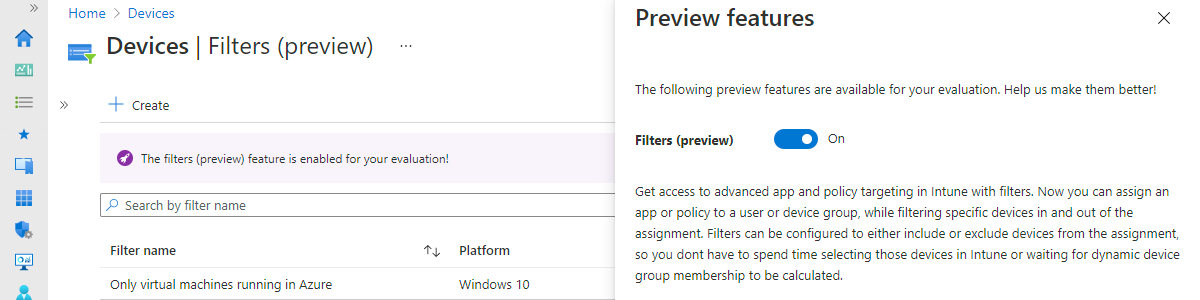
Using filters for assigning apps, policies and profiles to specific devices
This week is all about filters. Filters are basically a super-set of the functionalities of applicability rules – already available for a while for Windows 10 – and are a great new addition to assigning apps policies and profiles to specific devices. Those specific devices are only the devices that meet the specific properties that are configured in the filters. A great method for specifically targeting apps, policies and profiles. This post starts with a short introduction about filters, followed with information about creating and using filters (including the steps for using and creating filters). This post ends with the administrator experience with filters. Introducing filters For device configuration profiles for Windows 10 devices it was already possible to use applicability rules. Applicability rules would …