This week is all about the Microsoft Enterprise SSO plug-in for Apple devices. Both, iOS/iPadOS and macOS devices. That plug-in provides single sign-on (SSO) for Azure AD accounts across all apps that support the enterprise SSO feature of Apple. The plug-in is provided on iOS/iPadOS devices as an extension of the Microsoft Authenticator app and the plug-in is provided on macOS devices as an extension of the Company Portal app. The extensions can be enabled by using Microsoft Intune. In this post I’ll start with having a look at the configuration options, followed with the configuration steps. I’ll end this post by having a look at the end-user experience.
Important: Keep in mind that, at the moment of writing, this is still preview functionality.
Configuration options for the Microsoft Enterprise SSO plug-in
Let’s start by having a look at the configuration options for the Microsoft Enterprise SSO plug-in. The Microsoft Enterprise SSO plug-in, is a redirect-type SSO app extension. That plug-in provides SSO for Azure AD accounts across all apps that support the enterprise SSO feature of Apple and that authenticate via Azure AD. That includes accessing websites via supported browsers. In those cases, the SSO plug-in acts as an advanced authentication broker. The SSO plug-in is provided on iOS/iPadOS devices as an extension of the Microsoft Authenticator app and the SSO plug-in is provided on macOS devices as an extension of the Company Portal app. Configuring the SSO app extension will enable the SSO plug-in. The redirect SSO app extension configuration, for iOS/iPadOS and macOS devices, is provided in the table below.
| Property | iOS/iPadOS | macOS |
|---|---|---|
| Type | Redirect | Redirect |
| Extension identifier | com.microsoft.azureauthenticator.ssoextension | com.microsoft.CompanyPortalMac.ssoextension |
| Team identifier | SGGM6D27TK | UBF8T346G9 |
| URLs | https://login.microsoftonline.com | https://login.microsoftonline.com |
| https://login.microsoft.com | https://login.microsoft.com | |
| https://sts.windows.net | https://sts.windows.net | |
| https://login.partner.microsoftonline.cn | https://login.partner.microsoftonline.cn | |
| https://login.chinacloudapi.cn | https://login.chinacloudapi.cn | |
| https://login.microsoftonline.de | https://login.microsoftonline.de | |
| https://login.microsoftonline.us | https://login.microsoftonline.us | |
| https://login-us.microsoftonline.com | https://login-us.microsoftonline.com |
Note: The information in the table above is taken from a configured iPadOS device (Settings > General > Device Management > Management Profile > More Details > Authenticator) and a configured macOS device (System Preferences > Profiles > Extensible Single Sign On Profile – {GUID}). Those devices were configured by using the configuration steps provided in this post.
This all means that, to use the SSO app extension, an administrator should make sure that the correct app is installed and that the correct configuration is applied. That configuration can only be applied when the device is managed. Once the correct app is installed and the SSO app extension is configured, users can enter their credentials to sign in, and establish a session on their Apple device. That session is then used across the different supported apps, on their Apple device, without requiring users to authenticate again.
Note: Make sure to use the latest version of the Microsoft Authenticator app (iOS/iPadOS) and the latest version of the Company Portal app (macOS).
In addition to the default behavior, there are additional configuration options available to extend the SSO functionality to additional apps. Those settings are described in the table below and are recommended.
| Key | Type | Value | Description |
|---|---|---|---|
| browser_sso_interaction_enabled | Integer | 1 | This key and value enables non-MSAL apps and Safari browser to do the initial bootstrapping and get a shared credential. |
| disable_explicit_app_prompt | Integer | 1 | This key and value restricts ability of both native and web applications to force an end-user prompt on the protocol layer and bypass SSO. |
Configuring the Microsoft Enterprise SSO plug-in
Once the configuration options and requirements are clear, it’s time to look at the configuration of the Microsoft Enterprise SSO plug-in. The configuration for iOS/iPadOS and macOS devices is identical. Only the platform is different. That platform difference will make sure that the correct configuration is applied to the correct app. The following eight steps walk through the steps to configure the Microsoft Enterprise SSO plug-in.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Configuration profiles to open the Devices | Configuration profiles blade
- On the Devices | Configuration profiles blade, select Create profile to open the Create a profile page
- On the Create a profile page, provide the following information and click Create
- Platform: Depending on the platform of choice select iOS/iPadOS or macOS
- Profile: Select Device features
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the device features profile
- Description: (Optional) Provide a valid description for the device features profile
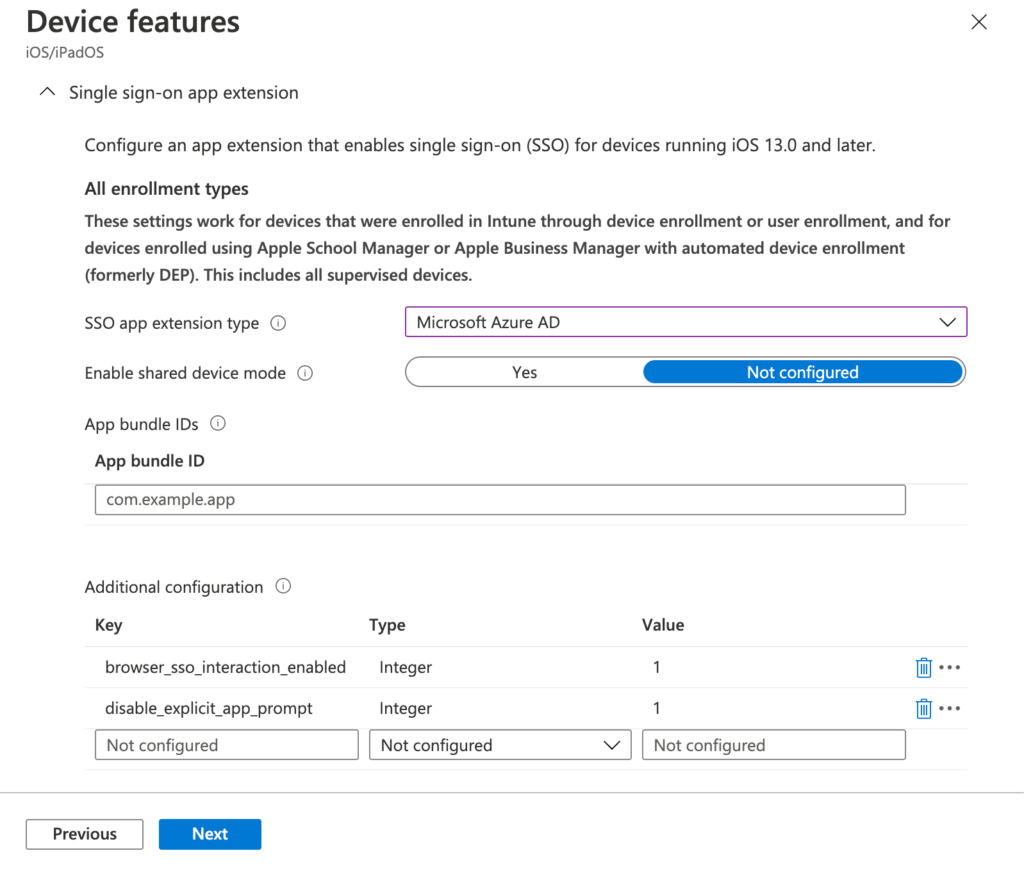
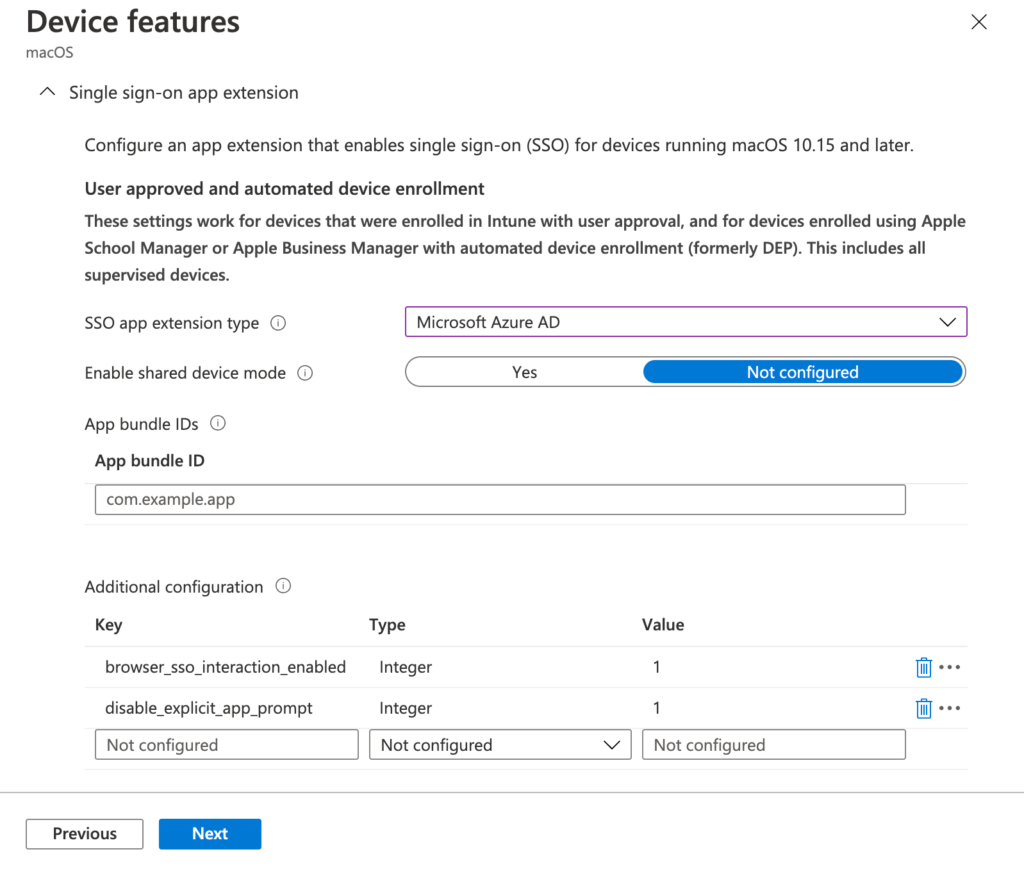
- On the Configuration settings page, configure at least the Single sign-on app extension section by providing the following information (see Figure 1 for an example configurations for iOS/iPadOS and see Figure 2 for an example configurations for and macOS) and click Next
- SSO app extension type: Select Microsoft Azure AD
- Enable shared device mode: Select Not configured
- App bundle IDs: Add the bundle identifiers of any additional app that should use the Microsoft Azure AD single sign-on extension and that doesn’t use the (latest) Microsoft libraries
- Additional configuration: Configure the earlier mentioned key-value pairs
- Key: browser_sso_interaction_enabled; Type: Integer; Value: 1
- Key: disable_explicit_app_prompt; Type: Integer; Value: 1
Note: When the earlier described configuration is not sufficient, because more URLs are required, configure a SSO app extension type of Redirect, start with providing the described configuration and add the additional URLs.
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required users and/or devices and click Next
- On the Review + create page, verify the configuration and click Create
End-user experience with the Microsoft Enterprise SSO plug-in
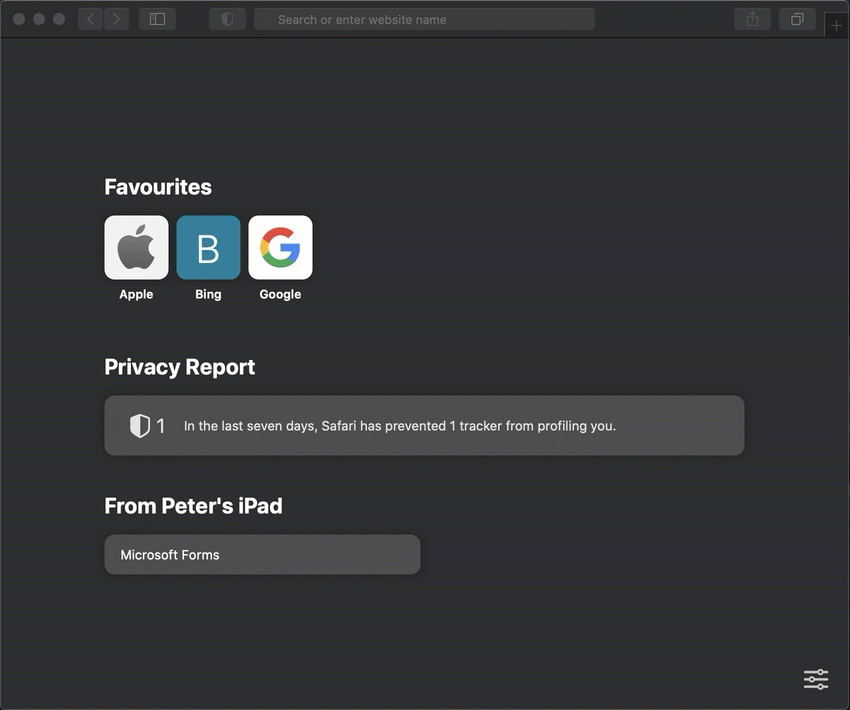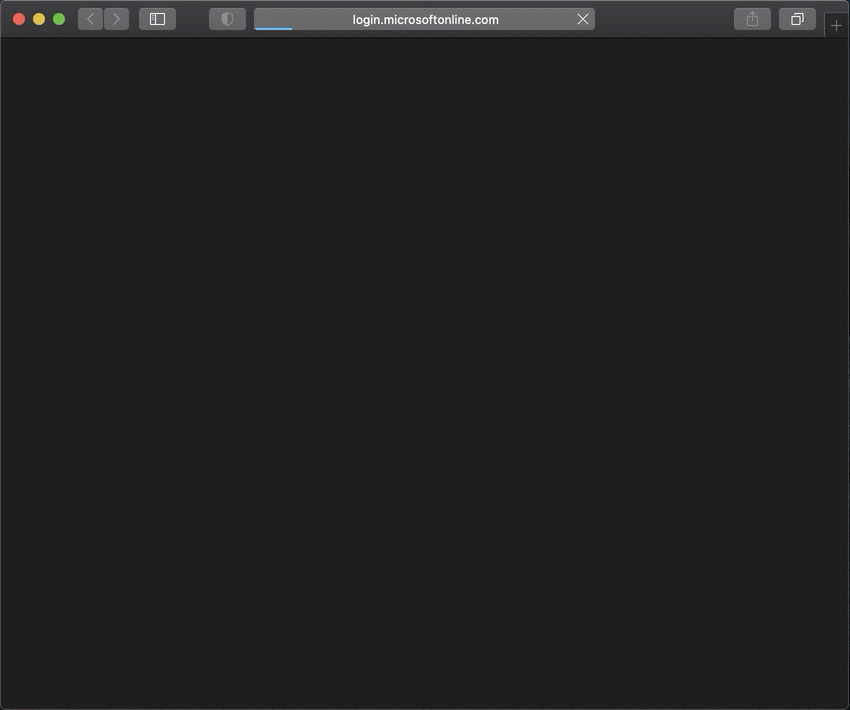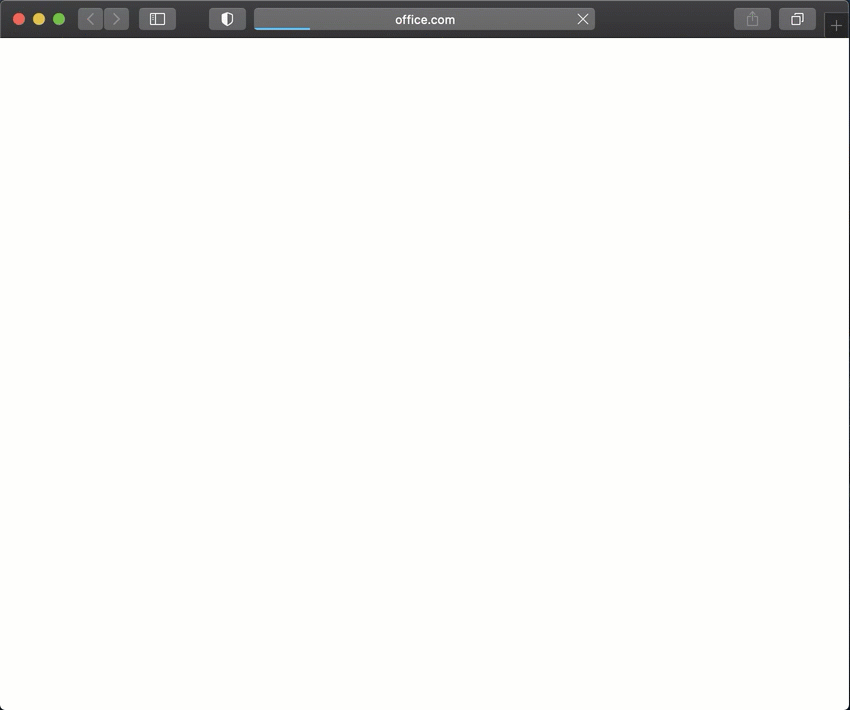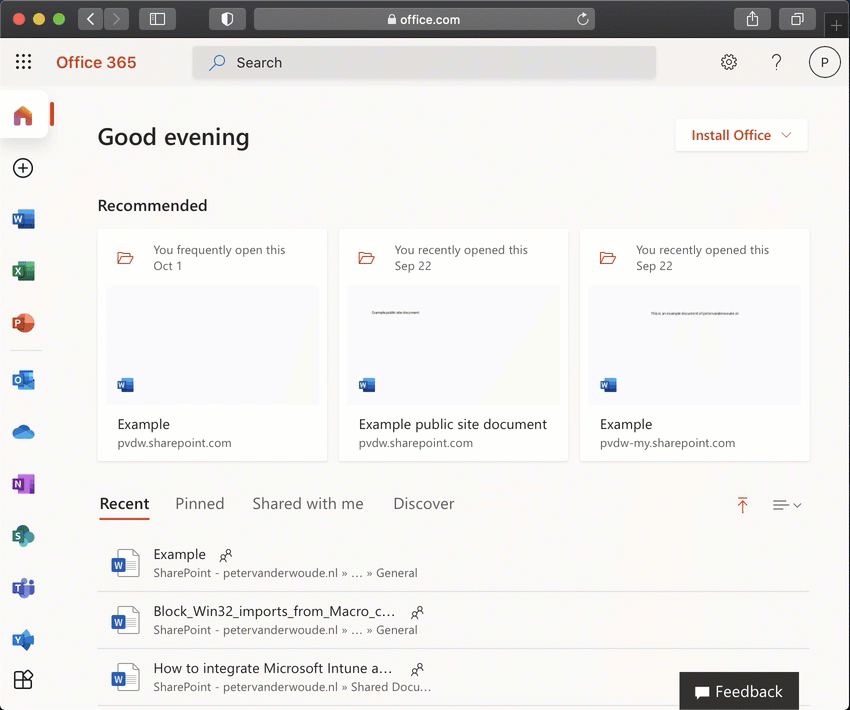
Now let’s end by having a look at the end-user experience with a configured Microsoft Enterprise SSO plug-in. To create the best picture, I’ve used a Safari browser on a macOS device and the experience was awesome. That experience is shown below, in Figure 3, by navigating to portal.office.com and simply picking the required account.
Note: The end-user experience is identical on iOS/iPadOS devices.
More information
For more information about the Microsoft Enterprise SSO plug-in and configuring device features on iOS/iPadOS and macOS devices, refer to the following docs.
Great article!
Have you gotten the shared device mode working?
Hi Anders,
I haven’t really looked at that yet. What’s the challenge that you’re running in to?
Regards, Peter
Hi Peter,
Did you manage to get this working on Chrome/Firefox/Edge browser on macOS?
Hi Nishant,
So far, I’ve only focussed on the Safari browser.
Regards, Peter
Hi Peter,
so does that mean that for iOS/iPadOS I need to have the Microsoft Authenticator App installed and configured on a device to be able to make use of the SSO extension?
Regards
Julio
Hi Julio,
Yes! On iOS/iPadOS you need the Microsoft Authenticator app.
Regards, Peter
Hi Peter,
what if you already have a 3rd party authenticator app in place? Is there a way to bypass the Microsoft Authenticator App or is there a way to integrate it with a 3rd party app?
Kind regards
Julio
Hi Julio,
At this moment the functionality is part of the Microsoft Authenticator app.
Regards, Peter
Peter, do we just need to install Authenticator app on device or need to set up app too ?
Hi Suraj,
The user doesn’t need to use or configure the app.
Regards, Peter
Does the SSO work as per the above end user experience if we have ADFS to authenticate the user identity.
Hi Jinks,
I haven’t tested it, but I would expect it to work.
Regards, Peter
It does work well in Safari, little too well. It doesn’t respect in-private browser sessions anymore, it just automatically logs you in. Also, when you log out en choose to log in with another account, a new tab automatically takes over that particular first session. Which to me, is a little worrying. One of the great things in Safari is that every in-private browser session is actually sandboxed from other sessions (other browsers could learn from that).
Is there a way to isolate in-private browser sessions from these settings?
Hi Marco,
I can reproduce the behavior of the in-private browser sessions. Just not the new tab behavior. I haven’t found out how to mitigate that behavior yet.
Regards, Peter
Hi Peter and thanks for your article!
I’m struggling to understand because both Microsoft and you are mixing their recommendations regarding the SSO extension type.
Do I need to create two policies with same settings but one with Redirect and one with Microsoft Azure AD?
Hi Emil,
Eventually both configure nearly the same settings.As mentioned in my post, the only difference is in the added URLs. The Microsoft Azure AD type does the basic standard configuration and the Redirect type allows custom configuration.
Regards, Peter
Hi Peter ,
Okay so what you mean is that both are using the same technology(redirect) in the backend and the redirect option just enables you to add some more config and custom parameters to it?
Thanks!
That is correct Emil.
I have the SSO Kerberos Extension configured which authenticates to Azure AD and works well with share drives however for some reason the MS Office apps still prompt our users to sign in even though they are authenticated with Azure.
Is it possible to have a true SINGLE sign on experience with MS Office apps?
Ideally the new users deployment process should go,
1, user logs into device for the first time
2, the user signs into an SSO extension
3, the user is not prompted to sign in again until their ticket expires.
However our users are logging into the SSO extension then being prompted to login again when they open Outlook or Teams for the first time.
Hi Rory,
This configuration is really focused on using Microsoft Azure AD as the SSO extension type. That should provide the SSO experience in the different supported apps and browsers. For MacOS that does require the additional configuration setting of browser_sso_interaction_enabled.
Regards, Peter
I have Azure AD credentials federated as Managed Apple ID.. In this case, How do I make the Apple app store and iCloud account signed in using the SSO.
is there any bundle ID for that?
Hi Jack,
I haven’t specifically tested that scenario, but I would think that there isn’t a bundle ID for that (as it’s not really an app).
Regards, Peter
I can deploy Company Portal app via script after MacOS enrols through Apple DEP but when I sign into Company Portal still wants profile installed even though it is installed during DEP process, I am concerned that Company Portal app install and sign in is required and if process isn’t completed my SSO experience isn’t working.
Plenty of people online with same issue with MacOS DEP and Company Portal install.
Anyone been able to solve this issue?
Hi Brendan,
Are you using Setup Assistant with modern authentication?
Regards, Peter
Hey Peter, yep setup assistant with modern auth
See the suggestion by Hans.
Regards, Peter
Hi Brendan, I had same issue, the account you use is an (DEM) enrollment account, then you get exactly this error.
Hello Peter,
Does SSP extension supports to shared iPad enrolled without user affinity ? We have requirement to target teams, office apps like word,excel to shared iPad, if we configured SSO extension then will it allow seamless sign in on these apps without prompting for credentials ?
Regards,
Suraj
Yes, Suraj, but only when it’s supported by the app.
Regards, Peter
Is it supported by Word and Excel? Because in my experience it doesn’t work.
Hi Rob,
I haven’t recently looked at those apps, but theoretically Microsoft apps should already work with Enterprise SSO (assuming they already have MSAL implemented).
Regards, Peter