To end this year in the cloud, I would like to devote this weeks post to allowing systems access to cloud distribution points. A bit more then two months ago I already did a post about creating a cloud distribution point, but until now I’ve never posted anything about the client configuration. By default, a system is not allowed access to cloud distribution points.
Prerequisites
Before it’s even useful to allow a system access to a cloud distribution point, the system needs to be able to resolve the name of the cloud distribution point. There are two ways to achieve this:
- The proper way – Create a public CNAME –record to map the service name, provided with the certificate for the cloud service, to the Windows Azure service FQDN.
- The dirty way – Create a private HOST –record to directly map the the service name, provided with the certificate for the cloud service, to the IP address of the Windows Azure service FQDN (only for testing!).
Configuration
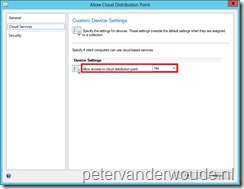 Now lets start with the configuration, which is actually very easy. Like almost all the previous times, this year, it’s all about knowing that the possibility exists. The configuration is another new Client Setting in ConfigMgr 2012 SP1, named Allow access to cloud distribution point. This setting can be used to control access to cloud distribution points. To configure this, for specific systems, follow the next steps:
Now lets start with the configuration, which is actually very easy. Like almost all the previous times, this year, it’s all about knowing that the possibility exists. The configuration is another new Client Setting in ConfigMgr 2012 SP1, named Allow access to cloud distribution point. This setting can be used to control access to cloud distribution points. To configure this, for specific systems, follow the next steps:
- In the Configuration Manager Console navigate to Administration > Overview > Client Settings.
- On the Home tab, in the Create group, select Create Custom Client Device Settings and the Create Custom Client Device Settings –popup will show.
- On the General page, fill in with Name <aName> and select Cloud Services.
- On the Cloud Services page, select next to Allow access to cloud distribution point Yes and click Ok.
- Select the new policy <aName> and on the Home tab, in the Client Settings group, select Deploy.
- Select <aDeviceCollection> and click Ok.
Result
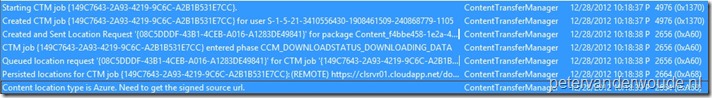
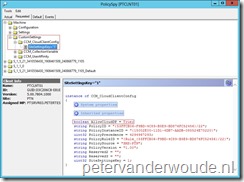 As always, now it’s time to take a look at the result. In this case I want to show two things, first the result, and second the impact, of the deployment of the new Client Settings. Normally, the best places to look at the results are the log files. In this case, there is no log file that shows whether cloud distribution points are allowed, or not. So the best place to look at that is the old-school Policy Spy. It will show AllowCloudDP = True as a custom setting under, in this case, Machine \ CustomSettings.
As always, now it’s time to take a look at the result. In this case I want to show two things, first the result, and second the impact, of the deployment of the new Client Settings. Normally, the best places to look at the results are the log files. In this case, there is no log file that shows whether cloud distribution points are allowed, or not. So the best place to look at that is the old-school Policy Spy. It will show AllowCloudDP = True as a custom setting under, in this case, Machine \ CustomSettings.
To look at the impact, the best places are still the log files. There are lot’s of log files that will show the usage of the cloud distribution points. A cool log file to look at the different blobs that are used during the download is the DataTransferService.log. The log file that I will show under here is the ContentTransferManager.log. In here it will also show the cloud distribution point, including the message that the Content location type is Azure.