This week is all about Android Enterprise fully managed devices. More specifically, the recently introduced functionality to use Android Enterprise fully managed devices in combination with conditional access. To support this functionality Microsoft introduced a new app, named Microsoft Intune app, and a new profile type for device compliancy policies for the Android Enterprise platform. Together these 2 features enable Android Enterprise fully managed devices to be registered as compliant device and to successfully work with conditional access. In this post I’ll provide some information about the Microsoft Intune app and I’ll show how to configure that app, followed by some information about the compliance policy for device owner scenarios and how to configure that policy. I’ll end this post by showing the end-user experience.
Keep in mind that Android Enterprise fully managed devices is still preview functionality. There are still scenarios that will not fully work at this moment. One of those scenarios is related to app protection policies. I specifically mention that scenario, as it can conflict with the scenario in this post. Apps with app protection policies assigned, will still prompt for the Company Portal app.
Microsoft Intune app
The first part in using Android Enterprise fully managed devices in combination with conditional access is the Microsoft Intune app. The Microsoft Intune app is a new modern and light-weight app that will enable the Company Portal app experiences for end-users on fully managed devices. That includes managing compliance for their device. Keep in mind that the Microsoft Intune app is only for the fully managed device scenario. As Android Enterprise fully managed devices require the Managed Google Play Store, the following 4 steps walk through the process of adding the Microsoft Intune app by using the Managed Google Play Store. After that the Microsoft Intune app can be assigned as any other app.
Keep in mind that after the May 2019 service roll out of Microsoft Intune, the Microsoft Intune app will automatically be added to the Intune admin console after connecting the tenant to managed Google Play.
| 1 | Open the Azure portal and navigate to Microsoft Intune > Client apps > Apps to open the Client apps – Apps blade; |
| 2 | On the Client apps – Apps blade, click Add to open the Add app blade; |
| 3a | 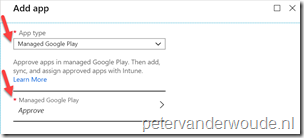 On the Add app blade, provide the following information and click Sync; On the Add app blade, provide the following information and click Sync;
|
| 3b | On the Search managed Google Play blade, search for the Microsoft Intune app; |
| — |  |
| 3c | On the Search managed Google Play blade, select the required app and click Approve to open a dialog box with app permissions; |
| — | 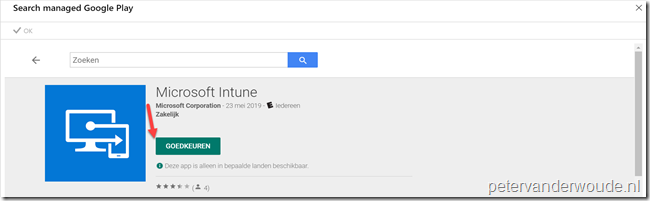 |
| 3d |
Important: Keep in mind that this will accept these permissions on behalf of the organization. |
| 3e |
Important: Keep in mind that this decision might impact the future app permissions and/or the future user experience. |
| 3f | On the Search managed Google Play blade, click OK; |
| — | 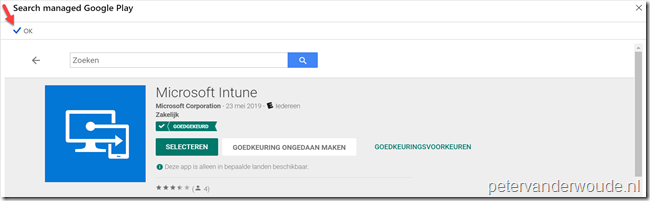 |
| 4 | Back on the Add app blade, click Sync; |
Note: These steps will approve the app in the Managed Google Play store and sync the approved app in to Microsoft Intune..
Compliance policy for device owner
The second part in using Android Enterprise fully managed devices in combination with conditional access is the compliance policies. Since recently it’s possible to create compliance policies for fully managed devices. The list of available compliance settings is smaller than other platforms. The main reason for that is because those settings are only applicable to fully managed devices. And fully managed devices are, as the name already implies, fully managed. In other words, fully managed devices already follow strict configuration policies. The following 5 steps walk through the process of creating a device compliance policy for Android Enterprise fully managed devices. After configuring the device compliance policy assign it to a user group like any other device compliance policy.
| 1 | Open the Azure portal and navigate to Microsoft Intune > Device compliance > Policies to open the Device compliance – Policies blade; |
| 2 | On the Device compliance – Policies blade, click Create Policy to open the Create Policy blade; |
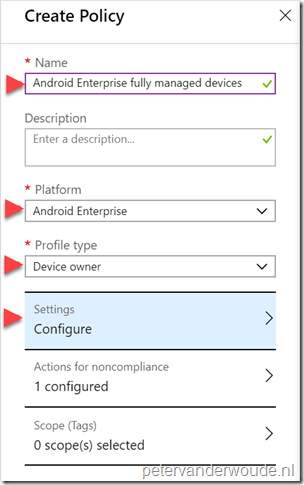
| 3a |
Note: Configuring non-standard values for Actions for noncompliance and Scope (Tags), is out of scope for this post; |
| 3b |
|
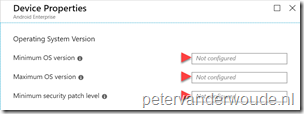
| 3c | 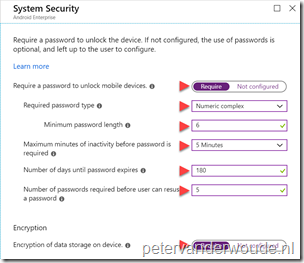 Back on the Device owner blade, select System Security to open the System Security blade. On the System Security blade, configure the required system security settings and click OK to return to the Device owner blade; Back on the Device owner blade, select System Security to open the System Security blade. On the System Security blade, configure the required system security settings and click OK to return to the Device owner blade; |
| 4 | Back on the Device owner blade, click OK to return to the Create Policy; |
| 5 | Back on the Create Policy blade, click Create to create the policy. |
Note: To take full advantage of this device compliance policy configuration, it must be used in combination with a conditional access policy that requires the device to be marked as compliant.
End-user experience
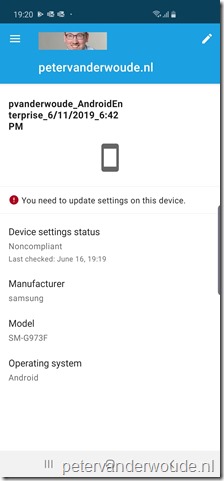
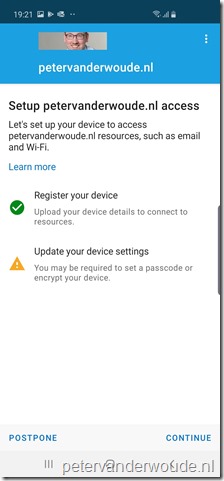
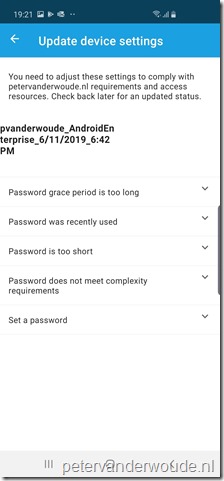
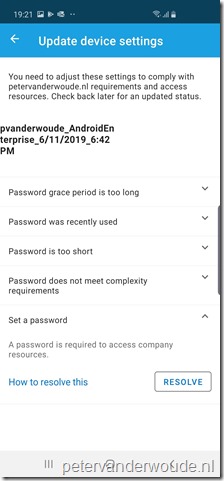
Now let’s end this post by looking at the end-user experience. Below, from left to right, is an overview of the different steps in the Microsoft Intune app to get a device from a noncompliant state to a compliant state. When the user has a noncompliant device state, the user can start the process by clicking on “You need to update settings on this device”. That will bring the user to the screen to setup access to resources. On that screen the user can simply continue. The next screen will show the user the settings that need to be updated and by clicking on a setting the user will receive information to resolve the issue. Once all the issues are resolved, the device state will switch to compliant.
 |
 |
 |
 |
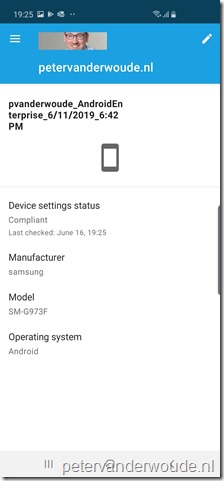 |
Note: Keep in mind that this is still preview functionality. When using app protection policies, the protected apps will still prompt for the installation of the Intune Company Portal app.
More information
For more information regarding the Microsoft Intune app and Android Enterprise fully managed devices, please refer to the following articles:
- Microsoft Intune announces Preview 2 for Android Enterprise fully managed devices: https://techcommunity.microsoft.com/t5/Intune-Customer-Success/Microsoft-Intune-announces-Preview-2-for-Android-Enterprise/ba-p/472324
- Set up Intune enrollment of Android Enterprise fully managed devices (Preview): https://docs.microsoft.com/en-us/intune/android-fully-managed-enroll
- Enroll your Android Enterprise dedicated devices or fully managed devices (Preview): https://docs.microsoft.com/en-us/intune/android-dedicated-devices-fully-managed-enroll
- Android Enterprise settings to mark devices as compliant or not compliant using Intune: https://docs.microsoft.com/en-us/intune/compliance-policy-create-android-for-work

The devices fail to register (“Register your device”) with a pop-up from the Android Device Policy like: “Cannot perform this action. You don’t have permissions”. The device is actually correctly registeren in AAD and configuration and compliance policies are applied. Any ideas?
Hi Hans,
Is the device also successfully enrolled into Intune?
Regards, Peter
Yes, it is. And it can be managed from Intune. It’s just that registering the device from within the Intune app fails.
Hi Hans,
Are you using the Company Portal app or the actual Microsoft Intune app.
Regards, Peter
The actual Intune app.
Hi Hans,
In that case, as I’ve covered the basics, it’s really hard for me to judge the scenario like this. Also, do keep in mind that it’s still preview functionality. My suggestion would be to create a support case.
Regards, Peter
Hi Hans,
That is a policy issue. Make sure that in the Device Restrictions profile for Android Enterprise, under Users and Accounts, the option Account Changes is set to Not Configured. If it is set to Block registration will fail.
Geert-Jan
Great, that is the solution. Thank you!
Hello Peter,
We are using android enterprise fully managed devices in combination with Samsung Knox. We have some devices we don’t need anymore and like to sell. Before we can do that we obviously want to remove the management part from the device. We deleted the device in the samsung knox portal succesfully. We noticed in Intune there is no device list like with autopilot for Windows. After resetting the android device it’s still being enrolled though, do you have any idea where we have to delete this device so it’s not being auto enrolled anymore?
Nevermind my last comment, even though the samsung portal said it deleted the device for some reason it was added again.
Deleted it again and it seems to work now.
Glad it’s working and thank you for the update, Mark!
Hi, I am trying to find out if it is absolutely necessary to use dynamic device groups for enrolment. I like the idea and would prefer to use them however pins are not enforced during enrolment but is left to the user post enrolment which to me defeats the whole purpose of fully managed devices. If I use user assigned groups everything is done during enrolment perfectly. Are there any risks or consequences of using user assigned groups for example if people have the company portal on their personal device would being in that group change anything. I have 1000 android devices to go into production and this a major concern. Would this also mean the enrolment profile would not be needed and qr code would be default?
Hi David,
Could it be that the dynamic group isn’t updating fast enough? Often filters provide a (much) better experience. When targeting settings to users, only settings that are applicable to the enrollment scenario of the user, will be applied.
Regards, Peter