
- Profile type: Select Custom as value
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the custom device configuration profile
- Description: (Optional) Provide a valid description for the custom device configuration profile
- On the Configuration settings page, click Add to open the Add Row page. On the Add Row page, provide the following information and click Add (and click Next back on the Configuration settings page)
- Name: Provide a valid name for the OMA-URI setting
- Description: (Optional) Provide a valid description for the OMA-URI setting
- OMA-URI: Specify ./Vendor/MSFT/Policy/Config/WindowsSandbox/{policysetting} as value
- Data type: Select Integer as value
- Value: Provide 0 as value to disable the setting
Note: Within the OMA-URI replace {policysetting} with any of the policy settings of the table above. Repeat these steps for every required setting.
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required users and/or devices and click Next
- On the Applicability rules page, configure the applicability rules (think about the existence of this setting for only the existence of these policy settings for only the latest Windows insider build) and click Next
- On the Review + create page, verify the configuration and click Create
Note: At some point in time this configuration will probably become available in the Microsoft Endpoint Manager admin center portal without the need of creating a custom device configuration profile.
Results of the Windows Sandbox configuration
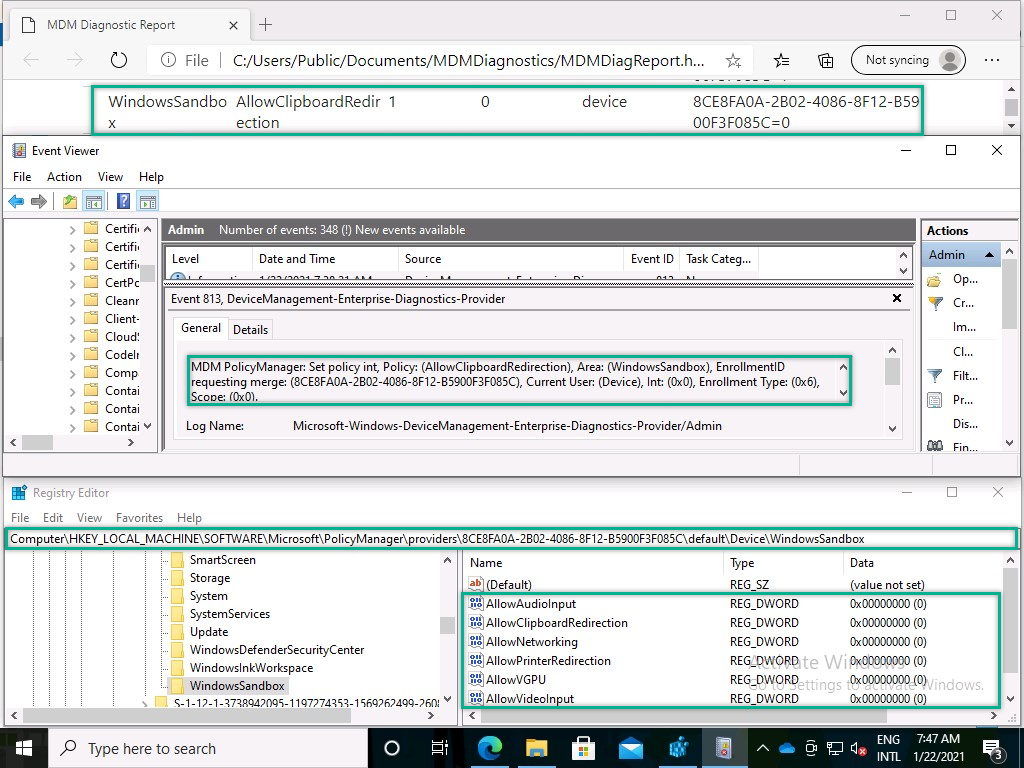
Verifying the applied configuration in a screenshot is challenging, as the main impact is on users creating a configuration file. Everything else doesn’t really show that well in an image. That’s why I thought – once again – that showing the applied configuration would be the best, as the configuration is only shown when successfully applied. Below in Figure 2 is an overview of the MDM Diagnostics Report, the Event Viewer and the Registry Editor. All of those locations show at least one policy setting, its value, its scope and its provider. All of those green lights mean a successful configuration.
More information
For more information about the different subjects that are used throughout this post, refer to the following docs.


Hey Peter, great post! One minor suggestion: the screenshots do not display fully in the article, you have to click on them to view them. Outside of that, thank you for the breakdown!
Thank you for your message Firras. The images seem to be fine on my side.
Regards, Peter