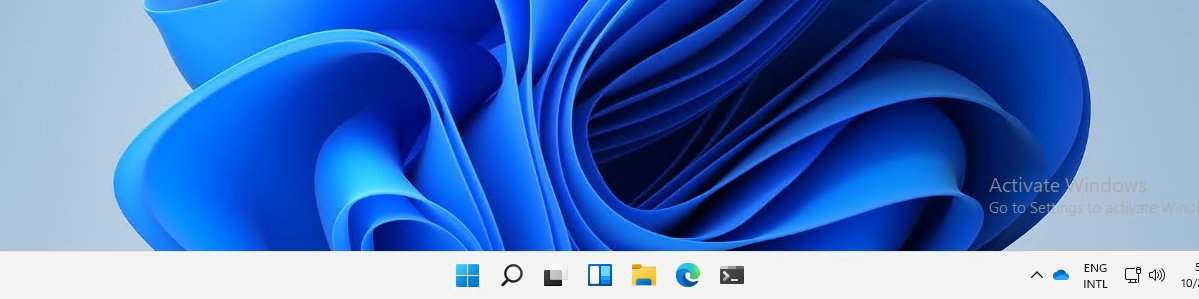
Customizing the Taskbar on Windows 11 devices
This week is a follow-up on last weeks post about customizing the Start menu layout on Windows 11 devices. This week, however, is focused on customizing the Taskbar layout on Windows 11 devices. Customizing the Taskbar layout enables organizations to create a standardized layout for their users. With the arrival of Windows 11, the configuration options for customizing the Taskbar layout have changed. Especially from a setting-by-setting perspective the options are now rather limited. This post does a quick breakdown of the Taskbar layout in Windows 11 and the different configurations that are available, per section. That breakdown is followed with a zoom-in on the actual configuration for creating the standardized layout. This post ends with showing the user experience with a customized Taskbar layout. …