This blog post is about a potentially really great feature, which is a combination of MAM-WE and app configuration policies. This enables the administrator to provide a preconfigured app, once the end-users signs in to the app with company credentials. I named it a potentially really great feature, because the availability of apps that support this combination of features will make or break the use of this feature. In this post I’ll provide a quick introduction to this feature, followed by a configuration example with the Intune Managed Browser.I’ll end this post with the end-user experience.
Introduction
Let’s start with a quick introduction. MAM-WE with app configuration, also known as MAM targeted configuration, allows an app to receive configuration data through the Intune App SDK. The format and variants of this data (the keys and values) must be defined and communicated by the application owner/developer. The Microsoft Intune administrators can target and deploy the configuration data via the Intune Azure console. The app configuration data is pushed through the MAM Service directly to the app, instead of through the MDM channel.
Configuration
The configuration in this post will be based on the Intune Managed Browser, which is, to my knowledge, currently the only app that works with this great combination of features. At this moment, MAM targeted configuration is available on iOS and Android. For iOS, the app must have incorporated Intune APP SDK for iOS (v 7.0.1) and be participating in app configuration settings.
Available settings
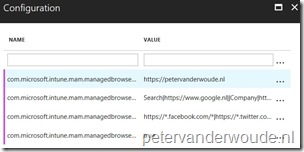
Before starting with the actual configuration, let’s start by looking at the available configuration settings. The nice thing is that very recently a few configuration keys have been released by Microsoft. The Intune Managed Browser can now be preconfigured for Azure AD App Proxy redirection, with a specific homepage, with a list of bookmarks and with a list of allowed or block websites. That provides us with the following list of keys and example values. The name of the keys provide a clear indication of their configuration usage.
| Key | Example value |
| com.microsoft.intune.mam.managedbrowser.AppProxyRedirection | true |
| com.microsoft.intune.mam.managedbrowser.homepage | https://www.petervanderwoude.nl |
| com.microsoft.intune.mam.managedbrowser.bookmarks | Search|https://www.google.nl |
| com.microsoft.intune.mam.managedbrowser.AllowListURLs | https://*.petervanderwoude.nl/* |
| com.microsoft.intune.mam.managedbrowser.BlockListURLs | https://*.facebook.com/* |
Note: The separation character for multiple bookmarks is || and the separation characters for multiple allow/block URLs is |.
Configure app configuration policy
After looking at the available settings, let’s have a look at the actual configuration. The configuration of MAM targeted configuration, can be done by using the Azure portal and following the steps below. After creating the app configuration policy, don’t forget to assign it to an user group.
| 1 | Open the Azure portal and navigate to Intune App Protection > App configuration; |
| 2 | Select Add Config to open the Add app configuration blade; |
| 3 | 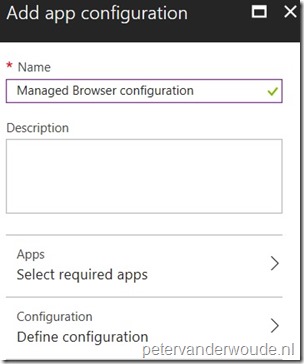 On the Add app configuration blade, provide a unique name for the app configuration policy and select App to open the Targeted apps blade; On the Add app configuration blade, provide a unique name for the app configuration policy and select App to open the Targeted apps blade; |
| 4 | 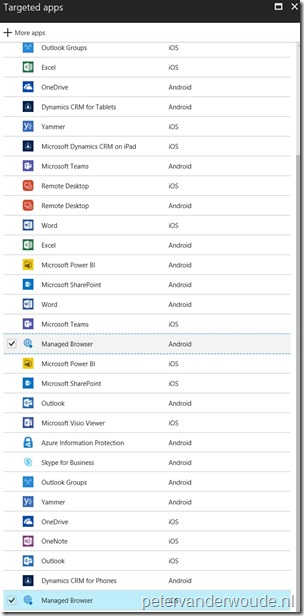 On the Targeted apps blade, select the Managed Browser (Android), the Managed Browser (iOS) and click OK to return to the Add app configuration blade; On the Targeted apps blade, select the Managed Browser (Android), the Managed Browser (iOS) and click OK to return to the Add app configuration blade; |
| 5 | Back on the Add app configuration blade, select Configuration to open the Configuration blade; |
| 6 |
|
| 7 | Back on the Add app configuration blade, click Create; |
End-user experience
Let’s end this post by looking at the end-user experience. I created an app configuration, as mentioned in this post, but added a couple more bookmarks. Below are a couple of examples of the Intune Managed Browser on an iOS device. On the left is an example of an app configuration including a homepage, and on the right is an example of an app configuration excluding a homepage.
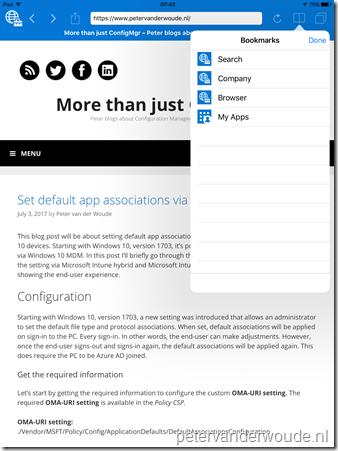 |
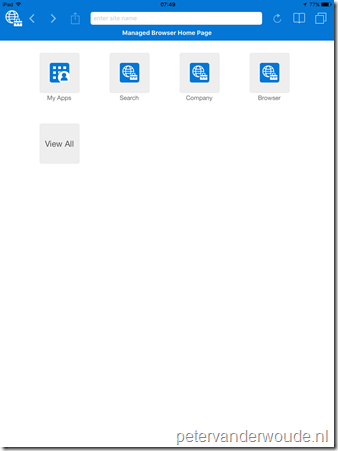 |
More information
For more information about configuring the Intune Managed Browser, please refer to this article about Manage Internet access using Managed browser policies with Microsoft Intune.
The 9Folder Inc. application, Nine Work for Intune, supports the configuration key/value pairs provided by MAM-WE App Config policies.
I’ve been investigating it recently as I use their normal Nine application as my default email client. Many customer are complaining that the Outlook App isn’t good enough to force on end users, and I’m inclined to agree. The Nine app allows much more end-user productivity.
I’m hoping one day that Intune will allow us to select non-Microsoft apps for use in the conditional access tab of the Intune App Policy blade.
I’m not affiliated in any way with 9Folders – I just love their client and can see how it would be useful to customers who aren’t willing to inflict Outlook on their users.
The details of the MAM Config Policy can be found here – http://ninework-faq.9folders.com/articles/16933-how-to-use-nine-work-for-intune-and-set-configuration
Thank you for the information Dae!