This blog post is about an Azure preview feature. A preview may include preview, beta, or other pre-release features, services, software, or regions. Previews are subject to reduced or different service terms. In other words, previews are for early testing and should not be considered as fully production ready.
During the session Secure access to Office 365, SaaS, and on-premises apps and files with Azure AD and Intune, at Microsoft Ignite, a nice new feature for mobile app management without enrollment (MDM-less MAM) was shown. That new feature is conditional access for managed apps. During that session they showed the URL to that new feature. What makes it even better, that specific URL already works with existing tenants. It simply brings the administrator to a public preview feature.
During this blog post I’ll provide some information about this new feature, I’ll go through the currently available configuration options of this new feature, I’ll show the end-user experience with this new features and I’ll provide my first impression with this new feature.
Information
This new feature will enable an administrator to restrict access to Exchange Online and SharePoint Online so that access can come only from managed apps such as Outlook, Word, Excel, PowerPoint and OneDrive. This new feature also pairs up perfectly with Intune mobile app management (MAM) policies, as it enables the administrator to block access to built-in mail clients or other apps that have not been configured with the Intune MAM policies.
During my first tests with this new feature I noticed that on iOS the Microsoft Authenticator app is required and on Android the Microsoft Intune Company Portal app is required.
Configuration in the Azure portal
Now let’s have a look at the configuration of this new feature. The conditional access policies are configured through the Azure portal, just like the MDM-less MAM policies. I’ll first go through the different configuration options followed by the basic step-by-step configurations.
Different configuration options
The conditional access policies in the Azure portal, contain three different configuration sections. These three sections together are the targeted conditional access policy. Let’s go through these three sections and see how they fit together.
Basic steps
After getting familiar with the different configuration options, it’s time to look at the creation and the targeting of a conditional access policy. The following 10 straight forward steps will guide anyone through the configuration and targeting.
| 1 | Open the Azure portal via this link and navigate to Intune mobile application management > Settings to open the Settings blade; |
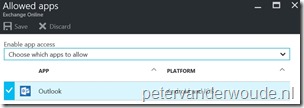
| 2 | In the Settings blade, click Exchange Online to open the Exchange Online blade; |
| 3 | In the Exchange Online blade, click Allowed apps to open the Allowed apps blade; |
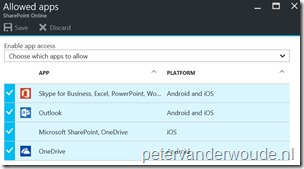
| 4 | In the Allowed apps blade, select the allowed apps. |
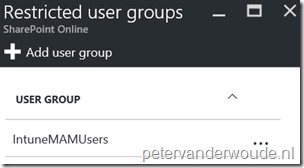
| 5 | Back in the Exchange Online blade, click Restricted user groups to open the Restricted user groups blade; |
| 6 | In the Restricted user groups blade, click Add user group to open the Add user group blade; |
| 7 | In the Add user group blade, select an user group and click Select to save the changes and to return to the Restricted user groups blade. |
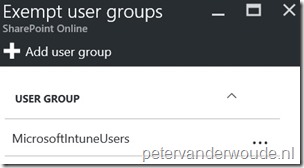
| 8 | (Optional) Back in the Exchange Online blade, click Exempt user groups to open the Exempt user groups blade; |
| 9 | (Optional) In the Exempt user groups blade, click Add user group to open the Add user group blade; |
| 10 | (Optional) In the Add user group blade, select an user group and click Select to save the changes and to return to the Exempt user groups blade. |
Note: The same steps are applicable to the configuration for SharePoint Online. The only real difference is the selection of SharePoint Online instead of Exchange Online.
End-user experience
Now it’s time to have a look at the end-user experience. When an end-user is targeted with a conditional access policy for managed apps and the end-users wants to use one of the blocked apps, the end-user will get the messages below after providing company credentials. The first message will show after adding a company email account to the native mail client and the second message will show after using a blocked app.
| Native mail client | Blocked app |
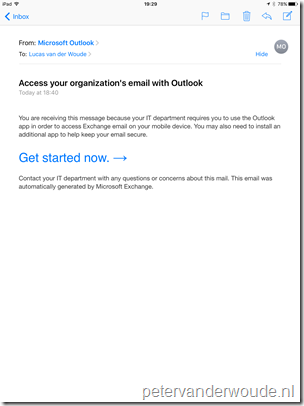 |
 |
First impressions
My first impressions of this new feature are mixed, from a great addition to leaving room for improvements. The idea of blocking apps that are not managed is great and is something that would be an awesome addition to the product. Especially when looking specifically at MDM without enrollment. However, at this moment it’s not blocking everything. There are three section that I can see a need for improvement:
- Only the native mail client on Android and iOS is blocked with Exchange Online. Other mail apps, not using modern authentication, are a hit-miss exercise;
- Only apps using modern authentication are blocked with SharePoint Online. Other apps can still connect and sync data;
- Browser access is not blocked.
1 thought on “Conditional access for managed apps (preview)”