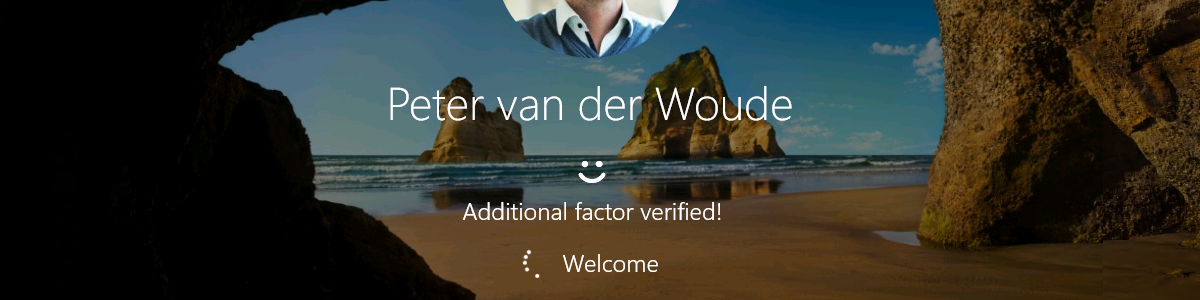
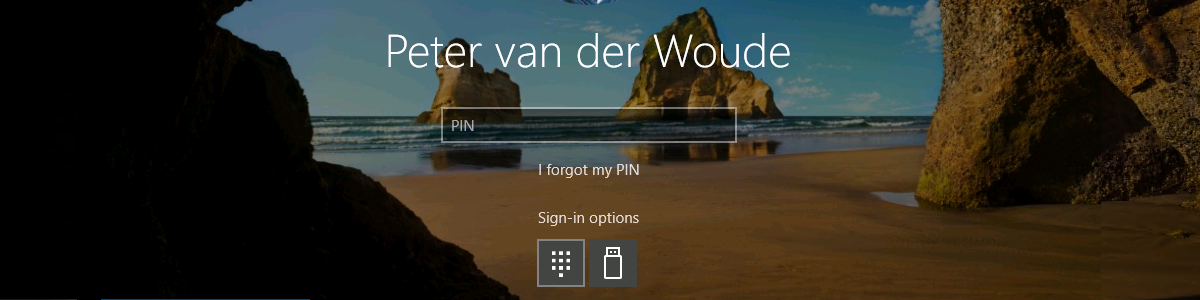
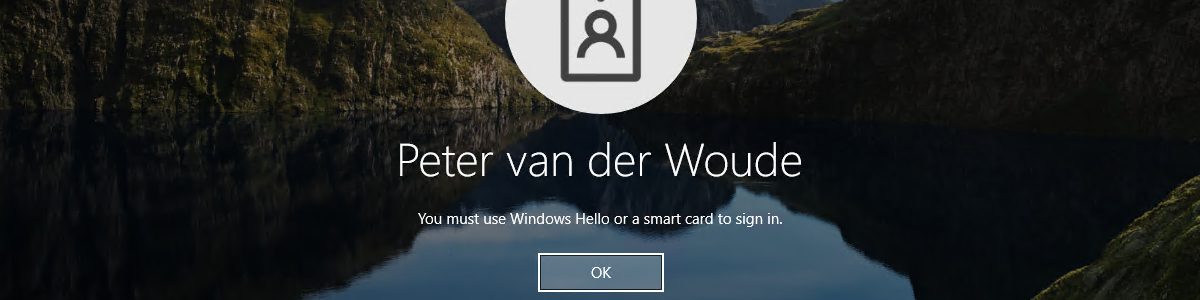
Enabling web sign-in to Windows for usage with Temporary Access Pass
This week still continues the journey through Windows Hello for Business. The last few weeks were all about direct Windows Hello for Business functionalities, while this week is all about providing alternatives besides Windows Hello for Business. When looking at standard Windows functionality, those alternatives are FIDO2 security keys and the relatively new combination of the web sign-in credential provider with Temporary Access Pass (TAP). The web sign-in credential provider itself is nothing really new, but the ability to use it in combination with TAP is something relatively new. Simply because TAP is relatively new. TAP is a time-limited passcode that basically temporarily enables users to sign-in. That sign-in is focused on getting users up-and-running with passwordless authentication and on helping users recover access to …