This week a new blog post about a little nice, but quite unknown, feature. Applicability rules for device configuration profiles. The nice thing about applicability rules is that those rules can be used to target devices in a group that meet specific criteria. That enables an administrator to assign a device configuration profile to all users, or all Windows 10 devices, but only actually apply to Windows 10 devices of a specific version or edition. In this post I’ll go through the configuration of applicability rules (including a few important details) and the administrator experience.
Configure applicability rule
Let’s start by looking at applicability rules. Applicability rules can be configured for every device configuration profile type with Windows 10 and later as Platform, with the exception of Administrative Templates as Profile Type. It enables the administrator to only assign the device configuration profile to a specific version or edition of Windows 10.
Before looking at the configuration of applicability rules, it’s good to be familiar with a few important notes about assigning a device configuration profile including applicability rules. When assigning such a device configuration profile, keep the following in mind:
- When two device configuration profiles are assigned with the exact same settings, and only one of those profiles has an applicability rule configured, then the profile without an applicability rule is applied.
- When assigning device configuration profiles to groups, the applicability rules act as a filter, and only target the devices that meet the specified criteria.
Now let’s have a look at the actual configuration of applicability rules. The following steps walk through the configuration of applicability rules in device configuration profiles for Windows 10 devices.
- Open the Microsoft 365 Device Management portal and navigate to Devices > Windows > Configuration profiles to open the Windows – Configuration profiles blade
- Select an existing device configuration profile, or create a new device configuration profile and navigate to Applicability Rules to open the Applicability Rules blade
- On the Applicability Rules blade, configure a rule click Add to add the rule and click Save
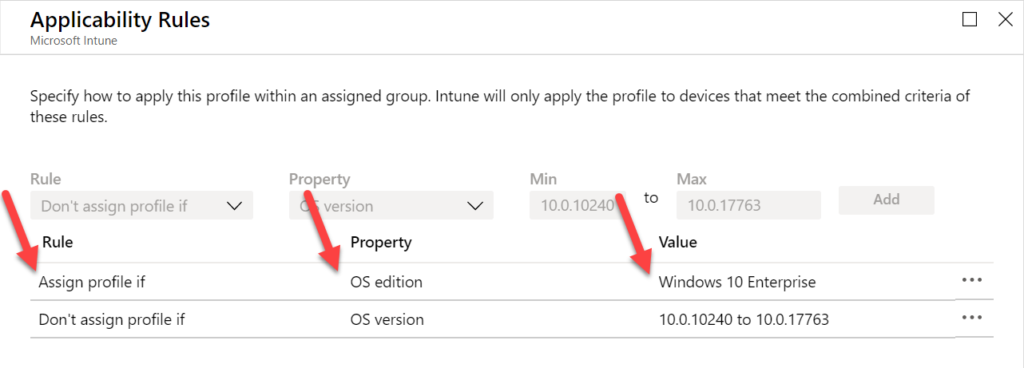
Figure 1: Applicability rules options
- The Rule selection enables the administrator to either use Assign profile if – that will include users or groups that meet the specified criteria – or use Don’t assign profile if – that will exclude users or groups that meet the specified criteria –.
- The Property selection enables the administrator to either use OS edition – that will enable a list to check the Windows 10 editions that must be included – or use OS version – that will enable fields to enter the min and max Windows 10 version numbers that must be included –. Both values (min and max) are required.
Administrator experience
Let’s end this post by shortly mentioning the administrator experience. The experience is not that exiting actually. When an applicability rule is applicable to a device, the device is targeted with the configuration profile. The device will try to assign the configuration profile and simply show the normal Succeeded, Error or Failed status. When an applicability rule is not applicable to a device, the device wil not be targeted with the configuration profile and the configuration profile will get the status of Not applicable.
Figure 2: Example
More information
For more information regarding applicability rules for device configuration profiles, refer to the Applicability rules section of the Create a device profile in Microsoft Intune doc.
Hi
thank you for the read up on “not applicable”
however I still have a question relating to windows updates
when I do reporting on a Windows update ring in Intune about 25% of the Windows 10 systems(1803 and higher) will have a status in the report as being “Not applicable”
how do I handle this especially for SLA reporting – I need to be able to explain this in hand of Windows Updates
thank you
Hi Mike,
The applicability rules of this post are not applicable to Windows update ring policies, so I’m not sure what you’re refering to. What type of policies are you using with what configuration and what is the behavior that you’re seeing?
Regards, Peter
If i assign a configuration profile to all users, but the profile is platform specific to certain devices, i assume the profile will only target that platform?
So one can avoid making to many dynamic device groups to seperate the platforms
Hi Thomas,
Yes, a profile is always specific to a platform.
Regards, Peter
How do you scope the “max”-value?
Lets say I want to configure this:
Policy CSP – LocalUsersAndGroups
https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localusersandgroups#localusersandgroups-configure
which is available from Windows 10 Version 20H2
now before 20H2 you should instead use this:
Policy CSP – RestrictedGroups
https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-restrictedgroups#restrictedgroups-configuregroupmembership
looking here:
https://docs.microsoft.com/en-us/windows/release-health/release-information
we can see that version 20H2 is the build 19042
so I should scope “LocalUsersAndGroups” from build 19042.572 which is the earliest build of version 20H2 but which value should I enter as the “end”-value?
19042.964 is the current latest build (released 2021-04-28 / checked 2021-04-29) but if I were to scope it:
10.0.19042.572 to 10.0.19042.964 but when a new build is released then the policy will no longer apply for the device?
Sorry if this is something that is quite self-explanatory but I can’t get my head around it.
Best Regards – Karl
Hi Karl,
You can just use the last number before the version number that you need for 20H2 (see for an example also: https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-create#applicability-rules).
Regards, Peter
Hi,
Thank you for your reply.
I understand I can scope pre-20H2 policies by just specifying the last version number before 20H2 was released which would be 10.0.19041.964 so for “Policy CSP – RestrictedGroups”;
10.0.18363.476 – 10.0.19041.964
Start: Just taken randomly, the first release of “1909”
End: The last release of “2004” before “20H2”
However for “Policy CSP – LocalUsersAndGroups” I would specify the first version of “20H2” which would be 10.0.19042.572 but when I am required to specify the end I just add a somewhat random version number to avoid the policy being “out-of-scope” when a newer version then the latest is released?
Best Regards – Karl
Hi Karl,
When you don’t need to make it more granular, you can just use 10.0.19042
Regards, Peter